Redefining Neuroweapons: Emerging Capabilities In Neuroscience And Neurotechnology – Analysis
By NDU Press
By Joseph DeFranco, Diane DiEuliis, and James Giordano*
As global conflicts assume increasingly asymmetric and “gray zone” forms, the ability to employ current and newly developing techniques and tools of neurocognitive science to manipulate human thought and behavior must be viewed as a present and increasing challenge.1 Ongoing developments in neuroscience and technology (neuroS/T), which trend toward 5 to 10 year trajectories of progression, make the brain sciences valid, viable, and of growing value for operational use in warfare, intelligence, and national security (WINS) applications. Illustrative of this progress are a series of U.S. Government assessments of such capabilities. A 2008 report by the ad hoc Committee on Military and Intelligence Methodology for Emergent Neurophysiological and Cognitive/Neural Science Research in the Next Two Decades claimed that neuroS/T was not sufficiently mature to enable operational employment in WINS. However, a subsequent report by this same committee in 2014 noted that advancements enabled several domains of neuroS/T to be capable and operationalizable for WINS. This was substantiated by a number of nations’ increased interest in, and consideration and use of, neurocognitive methods and tools for military and intelligence purposes.2 Indeed, neuroS/T can be employed as both “soft” and “hard” weapons in competition with adversaries. In the former sense, neuroS/T research and development can be utilized to exercise socio-economic power in global markets, while in the latter sense, neuroS/T can be employed to augment friendly forces’ capabilities or to denigrate the cognitive, emotive, and/or behavioral abilities of hostiles. Furthermore, both “soft” and “hard” weaponized neuroS/T can be applied in kinetic or non-kinetic engagements to incur destructive and/or disruptive effects.3
Historically, biochemical weapons have included incapacitating or lethal agents such as nerve gas, irritants, vesicants, and paralytics. Numerous examples of such weapons can be drawn from World War I to the present. As shown in Table 1, various forms of neuroS/T have become available, and radical leveling and emerging developments in the brain sciences fortify and add to this current palette of weaponizable tools.
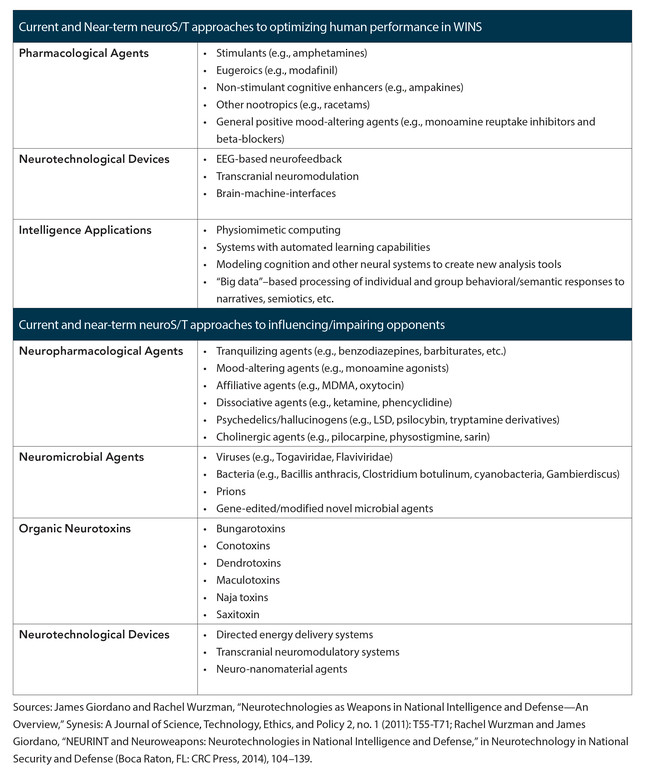
While many types of weaponizable neuroS/T (for example, chemicals, biological agents, and toxins) have been addressed in and by extant forums, treaties, conventions, and laws, other newer techniques and technologies have not.4 Thus, particular advances in neuroS/T have an increased potential for dual use and direct use in WINS. In this light, this article (1) presents the WINS utility and possible applicability of gene editing methods, nanoparticles, and other tools that can modify the central nervous system; (2) discusses the value and vulnerabilities of big data and bio-cybersecurity in WINS; (3) posits how such developments bring into stark relief existing gaps in international biological and chemical weapons conventions; and (4) proposes steps toward rectification of current and future oversight and governance.
Dual and Direct WINS Use Radical Leveling and Emerging NeuroS/T
Advancements in human genome sequencing, gene editing technologies, and other ancillary sciences (such as nanotechnology) have been instrumental to improving understanding and targeting of genetic mechanisms involved in several organisms’ structures and functions. In 1990, the United States initiated the Human Genome Project. By 2004, a draft had been completed of a significant sequence of the human genome.5 This knowledge was paired with the use of genome-wide association studies that can determine if any variation or mutation is associated with specific traits (for example, a disease or physiological function).6 Taken together with other genetic and genomic approaches, such emerging methods and tools have afforded the ability to identify and affect genes that are associated with or contribute to structure, functions, and abnormalities of the nervous system (that is, neurogenetics). This progress in neurogenetics has led to growing consideration of such assessments and modifications for use in WINS applications.7
Emerging Techniques Important for Neurogenetics
Gene editing (directly modifying an organism’s genetic material to achieve a desired effect and outcome) has been used for several decades. It has been intended and employed for treating a variety of conditions, including immunodeficiency and blood disorders and types of cancers. Gene editing methods were augmented by the discovery of certain nucleases (for example, zinc finger nuclease).8 However, despite some successes, difficulties with its design and application led to the development and use of simpler methods, most notably, clustered regularly interspaced short palindromic repeats (CRISPR) and the associated Cas9 nuclease.9 Such new, emerging, and relatively easy to obtain and use gene editing tools could be influential to the creation of novel neuroweapons.10 Of course, like any method, the uses of CRISPR/Cas systems have limitations. Yet these may not necessarily hinder their utility. In fact, such issues appear to be little more than proverbial “speed bumps” on the path to broadening capabilities afforded by CRISPR and related techniques.
It had been thought that the clinical use of CRISPR-type techniques represented a future possibility. However, a recent report on the administration of CRISPR-modified cells to human embryos in China (to generate an inherited resistance to HIV, smallpox, and cholera) has created a new timetable—and need for current guidelines—for human gene editing.11 To wit, in March 2019, the World Health Organization’s newly formed advisory committee for international governance on human genome editing declared such modifications to human germlines to be “irresponsible.”12 The committee proposed the need for a central registry of human genome editing research in order to facilitate more detailed insight to—and stringent oversight of—risks and hazards.
We agree with and support these actions. It is likely that the ability to modify existing microbes and other organisms will permit “side-stepping” the current Biological and Toxin Weapons Convention (BTWC) in the production of new bioweapons, and thus may necessitate revision of how such treaties categorize and identify agents that can pose risk and threats to global health and security.13 The recognition and acknowledgment that CRISPR methods could be used to generate novel biological weapons have also prompted studies of reversing CRISPR-induced effects. A recent article in the MIT Technology Review identified laboratories that are working to find “anti-CRISPR” molecules: proteins in nature that can “turn off” CRISPR-induced gene edits.14 Such endeavors reflect steps to control open source research and deter the use of gene editing to produce biological weapons or agents that otherwise negatively affect global health.
While these mitigative and preventive efforts are laudable, it should be noted that such regulation and attempts at restriction may not be encompassing or sufficient. In June 2019, a Russian scientist declared plans to implant gene-edited embryos into women.15 Clearly, this announcement came after the aforementioned appeals for international constraint of germline editing, thereby reinforcing the reality that CRISPR-based methods are relatively easy to develop and use but not necessarily easy to govern, monitor, and/or control.16 Of growing concern in this light are clandestine enterprises (biohacking) and research activities of nation-states, virtual nations, and/or nonstate actors that blatantly disregard international standards and guidelines.

Nanomaterials, NeuroS/T, and Bioweapons
Nanotechnology has been shown to be useful in controlling, guiding, and delivering molecules in biological systems to produce desired effects, and this has improved brain imaging and neuroactive drug delivery.17 As well, targeting molecules using nanotechnology has increased the possibility of genetically editing the brain.18 For example, nanolipoproteins (NLPs) mimic naturally occurring molecules and can be used to carry various biological substances (for example, nucleic acids, proteins, and other small compounds) to a desired location in the brain.19 Because these NLPs closely mimic molecules occurring naturally in humans, detecting their use (for example, in novel neuroweapons) would be difficult.20 Some proof of concept can be drawn from a 2019 study that used a mouse model to demonstrate the use of such nanotechnological stabilizing methods, the ability to transport modified molecules to the brain (that would otherwise not be possible), and to target and alter specific neural genes in the adult brain.21 Such methods could be used to genetically enhance neural structures and functions of their own personnel, as well as design novel agents that could degrade adversarial targets. Other applications of nanotechnology are enabling:
- insertion of very small-scale (nano) devices to remotely control organs and/or organisms
- modification of existing and/or creation of new neuropathogens (for example, nanoparticulate matter capable of exerting pathogenic effects in living organisms)
- enhanced delivery methods of drugs and/or toxins
- the disguise of organic molecules to avoid their detection.22
Nanotechnology is considered a relatively new science, and it remains unchecked by international treaties despite its viability and utility for various WINS applications.
Modified, non-infectious viruses have also been used as scaffolding to transport materials to edit genetic material.23 The lentiviruses (immunodeficiency viruses) have been favored because of their ability to integrate their genetic material (including any desired gene edits) to chromosomes of a variety of human cell types.24 This form of gene editing was used in a recent experiment that employed a modified Simian immunodeficiency virus to introduce the human MCPH1 gene (a major genetic factor in human brain evolution) into a non-human primate (a rhesus monkey).25 Following successful lentivirus-facilitated MCPH1 gene delivery, the monkeys showed decreased reaction times and enhanced short-term memory. Modifying the genome of non-human primates to make them more similar to humans may yield novel models for neurogenetic research and may speed the pace of translational research for human applications. However, we believe that it is important to question what types of neurogenetic research (for example, development of optimized functions and traits, modification of brain maturation or aging, resistance or susceptibility to particular pathogens) and toward what ends research findings, capabilities, and tools will be applied. In this regard, dual and direct WINS uses are not beyond the pale of possibility.26
Neurodata on the Molecular Level
Advances in both neurogenetic research and its applications are critically reliant on leveraging biological “big data” (“biodata”). Indeed, the digitization of biology is beginning to transform all of the life sciences, and automation of lab and medical procedures will manage and perform most tasks. The “digitization of biology” refers to the literal translation of the nucleotide codes of DNA to the binary structure (ones and zeros) of computer code. DNA sequences can now be databased and mined and, in these ways, enable computerized experimentation and/or design. Fully extrapolating information in digital contexts to meaningful biological study or the production of engineered organisms has additional dimensions and nuances. This leap from nucleotide data sequences recorded in databases, to forms and functions viable for biological predictions and product syntheses is known as abstraction.27 Valuable abstraction requires extensive genomic data analysis, using a complex set of computational tools, algorithms, and bioinformatics programs. If and when it is well articulated, the near future use of such high-quality abstraction could enable biological engineers to simply type in desired features for a biological protein/enzyme, or even an entire microbe, and receive those designs as outputs. In fact, such “computer-generated output” would not even require the engineer to have direct knowledge of the genetic sequences involved.
Still, the more complex the organism, the greater the computing and data storage power necessary. For example, one might readily be able to use open source software to engineer a soil microbe, but engineering human DNA in such ways might demand considerably more computational time on high-performance processors—at least at present. These challenges have fostered a host of international research enterprises aimed at opportunizing access to the human genome and iterative computational capability in ways that allow for rapid acquisition and translation of biodata to products, methods, and outcomes.
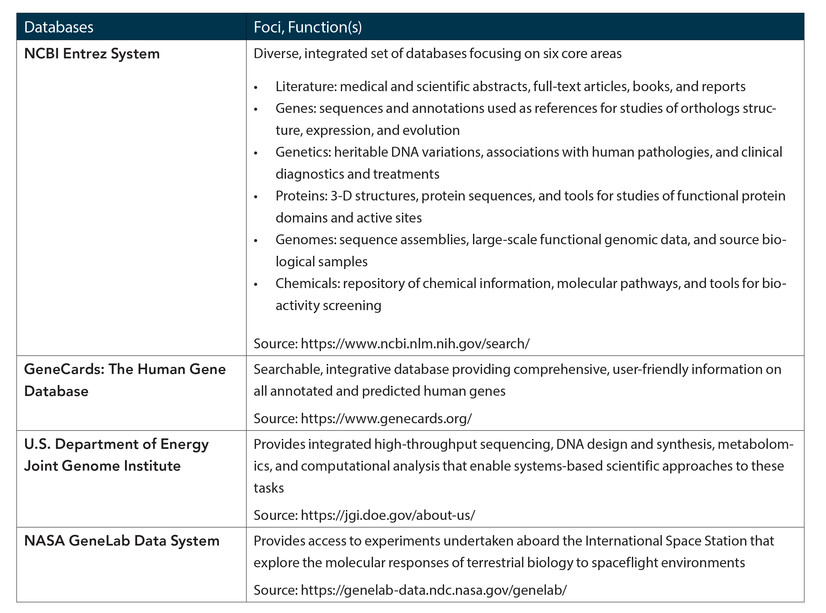
The U.S. National Center for Biotechnology Information website was created in 1998, and it remains one of the largest resources for biological information, being continuously updated by the U.S. National Institutes of Health, the DNA Data Bank of Japan, and the European Nucleotide Archive.28 This has prompted other agencies’/companies’ own efforts at DNA sequencing, and has enabled human and other genomes to be readily available (with other databases and/or tools) with unrestricted access (see Table 2). Recent attention has been focused on creating means of predicting and inhibiting the persistent problem of off-target mutations of gene editing (as seen for example, in the Chinese “CRISPR babies”).29 Computational algorithms have proven to be relatively affordable, quick, and useful means of assessing any potential off-target effects. Programs such as CRISPOR, CHOPCHOP, CRISPResso, Cas-Offinder, and Off-Spotter allow more accurate guidance of RNA design, acquisition, use of protospacer adjacent motif data, and facile adaptation of genetic modification techniques for use in desired organisms.30 Computational programs can be augmented by both in vitro genome analysis tools (such as CIRCLE-seq, SITE-seq, and others) and in vivo methods (VIVO, BLISS, etc.), which afford precision identification of both on- and off-target sites in specific cell types in an organism.31
Automation
Iterative automation is changing much of how bioscientific research is implemented. Machine systems are now able to execute a number of tasks that are routinely performed by humans, and in this way, machine systems can control many physical aspects of biological platforms and/or human-machine interfaces. For example, recent publications have described working robotic automation systems that reduce the time it takes to conduct synthetic biology experiments.32 Of note, a “digital-to-biological converter” has been described that can use digital DNA sequence information and produce DNA templates, RNA molecules, proteins, and viral particles.33 Furthermore, automated devices that monitor and/or control biological processes produce abundant data that can be shared and stored through cloud computing networks. As noted, the acquisition, use, and abstraction of such data require advanced computational software, algorithms, and bioinformatics. These processes also can be automated and have already proven to improve biological laboratory efficiency, and thus are beginning to be used more widely.34
As digitization and automation become more available, continue to advance, and are further integrated into various laboratories and medical centers, the procurement of and access to biodata will greatly simplify several dimensions and domains of biomedical research. Many countries have overtly—or more surreptitiously—begun to collect and utilize data to foster biotechnological innovation.35 Of particular note are efforts by China to collect vast quantities of genetic data in an initiative to construct a working database of its citizens.36 When fully operational, facilities in the city of Nanjing will sequence 400,000 to 500,000 samples per year and will be able to track individuals to obtain environmental and behavioral data.37 China’s cultural and political needs, values, and philosophies may establish ethico-legal parameters that allow extensive acquisition, access, and use of biological (and psycho-social) data in ways that are not viable in other countries. The concurrent collection of genetic and environmental/behavioral data can be essential to acquiring considerable knowledge about diverse aspects of human terrain.38 Per the adage that knowledge is power, this may expedite discovery and development of novel forms and capabilities of neuroS/T that can be employed to leverage strategically latent political effects worldwide.
With more laboratories and medical centers incorporating automation into their current systems, it is probable that a number of challenges and problems will be encountered and/or incurred.39 For instance, whole human genomic data (for example, as collected by companies like 23andMe, or Ancestry) are instrumental to creating and establishing a broader knowledge base (and palette of accessible information) about genes, inheritance, and dimensions of human intelligence, emotion, and actions. Recently described as “sociogenomics,” there is, of course, the possibility that this information (about an individual’s genotypic predilection for neurological disease, phenotypes, and/or behaviors) could be used to discriminate against or extort targeted individuals and/or groups.40 As well, the acquisition and use of such data could enable exploitation of particular genetic vulnerabilities to incur harm. Health records, health insurance profiles, or other clinical databases in which such information is housed have become vulnerable to direct cyberattacks on IT infrastructures.41
Risks of Neurodata
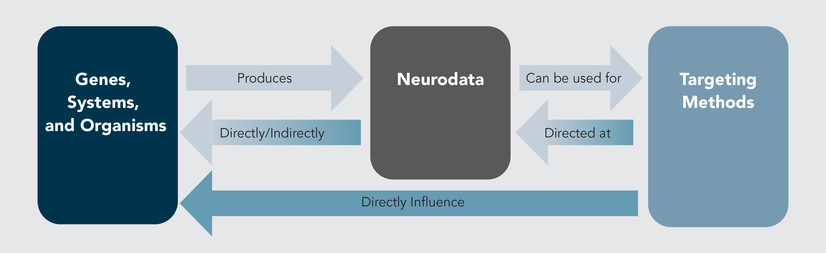
The intersecting vulnerabilities of computational systems and biological information are focal to the scope and activities of the emerging field of “cyberbiosecurity.” Jean Peccoud and colleagues define this discipline to entail (1) “understanding vulnerabilites to unwanted surveillance, intrusions, and . . . harmful activities which can occur at the interfaces of . . . medical sciences, cyber, cyber-physical . . . and infrastructure systems” and (2) “measures to prevent, protect, mitigate, investigate, and attribute such risks as it pertains to security, competitiveness, and resilience.”42 Previously we have analyzed the unique risks associated with biodata along a continuum of harms from individual privacy, to physical harm to individuals and groups—and we have highlighted the cyberbiosecurity risks specific to these domains.43 Here, we direct a similar examination by identifying the subset of biodata obtained from and operationalized within neuroS/T. We believe this subset represents a specialized landscape of vulnerabilities unlike any other in the cyberbiosecurity arena, as it could impact human mental health, cognitive states, emotional states, decisionmaking, and behavior. Such ability to coerce or otherwise control human beings via access to neurobiological manipulation is profound in both WINS and sociopolitical contexts. We envision two possible vectors of threat/harm: (1) the manipulation of neurodata in order to incur a direct/indirect effect on the way an individual or group is regarded and/or treated; and (2) the access and use of neurodata to design a precision effect on an individual or a group (see Figure 1).
Technological advances are expanding the type and variety of tools that can afford human-machine interfacing (HMI) for maintaining or improving health, and/or modifying (optimizing or negatively affecting) human neurocognitive and behavioral capabilities and performance.44 A timely example of this type of HMI is the Neuralink system proposed by Elon Musk as a minimally invasive intervention that could modulate selective brain networks and functions.45 The iterative development and utility of these devices are critically dependent upon the acquisition and use of diverse types and levels of data. These data, while force-multiplying the capabilities of neuroS/T, also render distinct risks in their relative susceptibility to hacking and manipulation.46 While tampering of any HMI is a cyberbiosecurity vulnerability, the capacity to access and control aspects of human cognition, emotion, and behavior incurs a special category of risk (see Figure 2). In these cases, cyberbiosecurity solutions will entail protection afforded to neurotechnological devices, and whether and how the information cued on such devices is accessed and shared by others.
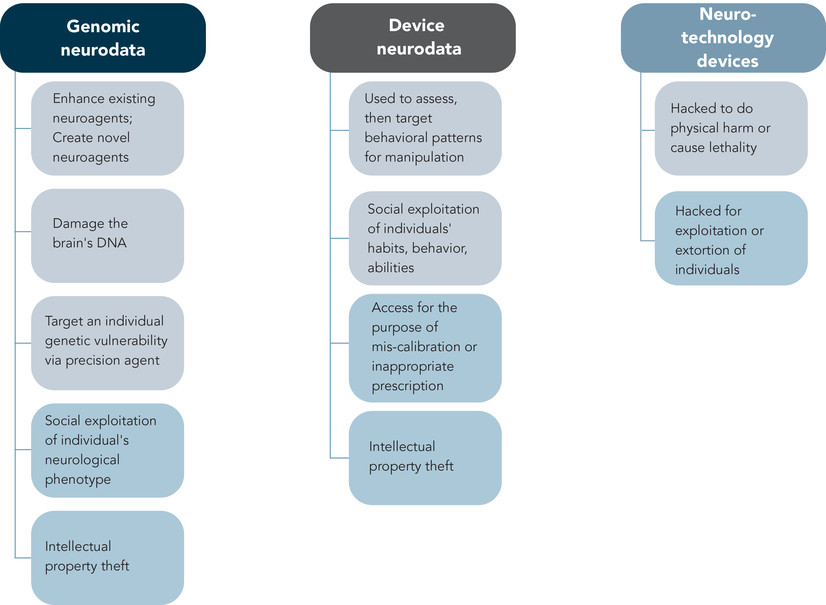
We consider these potential dual uses of neurodata to be a first but significant step in a pathway intended to produce neuropsychiatric threat and harm. Current treaties and conventions (for example, the Biological and Toxin Weapons Convention [BTWC] and Chemical Weapons Convention [CWC]) do not (yet) recognize, address, and hence govern the weaponized use of neurodata (or other biodata) and/or neuro-genetic modifiers.47 Thus, we believe and posit that it is important to acknowledge the role of—and need to protect and regulate—neurodata. Determination of who has access to these data and how access is provided should be considered and incorporated as fundamental components of any meaningful cyberbiosecurity solution on a relatively local scale. More broadly, such protections should be elements of future policy and governance in this realm.
Toward Regulations and Security
Regardless of current limitations, we believe that the BTWC and CWC can continue to be important mechanisms for international weapons control. The development, production, acquisition, retention, and/or stockpiling of defined neuro-microbiologicals, select chemicals, and toxins are prohibited by these two conventions. Yet these treaties are generally reactive and address biological and chemical weapons that have been used in the past. As well, the BTWC and CWC definitions of weapons were purposively intended to be vague in order to avoid constricted classification. This reactivity and system of classification do not account for (1) use of neurocognitive science (for example, neuropharmacological or neurotechnological augmentation) to optimize and enhance human performance in WINS operations; (2) development of novel pathogens via emerging technologies (for example, gene editing, nanoengineering, etc.); (3) the potential effect of ancillary techniques and technologies on existing biochemical agents; (4) specific neurotechnological devices that can be employed as weapons; and (5) the possibility of the human actor as a “biological agent.”48 Recent advancements and continued convergence of the brain sciences, genetics, neurotechnologies, and neurodata make the aforementioned possibilities rapidly realizable and urgent to consider and address.
Such risks and threats are greater as neuroscience becomes a more international enterprise and as nonstate actors and unregulated states acquire neuroS/T capabilities that can be used to achieve new balances of power. At their core, the viability and effectiveness of the BTWC and CWC are reliant on participatory states’ signature/ratification and acting in good faith. Without this standard, such agreements are relatively meaningless. Yet, the United Nations (UN) does not have statutes that make it mandatory to sign or ratify these conventions. Although UN Security Council Resolution 1540 (adopted in 2004) intended to target nonstate actors’ production and acquisition of weapons of mass destruction, it requires UN countries to modify their own legislation to exercise such controls. Enforcing the resolution is therefore dependent upon UN states’ proactive engagement and effectiveness, and thus fails to provide broad-based oversight and governance.49
Without proper surveillance and international cooperation, there is opportunity to bypass the BTWC, CWC, and other international regulations through (1) various types of commercial veiling strategies; (2) venture capitalist financing of “do-it-yourself”/biohacker scientists to conduct neuroS/T research for malevolent purposes; (3) research tourism that attracts scientists to undertake neuroS/T research and development in countries with capricious (or nefarious) agendas; (4) medical tourism, which encourages ethically problematic clinical practices; (5) defining a country’s research and use of weaponizable neuroS/T as “defensive” or for “intelligence” purposes; and (6) exploiting export codes of “dual-use” materials and technologies. Given these possibilities, we believe that it is increasingly important to analyze, quantify, and predict how the brain sciences can—and likely will—be developed and employed by foreign competitors and adversaries in both non-kinetic and kinetic ways.
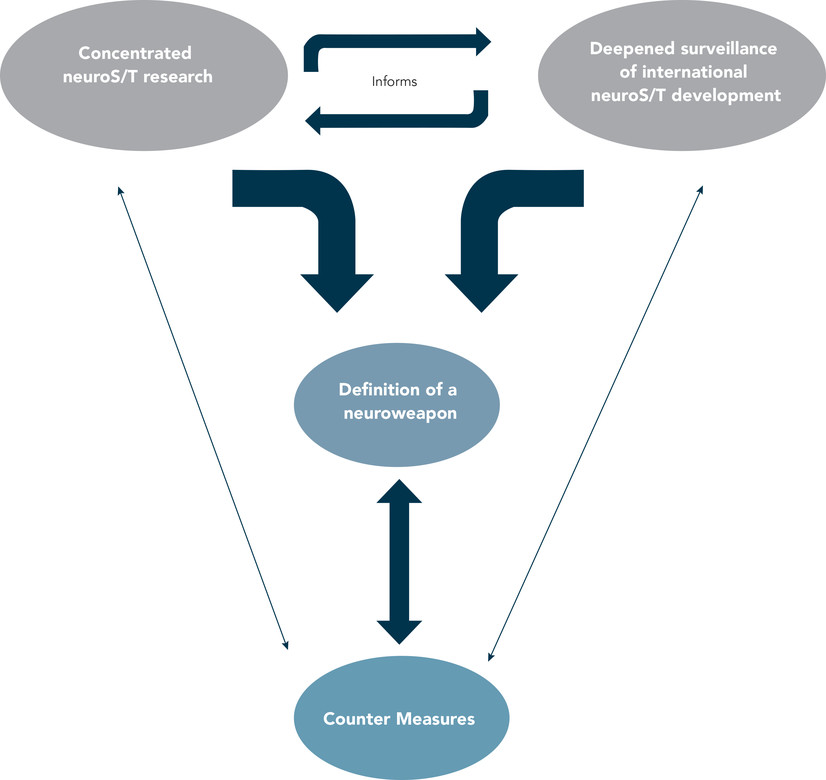
The current pace and scope of global neuroS/T research and development are indicative that this problem will only increase in years to come.50 The United States and its allies must acknowledge the risks that the brain sciences and ancillary technologies pose for potential applications in dual or direct uses for WINS purposes, and these developments and risks must be fully evaluated in order to establish and implement effective preparedness and countermeasures (see Figure 3). We see this as a multi-step process. First, the United States must engage extensive and focused research to better understand the current and near-term weaponization of neuroS/T. Several countries already have dual-use initiatives and/or military programs dedicated to neuroS/T, and not all are amenable or accessible to international surveillance and inspection.51 We opine that at present, there is a significant gap in the ability to forecast state-sponsored research and how nonstate actors could and will be able to harness extant neuroS/T for WINS applications.
To this point, we call for deeper and more granular surveillance of international neuroS/T research and use agendas. The European Union (EU) Dual-Use Coordination Group states that while approximately 20 percent of EU exports are “dual-use” goods, only 2.4 percent of those require export-license (the United States requires only 1 percent of “dual-use” goods to be authorized). A joint statement by the European Parliament, Council of the European Union, and the European Commission’s Dual-Use Regulation calls for “a high level of security and adequate transparency without impeding competitiveness and legitimate trade in dual-use items.”52 Toward these ends, assessing the scientific literature is an important step, as it could depict present and future research trends and afford means to monitor researchers who are knowledgeable, skilled, and able to exercise methods of creating neuroweapons. However, to appreciate the full scope of weaponizable neuroS/T, surveillance should focus on (1) activities of university and research sites; (2) the extent and directions of private and public support of research and development; (3) efforts toward recruitment of researchers; (4) neuroS/T commercialization; (5) current/future military postures; and (6) current/future neuroS/T markets and the potential for leveraging developments in this field for economic profit and global power.
International surveillance and research examining the ways that neuroS/T is being employed in WINS initiatives must be mutually supportive. Such reciprocity will be important to more accurately and efficiently (1) define which neuroS/T could have potential non-kinetic and/or kinetic capabilities; (2) understand present and future trends in research and development; and (3) identify specific research centers and personnel capable of—and involved in—creating neuroweapons (see Figure 3). We assert that the effective function of any competent, capable, and valuable biosecurity program requires two non–mutually exclusive factors. First is dedication to and flexibility in developing ongoing and revisable methods of identification, definition, classification, and regulation of current and emerging neuroweapons; and second is political support and sustained funding.
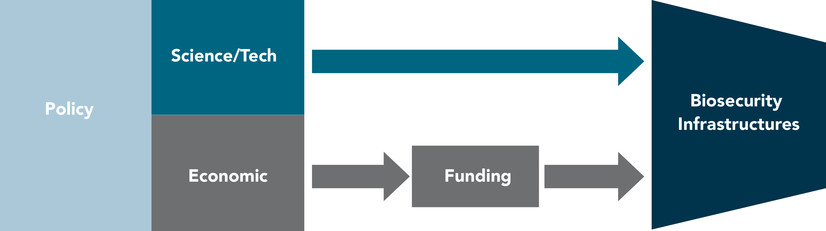
As shown in Figure 4, sound policies are important to the establishment, structure, and sustained functions of a biosecurity enterprise. Funding is essential to creating, maintaining, and expanding the resources, personnel, and activities of biosecurity infrastructures. However, policy is the means by which any funding is identified, appropriated, and allocated. Thus, ongoing efforts of surveillance, evaluation, and preparedness of science and technology mandate engagement and provisions of effort(s) to inform policy development and enforcement.
Acknowledgments
James Giordano’s work is supported in part by the Henry M. Jackson Foundation for the Advancement of Military Medicine; Leadership Initiatives; and federal funds UL1TR001409 from the National Center for Advancing Translational Sciences, National Institutes of Health, through the Clinical and Translational Science Awards Program, a trademark of the Department of Health and Human Services, part of the Roadmap Initiative, “Re-Engineering the Clinical Research Enterprise.” Diane DiEuliis acknowledges research support of the Center for the Study of Weapons of Mass Destruction, National Defense University.
About the authors: Mr. Joseph DeFranco is a Donavan Group fellow at U.S. Special Operations Command. Dr. Diane DiEuliis is a Senior Research Fellow at the Center for the Study of Weapons of Mass Destruction at the National Defense University. Dr. James Giordano is Professor in the Departments of Neurology and Biochemistry, Chief of the Neuroethics Studies Program, and Co-Director of the O’Neill-Pellegrino Center Program in Brain Science and Global Health Law and Policy at Georgetown University Medical Center.
Source: This article was published in PRISM Vol. 8, No. 3, which is published by the National Defense University.
Notes
1 Patricia DeGennaro, “The Gray Zone and Intelligence Preparation of the Battle Space,” Small Wars Journal Mad Scientist no. 13 (2016).
2 Jonathan D. Moreno, Michael Tennison, and James Giordano, “Security Threats Versus Aggregated Truths: Ethical Issues in the Use of Neuroscience and Neurotechnology for National Security,” in Neuroethics: Anticipating the Future, ed. Judy Illes (New York: Oxford University Press, 2017).
3 Joseph DeFranco et al., “Emerging Technologies for Disruptive Effects in Non-Kinetic Engagements,” Journal of the Homeland Defense & Security Information Analysis Center 6, no. 2 (2019): 48–55.
4 Malcolm Dando, “Neuroscience Advances and Future Warfare,” Handbook of Neuroethics (2015): 1785–1800.
5 J. Craig Venter et al., “The Sequence of the Human Genome,” Science 291, no. 5507 (2001): 1304–1351; International Human Genome Sequencing Consortium, “Finishing the Euchromatic Sequence of the Human Genome,” Nature 431, no. 7011 (2004): 931.
6 Angeliki Vgontzas and William Renthal, “Introduction to Neurogenetics,” American Journal of Medicine 132, no. 2 (2019): 142–152; Alkes L. Price et al., “Principal Components Analysis Corrects for Stratification in Genome-wide Association Studies,” Nature Genetics 38, no. 8 (2006): 904; Iris E. Jansen et al. , “Genome-wide Meta-analysis Identifies New Loci and Functional Pathways Influencing Alzheimer’s Disease Risk,” 2019; Andreas Papassotiropoulos and J-F. Dominique, “Genetics of Human Episodic Memory: Dealing with Complexity,” Trends in Cognitive Sciences 15, no. 9 (2011): 381–387.
7 Diane DiEuliis and James Giordano, “Gene Editing Using CRISPR/Cas9: Implications for Dual-use and Biosecurity,” Protein & Cell 9, no. 3 (2018): 239–240; Huda Y. Zoghbi and Stephen T. Warren, “Neurogenetics: Advancing the ‘Next Generation’ of Brain Research,” Neuron 68, no. 2 (2010): 165–173.
8 Yang-Gyun Kim, Jooyeun Cha, and Srinivasan Chandrasegaran, “Hybrid Restriction Enzymes: Zinc Finger Fusions to Fok I Cleavage Domain,” Proceedings of the National Academy of Sciences 93, no. 3 (1996): 1156–1160.
9 Dana Carroll, “Genome Engineering with Zinc-Finger Nucleases,” Genetics 188, no. 4 (2011): 773–782; Elena E. Perez et al., “Establishment of HIV-1 Resistance in CD4+ T cells by Genome Editing Using Zinc-Finger Nucleases,” Nature Biotechnology 26, no. 7 (2008): 808; A.A. Nemudryi et al., “TALEN and CRISPR/Cas Genome Editing Systems: Tools of Discovery,” Acta Naturae 6, no. 3 (2014): 22.
10 Diane DiEuliis and James Giordano, “Why Gene Editors Like CRISPR/Cas May Be A Game-Changer for Neuroweapons,” Health Security 15, no. 3 (2017): 296–302.
11 Antonio Regalado, “Chinese Scientists Are Creating CRISPR Babies,” MIT Technology Review, November 25, 2018, available at <https://www.technologyreview.com/s/612458/exclusive-chinese-scientists-are-creating-crispr-babies/>; David Cyranoski, “CRISPR Gene-Editing Tested in a Person for the First Time,” Nature News 539, no. 7630 (2016): 479.
12 World Health Organization, “WHO Expert Panel Paves Way for Strong International Governance on Human Genome Editing,” March 19, 2019, available at <https://www.who.int/news-room/detail/19-03-2019-who-expert-panel-paves-way-for-strong-international-governance-on-human-genome-editing>.
13 Daniel Gerstein and James Giordano, “Rethinking the Biological and Toxin Weapons Convention?” Health Security 15, no. 6 (2017): 638–641.
14 Antonio Regalado, “The Search for the Kryptonite that Can Stop CRISPR,” MIT Technology Review, May 2, 2019, available at <https://www.technologyreview.com/s/613309/the-search-for-the-kryptonite-that-can-stop-crispr/>.
15 D. Cyranoski, “Russian Biologist Plans More CRISPR-edited Babies,” Nature 570, no. 7760 (2019): 145.
16 C.D. Wolinetz and F.S. Collins, “NIH Supports Call for Moratorium on Clinical Uses of Germline Gene Editing,” (2019): 175.
17 Florence Sanchez and Konstantin Sobolev, “Nanotechnology in Concrete—A Review,” Construction and Building Materials 24, no. 11 (2010): 2060–2071; Andrea Gropman, “Applying Advances in Neurogenetics to Medical Practice,” 2006: 677–685.
18 DeFranco et al., “Emerging Technologies.”
19 Nicholas O. Fischer et al., “Evaluation Of Nanolipoprotein Particles (NLPs) as an In Vivo Delivery Platform,” PloS One 9, no. 3 (2014): e93342.
20 National Academies of Sciences, Engineering, and Medicine, Biodefense in the Age of Synthetic Biology (Washington, DC: National Academies Press, 2018).
21 Sumiyo Watanabe et al., “In Vivo Rendezvous of Small Nucleic Acid Drugs with Charge-matched Block Catiomers to Target Cancers,” Nature Communications 10, no. 1 (2019): 1894.
22 DeFranco et al., “Emerging Technologies.”
23 Ina Balke and Andris Zeltins, “Use of Plant Viruses and Virus-Like Particles for the Creation of Novel Vaccines,” Advanced Drug Delivery Reviews (2018).
24 Michael C. Milone and Una O’Doherty, “Clinical use of Lentiviral Vectors,” Leukemia 32, no. 7 (2018): 1529.
25 Lei Shi et al., “Transgenic Rhesus Monkeys Carrying the Human MCPH1 Gene Copies Show Human-like Neoteny of Brain Development,” National Science Review 6, no. 3 (2019): 480–493.
26 Guillermo Palchik, Celeste Chen, and James Giordano, “Monkey Business? Development, Influence, and Ethics of Potentially Dual-use Brain Science on the World Stage,” Neuroethics 11, no. 1 (2018): 111–114.
27 Christopher Ochs et al., “Quality Assurance of the Gene Ontology Using Abstraction Networks,” Journal of Bioinformatics and Computational Biology 14, no. 3 (2016): 1642001.
28 David L. Wheeler et al., “Database Resources of the National Center for Biotechnology Information,” Nucleic Acids Research 35, no. suppl. 1 (2006): D5-D12.
29 Joseph DeFranco and James Giordano, “Designer Genes: Made in China?” Mad Scientist Laboratory, post no. 66, August 1, 2019, available at <https://madsciblog.tradoc.army.mil/166-designer-genes-made-in-china/>.
30 For more information on in silico genome analysis tools, see Maximilian Haeussler et al., “Evaluation of Off-target and On-target Scoring Algorithms and Integration into the Guide RNA Selection Tool CRISPOR,” Genome Biology 17, no. 1 (2016): 148; Tessa G. Montague et al., “CHOPCHOP: A CRISPR/Cas9 and TALEN Web Tool for Genome Editing,” Nucleic Acids Research 42, no. W1 (2014): W401–W407; Luca Pinello et al., “Analyzing CRISPR Genome-Editing Experiments with Crispresso,” Nature Biotechnology 34, no. 7 (2016): 695; Sangsu Bae, Jeongbin Park, and Jin-Soo Kim, “Cas-OFFinder: A Fast and Versatile Algorithm that Searches for Potential Off-target Sites of Cas9 RNA-guided Endonucleases,” Bioinformatics 30, no. 10 (2014): 1473–1475; and Venetia Pliatsika and Isidore Rigoutsos “‘Off-Spotter’: Very Fast and Exhaustive Enumeration of Genomic Lookalikes for Designing CRISPR/Cas Guide RNAs,” Biology Direct 10, no. 1 (2015): 4.
31 For more information on in vitro genome analysis tools, see Shengdar Q. Tsai et al., “CIRCLE-seq: A Highly Sensitive In Vitro Screen for Genome-wide CRISPR–Cas9 Nuclease Off-targets,” Nature Methods 14, no. 6 (2017): 607; and Peter Cameron et al., “Mapping the Genomic Landscape of CRISPR–Cas9 Cleavage,” Nature Methods 14, no. 6 (2017): 600. For more information on in vivo genome analysis tools, see Pinar Akcakaya et al., “In Vivo CRISPR Editing with No Detectable Genome-wide Off-target Mutations,” Nature 561, no. 7723 (2018): 416; and Winston X. Yan et al., “BLISS Is a Versatile and Quantitative Method for Genome-wide Profiling of DNA Double-strand Breaks,” Nature Communications 8 (2017): 15058.
32 Blake Marshal Elias, “High Throughput Pin-tool Based Automated DNA Assembly,” PhD diss., Massachusetts Institute of Technology, 2018; Michael I. Sadowski, Chris Grant, and Tim S. Fell, “Harnessing QbD, Programming Languages, and Automation for Reproducible Biology,” Trends in Biotechnology 34, no. 3 (2016): 214–227.
33 Kent S. Boles et al., “Digital-to-Biological Converter for On-demand Production of Biologics,” Nature Biotechnology 35, no. 7 (2017): 672.
34 Anthony Croxatto et al., “Laboratory Automation in Clinical Bacteriology: What System to Choose?” Clinical Microbiology and Infection 2, no. 3 (2016): 217–235; Jacob Nichols et al., “2069. Automation Process Improving Microbiological Laboratory Efficiency,” Open Forum Infectious Diseases 5, suppl. 1 (New York: Oxford University Press, 2018), S604.
35 For example, Hannah Denham and Drew Harwell, “Panic over Russian Company’s FaceApp Is a Sign of New Distrust of the Internet,” Washington Post, July 18, 2019, available at <https://www.washingtonpost.com/technology/2019/07/18/heres-what-we-know-about-russian-company-behind-faceapp/>.
36 Claudia Geib, “A Chinese Province is Sequencing One Million of Its Residents’ Genomes,” Futurism, November 8, 2017, available at <https://futurism.com/chinese-province-sequencing-1-million-residents-genomes>.
37 Nanjing YiGenCloud, “Nanjing YiGenCloud Institute Aims to Speed Up the Process of China’s Precision Medicine with ‘Intelligence,’” Cison PR Newswire, May 27, 2019, available at <https://www.prnewswire.com/news-releases/nanjing-yigencloud-institute-aims-to-speed-up-the-process-of-chinas-precision-medicine-with-intelligence-300856584.html>.
38 This refers to the field of neuroepigenetics, which is outside the purview of this paper. For more information, see J. David Sweatt, “The Emerging Field of Neuroepigenetics,” Neuron 80, no. 3 (2013): 624–632.
39 Claudia Archetti et al., “Clinical Laboratory Automation: A Case Study,” Journal of Public Health Research 6, no. 1 (2017); Gustavo de Freitas Nobre, Marcelo Kalichsztein, and Marcelo Martínez Ramos, “Hospital Bed Automation System and Methods for Performing Signal Read and Correlation as well as Real-time Data Processing,” U.S. Patent Application 16/300,272, filed May 16, 2019.
40 Nathaniel Comfort, “Sociogenomics Is Opening a New Door to Eugenics,” MIT Technology Review, October 23, 2018, available at <https://www.technologyreview.com/s/612275/sociogenomics-is-opening-a-new-door-to-eugenics/>.
41 Lukasz Piwek et al., “The Rise of Consumer Health Wearables: Promises and Barriers,” PLoS Medicine 13, no. 2 (2016): e1001953.
42 Jean Peccoud et al., “Cyberbiosecurity: From Naive Trust to Risk Awareness,” Trends in Biotechnology 36, no. 1 (2018): 4–7.
43 Diane DiEuliis, Chuck D. Lutes, and James Giordano, “Biodata Risks and Synthetic Biology: A Critical Juncture,” Journal of Bioterror and Biodefense 9, no. 159 (2018): 2.
44 Raza Qazi et al., “Wireless Optofluidic Brain Probes for Chronic Neuropharmacology and Photostimulation,” Nature Biomedical Engineering (2019): 1–15.
45 Joseph DeFranco and James Giordano, “Linking Brains to Machines, and Use of Neurotechnology to the Cultural and Ethical Perspectives of the Current Global Stage,” Mad Scientist Laboratory, post no. 168, August 8, 2019, available at <https://madsciblog.tradoc.army.mil/168-linking-brains-to-machines-and-use-of-neurotechnology-to-the-cultural-and-ethical-perspectives-of-the-current-global-stage/>.
46 Dian DiEuliis and James Giordano, “Neurotechnological Convergence and ‘Big Data’: A Force-Multiplier Toward Advancing Neuroscience,” in Ethical Reasoning in Big Data, 71–80, Springer, Cham, 2016.
47 Malcolm Dando, “Advances in Neuroscience and the Biological and Toxin Weapons Convention,” Biotechnology Research International (2011); Giordano and Wurzman, “Neurotechnologies as Weapons in National Intelligence and Defense.”
48 Rain Liivoja and Luke Chircop, “Are Enhanced Warfighters Weapons, Means, or Methods of Warfare?” International Law Studies 94, no. 1 (2018): 7.
49 Verification refers to the countries’ national regulations and acceptable execution of international legislation. Although countries are forced to implement codes that prevent the existence of agents that do not serve “prophylactic, protective, or other peaceful” purposes, states may choose not to enforce such laws. Enforcement refers to the infliction of retribution to states that do not follow international regulations. Without proper verification of states’ adherence to the BTWC, CWC, or UNSCR 1540, it is impossible to enforce a violation by a nation.
50 Joseph DeFranco, L.R. Bremseth, and James Giordano, “The Importance of Integrative Science/Technology Intelligence (InS/TINT) to the Prediction of Future Vistas of Emerging Threats,” Mad Scientist Laboratory, post no. 125, March 13, 2019, available at <https://madsciblog.tradoc.army.mil/125-the-importance-of-integrative-science-technology-intelligence-ins-tint-to-the-prediction-of-future-vistas-of-emerging-threats/>.
51 Moreno, Tennison, and Giordano, “Security Threats Versus Aggregated Truths.”
52 Christine Aicardi et al., Dual Use in Neuroscience and Neurotechnology (London: Human Brain Project Foresight Lab at King’s College London, 2017); The European Parliament and the Council of the European Union, “Position (EU) No 5/2014 of the council at First Reading with a view to the adoption of a Regulation of the European Parliament and of the Council amending Council Regulation (EC) No 428/2009 setting up a Community regime for the control of exports, transfer, brokering and transit of dual-use items,” Official Journal of the European Communities, C 100, no. 6 (2014).

