How the ‘NYT’ swallowed the Stuxnet worm
By Mondoweiss
By Rehmat Qadir
On January 16, The New York Times ran a front-page story by William Broad, John Markoff, and David Sanger entitled “Israeli Test on Worm Called Crucial in Iran Nuclear Delay,” supposedly unveiling the joint US/Israeli role in creating and testing the now-famous Stuxnet computer virus reportedly employed against Iran’s nuclear program. According to the article, this piece of malware is responsible for setting back Iran’s nuclear program by possibly years.
The reaction in the blogosphere and news media following has been one of widespread awestruck acclaim, with various outlets referring to the advent of Stuxnet as an “Oppenheimer moment”, “the Hiroshima of our time” along with slews of hypothetical analyses of the world-changing implications of such technology.
I was astonished at the near-total acceptance of the claims laid out by the NY Times article. At first impression, the major themes of the commentary on Stuxnet sounded like science fiction and propaganda, and upon examination of the article, many, many questions arose in my head. I do not doubt the existence of Stuxnet, nor the revelation that Iran was indeed the intended target of the malware distributed globally; high officials of the Iranian government, including Ahmadinejad himself, have conceded in recent months at least some damage caused by the attack. However, the scope and scale and level of success of the Stuxnet virus implied by the coverage of the NY Times story warrant far more scrutiny than they have up to now received.
I was curious enough to start digging. What I’ve found leaves it very difficult to believe that The New York Times correspondents, following the culmination of a three-month investigative process, could have been unaware of the massive volume of publicly-available data that undermine the reporting they offered. Even more interesting, most of that contrary information is included inside the very same reports The New York Times cites in its evidence for its claims. What I have found follows:
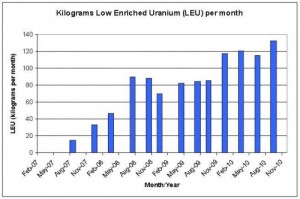
The New York Times article is deliberately misleading, excluding publicly-available evidence that casts doubts on the facts presented within it. Chiefly it has excluded the likelihood that the Stuxnet operation was a failed or only minimally-successful experiment that did next to nothing in terms of setting back Iran’s nuclear program, as demonstrated by Stuxnet’s inconsequential effect on the production of low-enriched uranium– an effect documented in the graph below from the very report that The New York Times cites as the authoritative record for the timeline it puts forward, but a graph it failed to report to readers.
Furthermore, technical analysis of the actual virus code shows a series of software revisions in 2010, long after the 2009 period of damage the authors assert was effected by Stuxnet– implying much less confidence in the success of the virus on the part of its developers, a conclusion again supported by quantitative data illustrating rising Iranian output of low enriched uranium over the past four years. And this conclusion is borne out by recent analyses of the software that once again the Times failed to mention.
I can only speculate on the motives of the authors in writing the piece, but here are the points that are making me twitch:
The article is almost completely unsourced, without names attributed to assertions of fact, with a few exceptions, which I’ll expand upon below and which only cast doubt upon the veracity of the story being reported. In the piece the authors claim that it was based on interviews conducted by The New York Times over the past three months, but aside from a few opinions from academic types and security experts, there is no source cited for the chronology of events in the piece aside from a section dealing with the AQ Khan nuclear network and Israel’s nuclear program in the 1970s–which is irrelevant to the major claims made by the article relating to Stuxnet and its development, testing and subsequent deployment against the Iranian uranium enrichment site at Natanz.
The piece begins its timeline with the German company Siemens, producer of tons of industrial equipment, cooperating since 2008 or so with the US government in experiments to supposedly identify weak points in the control systems for the various products they sell. That time frame raises questions.
The article asserts that the cooperation between Siemens and the Idaho National Laboratory began at some point in 2008, and cites as evidence of this cooperation a link to a PowerPoint document presented at a security conference held in July of that year with Siemens and INL as participants detailing various vulnerabilities found in the software used to run industrial control systems such as water plants, power grids, etc, over the past few years leading up to the conference.
A paragraph or two later the authors cite to corroborate their narrative some Wikileaks releases: State Department cables from April 2009 about efforts to interdict shipments of industrial equipment, manufactured by Siemens, to Iran. The article continues in the next sentence to say that the Emirates assisted in blocking a similar shipment of Siemens computers to Iran, seemingly around the same time.
Given the premise of the article– recent setbacks in Iran’s uranium enrichment program were the work of the United States and Israel employing a computer virus– interrupting hardware shipments would seem to make little sense. If, indeed the work on the Stuxnet virus and the related research into vulnerabilities in software and computers managing the workings of massive industrial infrastructure were, as the article implies, undertaken in an effort to create some kind of supervirus capable of sabotaging Iran’s nuclear plant, why would the article’s heroes want to block such shipments? If, as Markoff, Broad and Sanger forcefully suggest, Stuxnet was designed as a means of disabling enemy infrastructure remotely, or at least sabotaging it, what could possibly explain the efforts to prevent “poisoned”, or weak, easily exploitable hardware and software from reaching Iran? Wouldn’t this be exactly the make of equipment they’d want to reach that country, one they had been developing a secret killswitch for– rather than comparable technology purchased from elsewhere on the world market?
If the Times is right, and Stuxnet was designed/tested by the US/Israel, and was actually intended as a means of sabotaging the facilities at Natanz and elsewhere, the only possibilities I can think of to explain the effort at preventing this equipment from reaching Iran were a) perhaps the Stuxnet project/research wasn’t far enough along in 2009, not yet operable as a means to cause any setbacks to the enrichment program; b) it did not actually exist at all at the time the shipments took place, or c) the timeline has been carefully edited to be a self-serving fairy tale, speculating on/claiming causation for a series of unrelated events, and perhaps taking credit for them, or exaggerating their significance.
The New York Times’ timeline is so hazy– and so at odds with the chronologies contained in public reports the NYT points to as its own sources– that I conclude the article is deliberately vague.
Here is The New York Times timeline:
2008: Cooperation begins between Siemens and Idaho National Lab.
April 2009: Wikileaks cables dated detailing efforts by the United States to block shipments of Siemens industrial equipment.
June 2009: Stuxnet is discovered.
Late 2009: Centrifuges are revealed to have been destroyed by the IAEA due to unknown circumstances.
Broad, Markoff, and Sanger offer June 2009 as the date of the discovery of the Stuxnet virus with no source cited for the claim, not even an “unnamed official” (the go-to source for these reporters in their work, particularly Broad and Sanger), a news report, or any other document. This is a significant claim because the malware now described as Stuxnet was first revealed to the world on June 14, 2010 by VirusBlokAda– the Belorussian security firm most widely credited with discovering the worm–according to the consensus of VirusBlokAda, ESET, Symantec, Kapersky Research Labs, and, most tellingly, The New York Times’ own earlier story in November 2010 that accepted this consensus. This consensus described an infection that suddenly popped up on tens of thousands of computers worldwide, with 60% of these based in Iran, followed in numbers by Indonesia and India. In July 2010, Symantec followed VirusBlokAda with its own detection of Stuxnet. And Microsoft issued warnings regarding the vulnerability of Windows to Stuxnet on July 16, and two weeks later, in August 2010, issued a security patch plugging the discovered vulnerabilities in its Operating System to the virus.
Following the definitive discovery in June 2010, Symantec and ESET released dossiers on the Stuxnet worm stating that isolated variants of the worm did indeed, appear in 2009, and were retrospectively determined to be earlier variants of Stuxnet. But these papers provide further details that cast doubt over the NYT’s timeline: they state that components of the Stuxnet code were in fact developed in 2009 and subsequently revised throughout 2010 (evidenced by timestamps discovered within code sections). Possibly these references were the cause for the The New York Times setting of June 2009 as the time of the virus’ initial discovery? But if this ambiguity constitutes the evidence for the NYT’s purported discovery date, the exclusion of the overwhelming volume of technical documentation and news reports putting that date in 2010 should at the minimum have invited further scrutiny of the article from media critics discussing the piece, such as Robert Dreyfuss and Eric Alterman of The Nation, both of whom seem to have missed the contradiction in discovery dates (and more importantly, its almost complete lack of citations, which you’d think media critics would notice right away).
Later in the Times article, perhaps the most fascinating claim about Stuxnet’s efficacy in setting back Iran’s nuclear program in the entire piece is made:
“[O]ne small section of the code appears designed to send commands to 984 machines linked together [out of 8000 centrifuges in total].
Curiously, when international inspectors visited Natanz in late 2009, they found that the Iranians had taken out of service a total of exactly 984 machines that had been running the previous summer.”
The article attributes the 984 coincidence to a German security analyst, Ralph Langner, writing up the workings of Stuxnet (Langner first published in Fall 2010 and subsequently revised and summarized just a few weeks ago here) and the conclusions of those international inspectors, employees of the IAEA, the UN nuclear agency tasked with enforcement of the Non-Proliferation Treaty, in late 2009.
The IAEA publishes quarterly reports, available in the public domain, regarding their continued inspections of Iran’s nuclear facilities. I have searched through the reports of the IAEA from that period and have found nothing so far matching this claim. Perhaps there do exist additional documents or sources produced by the agency that the journalists draw this information from that are as of yet not publicly available. But in the NY Times piece, the findings of “international inspectors” are given the credit for this figure; and the findings of those international inspectors from around the period of late 2009 are here:
IAEA Board Report – February 2010
IAEA Board Report – November 2009
IAEA Board Report – August 2009
None of these documents contain figures that corroborate the 984 coincidence.
Oh, but several paragraphs later, the NY Times article informs the reader that the actual source for the “984” figure are the findings of a report last month issued by the ISIS, the Institute for Science and International Security, a thinktank that touts itself as “a non-profit, non-partisan institution dedicated to informing the public about science and policy issues affecting international security”.
This is where things become extremely confusing.
For the Times authority Ralph Langner also relied on ISIS. As I said, the Times credits Ralph Langner for the “984” discovery. Langner’s claim is here, a blog post published by the researcher dated December 29, 2010. Here is Langner’s description of the “attack code”:
“FC [Function Call] 6068 is called from FC 6070 six times, passing values from 1 to 6. Funny enough, 164 centrifuges are in one IR-1 cascade. Six cascades translate to 984 centrifuges.
Now go back to the ISIS report. The number of damaged cascades is six. That’s how you arrive at the “about 1,000 centrifuges”. The exact number is 984. Bottom line: We bet a gefilte fish that the damaged centrifuges were attached to one infected 417.”
Langner has seized on as a suspicious coincidence between the actual Stuxnet code and the ISIS report, which was based on IAEA documents. But this coincidence is misleadingly presented by The New York Times not as a bet on a gefilte fish, but as some kind of smoking gun. The ISIS report on which Langner bases this connection, and which The New York Times later in its article also cites, states the following:
“The February 18, 2010 IAEA safeguards report on Iran indicates that centrifuges in 11 of the 18 cascades in module A26 were disconnected, and these cascades were by implication no longer under vacuum. A module contained a total of 2,952 IR-1 centrifuges in 18 cascades; these 11 cascades contained 1,804 IR-1 centrifuges. Six cascades in module A26 continued to be fed with uranium hexafluoride. All but one cascade in module A24 continued to be listed as enriching uranium. In addition, cascades in module A28 were not under vacuum or being fed uranium hexafluoride, but centrifuges in two cascades were being removed.”
The math in the ISIS analysis leaves a wide range of ambiguity, which is extremely interesting considering the NY Times article asserts that exact figure for disabled centrifuges, with no margin of error: 984. As Broad, Markoff, and Sanger purport, and Langner on his website purport, this conforms to a line of code in Stuxnet specifying the number of centrifuges to be disabled by the virus: 984.
Let me summarize the actual numbers in the ISIS report:
–Within the data set of affected cascades there are 3 Modules.
–1 Module = 18 Cascades
–1 Cascade = 164 Centrifuges.
–Thus, 1 Module = 2952 Centrifuges.
–The sum total of the centrifuges housed by the 3 referenced modules (functioning at 100% capacity) is 3 X 2952, or 8852 centrifuges.
–For the first module, A26, 11 of the 18 cascades were disconnected, presumably due to device failure. This would translate to 1804 centrifuges destroyed or otherwise out of service for this one device. Then the piece notes that only 6 cascades remained intact, leaving only 984 online, in cascade A26, not the 984 destroyed according to Langner.
–For the module A24, one cascade is inoperable. This accounts for an additional 164 centrifuges inoperable.
–And finally, for module A28, 2 cascades were “being removed”. This would translate to a further 328 inoperable centrifuges.
These figures add up to a total figure of 2296 destroyed, removed, or otherwise unuseable centrifuges. This does not come close to the conclusions drawn by Langner, or the New York Times based on the data extrapolated by ISIS from IAEA reports. Even if only a single module, A26, were used as the data set for this conclusion, at the very least, by the standard assuming within each cascade that every centrifuge was destroyed, there would be at least 1804 wrecked centrifuges, not the 984 that either piece claims.
Of course, there is no way of sorting out the exact cause of failure for any of the individual devices. Other reports by ISIS, such as this one, detail other possibilities for centrifuge loss, in addition to Stuxnet, such as regular mechanical breakdown; inability to smuggle or reverse-engineer modern equipment: “Stuxnet is not the only candidate for explaining breakage and other problems. Iran may also have significant centrifuge manufacturing and assembly problems, including shortages of domestically-produced, high quality centrifuge parts. The enrichment plant has an elaborate computer control system which may have caused other problems.”
These possibilities are excluded from The New York Times piece, leaving an opening that makes it, I believe, at minimum, reasonable to question the level of success of Stuxnet had in setting back Iran’s enrichment capabilities, if we accept the timeframe of late 2009 as the period of the damage.
Returning to Langner’s post, further doubts are raised. What Langner’s blog post asserts with near certainty, unless this is a simple, uncorrected error, is that the Stuxnet code has been carefully designed to destroy exactly 984 centrifuges within a specific cluster of devices. As I said, astonishingly, the passage in the piece he himself cites for this yields this figure for the number of centrifuges remaining intact in just one of the modules. By examining the very document Langner cites as the evidence for his voila moment, it would seem that, only by examining just one of the three damaged modules reported on by the ISIS report can a reader arrive at the 984 figure he touts, and this number seems to designate the quantity of surviving centrifuges. I cannot possibly believe that this error in simple arithmetic was missed by Langner if his report was ever at all reviewed beyond a first draft. I can only speculate that Langner attempted to latch onto a numerical connection between his own analysis of the Stuxnet code and the estimations of the ISIS and clung onto this tenuous linkage out of laziness, or a lack of faith in a general audience to dispute the conclusions of an expert in an extremely technical field.
Assuming the best intentions in Langner’s connection here, that what he meant to say was that the code was designed to actually leave intact 984 centrifuges in one of these groupings, further questions are raised. Why leave intact (or destroy) just a fraction of the purported 8000+ centrifuges spinning? Why not disable all of them, or at least try to? If it were indeed attempted by this virus to as comprehensively render inoperable the nuclear plant as possible, then it would seem that the virus was not very efficient, though technologically impressive nonetheless. If the cyberattack were not 100% successful, and only a portion of the devices were successfully sabotaged, then where exactly does this 984 figure highlighted by Markoff, Broad, and Sanger in their piece come from, aside from a pattern in the code, unconnected to the purported yield of its destruction? It seems implausible that it could come from the ISIS analysis, which mentions a vague figure of “around 1000” but whose actual assessment of ongoing damage seems to undermine this quantity. Or, it could simply be the unskeptical, echoing of Langner’s gotcha! moment due to the unwillingness of the reporters to test the veracity of the facts dangled before their eyes by difficult-to challenge scientific experts and pseudoscientific documents. The subject matter definitely has an aura of indecipherable technological wizardry, but this is no excuse for the authors of this piece to not scrutinize their own sources, either themselves or by interviewing other appropriately trained experts.
From what I can tell so far, the inclusion of the 984 “coincidence”, if it indeed can be considered such, seems like a retroactive boast taking credit for an achievement that could plausibly have failed, citing evidence the authors, and possibly Langner, have faith the public will never bother to examine for themselves.
Let me move on to another major weakness in the Times’ piece.
Both the Symantec and ESET dossiers put forward that the technology described in the press as Stuxnet is not one powerful innovation of software, and has in fact been several deployments of modifications to an original worm. Both papers, as well as Langner’s analysis, explain that Stuxnet was designed with the capability to receive code updates from a distant server under the control of the virus’ handlers/authors.
And this characteristic of the worm only deepens the mystery.
According to these reports and tech news coverage, a feature of Stuxnet which astounded security researchers upon the virus’ discovery worldwide was its use of signed driver certificates, a means of authenticating the safety of installed software within Windows by utilizing a commercial “signature” to conceal the presence of the malware within the operating system. Valid signatures are provided by “trusted” and legitimate software developers, and the presence of these signature certificates proves the “reliability”, so to speak, of the software introduced to Windows, which then enables its installation. Use of this technique allowed Stuxnet to evade detection as malware to these computers by incorporating the signatures of legitimate commercial software. Apparently, the Stuxnet analyzed by researchers included two separate signed certificates by Taiwan-based software developers: Realtek and JMicron.
The first certificate discovered, that of Realtek, was determined to have been dated and compiled (activated) January 25, 2010. This would mark the start of the period of this component of the software’s “validity”, which would allow it to work within Windows. Already, this date does not gel with the timeline of Stuxnet’s efficacy, if we accept The New York Times’ claim of late 2009 as the period of centrifuge destruction attributable to the virus. Furthermore, the Symantec dossier notes that the Realtek certificate expired on June 10, 2010, at which point Windows would no longer trust the software, and its ability to replicate within new machines undetected would also end. This date is borne out by the discovery of Stuxnet that spring by VirusBlokAda and its announcement on June 17, 2010– an infection which suddenly popped up on tens of thousands of computers worldwide, with 60% of these based in Iran, followed in numbers by Indonesia and India.
The two security reports state that an additional security certificate, that of JMicron’s, was activated on July 14, 2010. The authenticity of this additional certificate was revoked (hence expired) within days on July 17, 2010.
Of course these timestamp dates are much later than the period of purported centrifuge destruction in late 2009 offered by The New York Times.
But the usage of the signed driver certificate is, for me, at least, the strangest part of this story of all. The employment of this method to bypass security features on Windows seems impressive on first look, but I cannot, for the life of me, understand the inclusion within Stuxnet of the Realtek signature’s seemingly deliberate expiration date. For Stuxnet appears to have been designed with a built-in termination date (June 10, 2010), one that would enable a five month period of use before the inevitable expiration of the signature, at which point the virus would become visible to Windows. Given the political stakes and logistics involved, and very definite possibility of discovery using this method, this expiration date seems laughably self-defeating. And accordingly, the expiration is corroborated by the sudden widespread discovery of the worm on tens of thousands of computers throughout the world by VirusBlokAda on June 17th.
Again, within days warning were issued, and software patches and remedies were issued by Microsoft and antivirus companies within days. And it seems that the attempt was repeated with the inclusion of the JMicron certificate timestamped on July 14. For me, it is difficult to entertain the possibility that such forseeable results were accidental, and twice. If the method was not risky and ineffectual before, it would be exponentially more brain-dead to attempt it again, but that seems to be what was done.
What seems at the very least plausible is that rather than employ the use of signed drivers to help conceal the presence of the virus within Windows, the inclusion of this feature was designed to reveal it– was designed to publicize its existence for political means, its insertion a clever poison pill not meant to mask its presence within infected computers, but rather ensure its inevitable detection and announcement to the world.
Returning to the reported late 2009 damage to equipment in Natanz, what I think is plausible, and what I believe the motivation of the spokesperson or administration official(s) who fed the tale to Sanger et al. is that the code being studied and called Stuxnet reflects a repeated effort to publicize a prior failed operation. If not to ensure the worm’s detection, the inclusion of the second signed driver certificate in July after the discovery of the virus seems to strengthen the notion that deployments of the malware had had very limited success, and so had to be continually recalculated and reconfigured to make up for the earlier near non-existent results– or, more devilishly, to publicize the worm and attempt to give credit to it, as the Times duly provided credit.
Because let us not forget: Whatever the exact time period of the damage done by Stuxnet, the same ISIS reports cited by The New York Times as their evidence provide the graph at the top of this piece for output levels of low-enriched uranium since 2007. (See the above graph once more.) With very few hitches, the Iranian program continues to increase its capacity, illustrating that Stuxnet has barely made a dent in the production of LEU. Again, this information is left out and doubtless, intentionally, unless New York Times reporters reached their positions at the world’s leading newspaper by reading only the first few paragraphs of their own source material. ISIS does offer comically vacuous lines of analysis to explain its own inability to demonstrate the damage done:
“Any effect is camouflaged since the rate of low enriched uranium (LEU) production increased significantly during the three month reporting period between November 2009 and February 2010. This gain was sustained in the months afterwards.”
The ISIS report is responsible enough to offer that Stuxnet’s introduction to Natanz could indeed be inconsequential, and the second half of the paper goes ahead to explain ISIS’s own doubts, providing numerical data that does not support the ISIS report’s own thesis.
Strangely, and irresponsibly, The New York Times did not find room in its own piece to mention these, nor examine the report’s provided quantitative data that undermine the premise of the ISIS paper’s own headline.
Beyond this, the NY Times piece’s authors’ inclusion of the qualitative speculations (rather than quantitative data) of the ISIS report, and not the direct findings of the IAEA for supposed technological figures and political assessments of the Iranian nuclear program, seems to be an unnatural choice, if accuracy were their mission. Having sifted through these ISIS papers, which are much more alarmist and hawkish, so to speak, than the quarterly reports of the IAEA (the UN source of the ISIS analyses), I would note that the IAEA continues to verify the non-diversion of nuclear materials from declared sites under IAEA safeguards, and Iran’s ongoing non-violation of the Non-Proliferation Treaty. The IAEA reports, in their conclusions, do raise concerns about Iran’s cooperation in adhering to the Additional Protocol demanded by the UN Security Council, but not the substance of the Non-Proliferation Treaty, the agreement it remains a signatory to– unlike those other regional nuclear powers, India, Pakistan, and Israel. None of the source IAEA reports provide the centrifuge figures used by ISIS, the ones subsequently cited by Langner and ultimately The New York Times. These breakdowns are instead extrapolated by the ISIS from the vague, raw, and much more politically neutral findings of the IAEA reports. Also, in literally every document produced by the ISIS there is a presumption of a covert Iranian nuclear weaponization program that is not shared by the IAEA– which I suppose would make the use of these primary documents, rather than the secondary commentary provided by the ISIS, less than ideal for The New York Times in crafting a war narrative.
By the way, the ISIS has offered the possibility of Stuxnet being responsible for setbacks in LEU production levels with more than one timeframe. In an earlier piece of theirs, dated November 27, 2010, they offer another speculation for possible Stuxnet damage, one of fall 2010. Again, the graphs do not corroborate any kind of setback and in fact illustrate the largest gain in output of LEU from August to November 2010. Readers should be aware of long-standing criticism of the founder and director of ISIS, David Albright by other writers on non-proliferation issues like Scott Ritter and Muhammad Sahimi, who basically write him off as sort of an obsequious number-cruncher, who in their opinion works to provide scientific cover for presidential administrations to bomb other countries dating to the period of the first Gulf War. Readers can gauge the credibility of their criticisms of Albright and the thinktank that is his brainchild here and here. The New York Times is certainly aware of these criticisms of ISIS, but strangely chooses to present its findings without comment.
What was the point of the New York Times article at all, aside from the obvious entertainment value? Certainly co-author David Sanger has a rep as being one of the primary conduits for and conjurers of war propaganda in making the case for an attack on Iran– similar to the role Michael Gordon played in the lead up to Iraq, largely by presenting unsourced and unverified claims from unnamed officials about threats posed by enemy states.
But while you might think that Sanger has the desire to sell a possible war with Iran to the general public, this story seems to undermine the possibility of such a war, if, as the article claims, the Iranian nuclear program has been set back years as a result of Stuxnet. It seems to put the brakes on a narrative that has been animating nearly all Sanger’s reporting for the past four years, and I’ve found myself puzzled again trying to discern the article’s political intent. Could this article be a signal by someone in the Obama administration that a war is not coming anytime soon? It seems to at least be a possiblity that the Stuxnet story could indeed present an opportunity to cover a retreat from that option with a claim of success that, as some pro-Israeli sources have suggested, is the equivalent of a military attack.
I am suggesting that the article is a form of damage control related to the recent statements by Meir Dagan that Iran no longer poses an imminent threat. I can think of other motives: an attempt to claim credit by the US/Israel for the work of unknown cyberassailants, an attempt to save face for a failed, unfocused operation. Interestingly, Ralph Langner himself has suggested multiple possible culprits for the attack in addition to the United States and Israel, including Russia, China, and Germany. Again, though, and irresponsibly, The New York Times excluded all these culprits even though it uses Langner’s work to buttress its most important technical details.
My conclusion is that the authors’ purpose was simply to craft a fantastic and fawning patriotic narrative, overstating joint American and Israeli power in light of less than stellar results, a caricaturized timeline to suggest a much longer and greater degree of sophistication, planning and strategic capacity in the Stuxnet effort than the actual chronology of events reveal, and a possible means of backing away from a war that may be off the table now, by writing up a self-congratulatory victory fable.
Yes, I am speculating. I cannot be 100 percent confident about that conclusion. I hope that forthcoming events will illuminate the true intention behind this story’s publication.
(Thanks to Eli Clifton, Jim Lobe and Gareth Porter of IPS for their invaluable insights during the preparation of this piece.)
Qadir’s piece was written in late January and early February. He offers this addendum:
On February 11, Symantec published a revision to its Stuxnet dossier, confirming more or less my speculations above, by verifying the existence of multiple revisions and deployments of the virus. From examination of around 3300 strains of Stuxnet recovered from infected computers, the security firm determined that at least three variants of the same malware were deployed in June 2009, March 2010, and April 2010. Accordingly, ISIS has updated its December 22, 2010 report to include some of this information. Symantec and ISIS now report that the “417” controller attack sequence was inoperable and unfinished at the time of each of its deployments. Now it is impossible to continue to credit this part of the Stuxnet code with the late 2009 damage detailed by ISIS. The “417” controller attack sequence is the source for Langner’s and the ISIS’ earlier claim of 984 centrifuges damaged by the virus. Incredibly, ISIS continues in its update to claim “To date, Stuxnet is known to have had at least one successful attack. It is increasingly accepted that, in late 2009 or early 2010, Stuxnet destroyed about 1,000 IR-1 centrifuges out of about 9,000 deployed at the site.” But the new revelation completely contradicts this, and there is almost no case left for attributing the centrifuge damage in late 2009 to the specific section of Stuxnet code that was held up as evidence of enrichment setbacks cited by The New York Times. Albright himself almost completely slithers away from his earlier assessments in this February 16 article in the Washington Post. Perhaps other sections of the Stuxnet code were indeed responsible for this damage, but the case becomes more circumstantial as more information comes out. The New York Times went ahead and attributed causality, damage, and declared victory on the basis of extremely dubious evidence that can now be excluded from any assessment of Stuxnet’s utility.
Returning to the Symantec update, and its identification of three strains of Stuxnet up to March 2010, remember that the The New York Times gave June 2009 as the discovery date for the virus– when this date was somewhat ambiguously (and only retroactively) supported by the security firm’s published findings at the time of the article’s release. This leads me to suspect that this date was fed to the Times by another one of their unnamed sources, or chosen by them for the purpose of framing this narrative.
All of this focus on the design intent in Stuxnet and the corresponding damage distract from a much larger point here though, and probably the only thing to add with the discovery of these variants (and the revelation of the inoperability of the 417 attack sequence) is that the Iranian nuclear program continues unabated, and the publication of The New York Times piece could very well be a recognition of the program of ongoing uranium enrichment now as a fait-accomplit in the eyes of American/Israeli military programs. In drawing this conclusion, one only needs to refer to the above graph. Perhaps Stuxnet has, indeed, slowed the rate of acceleration of uranium enrichment capabilities, but output of LEU itself has only continued to grow as months pass. Would the rate have increased faster and more steeply sans Stuxnet? There is literally no way at all to quantify or prove this, whether arguing for or against the efficacy of the virus. The fact that the only possible period of quantifiable damage to Iranian nuclear equipment cited by the ISIS reports and The New York Times is in late 2009 seems to confirm the continuing impotency of the Stuxnet exercise.
