Beneath The Crosshairs: Remotely Piloted Airstrikes As A Foreign Policy Tool – Analysis
By NDU Press
By Roderic K. Butz*
The key principles of the laws of war are necessity, distinction, and proportionality in the use of force. Drone attacks and targeted killings serve these principles better than any use of force that can be imagined. –Richard Pildes1
Nearly a year before the attacks of September 11, 2001, the United States flew its first unarmed remotely piloted aircraft (RPA) sortie against Osama bin Laden and al Qaeda in Afghanistan.2 In November 2001, following the terrorist attacks, the United States launched its first armed RPA kinetic strike against an al Qaeda leader in Afghanistan.3 Since then, the United States has executed more than 6,000 RPA strikes against a myriad of declared terrorist organizations and threat groups across the globe.4 The tactical value of RPA and their crews has proven to be, as Richard Pildes stated, “the most discriminating use of force that has ever been developed.”5
While the proven utility of armed RPA represents a significant evolution in military capability and the character of war, perhaps more important, it also represents a revolution in U.S. foreign policy. Successful RPA strikes have led some to believe their use allows “Presidents to punt on questions of war and peace,” relying on tactical military capability to supplant strategy.6 Because RPA strikes offer the unique ability to directly affect strategic objectives with a low risk to forces and a small footprint, policymakers may be tempted to resort directly to the use of force to resolve complex security challenges.7 But RPA strikes are a tool, not a strategy in their own right. They are a facet of a broad effort to attain political ends through the concerted use of all available instruments of national power. Without a clearly identified endstate and coordinated whole-of-government strategy, RPA strikes alone actually increase risk to national policy objectives, destabilize fragile regions, and isolate key partners.
A comprehensive study of the effects of RPA strikes on foreign policy would require vast background knowledge, unbiased analysis, access to classified data, and a complex contextualization of the character of belligerents, geopolitical relationships, and U.S. policy goals. This article represents a more limited analysis and instead focuses on five topics within the context of U.S. military RPA strikes outside declared theaters of active armed conflict (ODTAAC). First, it outlines key assumptions and facts related to the legality, authorities, and classification of RPA operations. Second, it explores the evolution of U.S. policy on the use of RPA over the past two decades and three Presidential administrations. Third, it lays out the unique attributes of RPA operations that facilitate their use as a foreign policy tool in ODTAAC environments. Fourth, it analyzes the attributes of RPA strikes that alone may detract from national security objectives and lead to instability, governmental illegitimacy, and increased strategic risk, including ineffective targeting theory and mischaracterization of the operational environment. Finally, the article offers a series of recommendations for the effective use of RPA in ODTAAC environments as a facet of national strategy.
Scope
America’s rapid expansion in the use of armed RPA following the attacks of 9/11 created a broad array of new legal, ethical, and political issues that remain widely unaddressed today. These issues include but are not limited to the employment of armed RPA through the lens of U.S. legal code, international humanitarian law (IHL), military rules of engagement, and the legal authorization for use of military force (AUMF).
First, analysis and examination of U.S. military RPA strikes in ODTAAC theaters are based on the assertion that the use of armed RPA by the United States is authorized through established mechanisms within the Department of Defense, the Office of the Director of National Intelligence, and the national security establishment. In today’s counterterrorism (CT) campaigns, authorization is established through various classified and unclassified permissions including Public Law 107-40, which declares:
That the President is authorized to use all necessary and appropriate force against those nations, organizations, or persons he determines planned, authorized, committed, or aided the terrorist attacks that occurred on September 11, 2001, or harbored such organizations or persons, in order to prevent any future acts of international terrorism against the United States by such nations, organizations, or persons.8
Second, from a legal perspective, this article assumes the targeting processes and strike approvals are consistent with an AUMF and U.S. legal code and do not constitute assassination or extrajudicial executions.9 Because of the character of CT targets and the authorized use of force, RPA strikes do not violate the Ronald Reagan administration Executive Order (EO) 12333, which states “no person employed by, or acting on behalf of, the United States Government shall engage in, or conspire to engage in, assassination.”10 Additionally, this legality is not differentiated by the specific source of authority, be it Title 10 or Title 50 of U.S. Code, whereby an approved AUMF covers both traditional military and intelligence activities against external actors.11
Finally, within the scope of IHL, the authorized rules of engagement for U.S. military RPA strikes are consistent with the concept of jus in bello, with a mandate of proportionality, distinction, humanity, military necessity, protection of nonbelligerents, and a minimization of suffering for the victims of armed conflict.12 Critics posit that RPA technology makes attainment of military distinction and proportionality “more ambiguous and their achievement more problematic.”13 On the contrary, according to Pildes, because of the networked human interface, legal insight during targeting, technological advances, and command-level oversight, RPA operations “serve these principles [of IHL] better than any use of force that can be imagined.”14 Finally, this analysis on the efficacy of RPA strikes in the ODTAAC environment is at the unclassified level and proceeds with the assertion that they are both legal and ethical when authorized through traditional national security processes of the U.S. Government and executed in accordance with approved rules of engagement.
Policy Evolution
To better analyze the implications for U.S. policy of using armed RPA as a military tool, it is necessary to understand how the rapid expansion of this capability following 9/11 drove the evolution of policy through three Presidential administrations. The first operational use of the RQ-1 Predator, the successor to the widely proliferated MQ-1 and MQ-9 Reaper, occurred in 1995 over Bosnia. Employed primarily for intelligence, surveillance, and reconnaissance (ISR) through use of its full-motion video, the RQ-1, according to Richard Whittle, “played a key role in helping [the North Atlantic Treaty Organization] bring key factions . . . to peace talks,” enhancing the quality and quantity of targetable intelligence.15 In late 1999, based on the success of the RQ-1 in Bosnia, and in response to the growing threat of al Qaeda following terrorist attacks in Tanzania and Kenya, the United States began efforts to arm the Predator. One year later, the United States commenced limited employment of unarmed MQ-1 sorties for ISR missions over Afghanistan, resulting in an assessed sighting of Osama bin Laden in September 2000.16 For the next year, though the concept of RPA strikes was proved as feasible, policymakers, military leaders, and intelligence officials grappled with the formulation of a comprehensive, multiyear counterterrorism campaign to address the al Qaeda threat.

Even though RPA strike approvals were granted through the National Security Council and aligned with U.S. legal channels vis-à-vis EO 12333, on September 4, 2001, the plan to strike bin Laden was tabled. The primary reasons for this delay were based on budget disputes between the Central Intelligence Agency (CIA) and the Air Force, a fear among analysts of escalation in the event of an MQ-1 shootdown, and existing technological limitations on the reliability of the hellfire missile.17 In an impassioned response, Richard Clarke, the National Coordinator for Security, Infrastructure Protection, and Counterterrorism, declared to the U.S. Principals Committee, “decisionmakers should imagine themselves on a future day when [they have] not succeeded in stopping al [Qaeda] attacks and hundreds of Americans lay dead in several countries, including the [United States].”18 Unfortunately, while there is no evidence that a decapitation strike against bin Laden during the summer of 2001 would have prevented impending attacks, the future day that Clarke spoke of occurred less than 1 week after the meeting.
With only a handful of unarmed Predators over Afghanistan in September 2001 under the authorities of Operation Enduring Freedom, the United States was not postured to execute immediate kinetic strikes against bin Laden and al Qaeda, requiring a mobilization of thousands of intelligence and military professionals. Within 1 week of 9/11, concurrent with President George W. Bush’s AUMF (Public Law 107-40), the United States commenced its first armed MQ-1 sortie over Afghanistan—harkening the evolutionary era of armed RPA operations as both a military tool and a tool of American foreign policy. Subsequently, because of the pre-9/11 policy disagreements and rapid expansion of this emerging capability following the attacks, the United States never developed a coherent, comprehensive legally based policy before conducting its first RPA strike on November 12, 2001. The operational demands of the war on terror necessitated emergency expansion of RPA operations, leaving Presidential administrations, lawmakers, and military leaders in a reactive position to analyze policy issues, classification levels, departmental authorities, strategic impacts, and the long-term efficacy of this capability.
Under the administration of President Bush, aligned with theater campaign plans, the RPA force expanded rapidly in both declared theaters of active armed conflict (DTAAC) and ODTAAC environments within the Middle East, Africa, and the Pacific. Beyond Afghanistan and Iraq, wherein RPA were highly effective against al Qaeda, the Taliban, and other terrorist networks, the Bush administration directed approximately 57 RPA strikes supporting named operations against declared terrorist organizations in ODTAAC regions in Pakistan, Yemen, and Somalia.19 Under the auspices of the war on terror, President Bush established the foundational assertions of the legality, ethicality, and policy use of RPA that evolved little in nearly two decades. Though the corporate view of the CIA, according to the International Journal of European Relations, was reluctant or outright opposed to armed RPA strikes, that position changed following 9/11. The attacks on 9/11 led the CIA to change its position, wherein it developed a deliberate targeting and strike system that separated “targeted killing” from assassination “rather than defending assassination itself.”20 While the Bush administration was successful in its limited ODTAAC RPA strike campaigns, executing approximately 57 strikes, the legacy lay in the policies that withstood the early years of the war and bolstered President Barack Obama’s dramatic increase of remote strikes as a foreign policy tool.
While President Obama has been credited for significant military drawdowns in Iraq and Afghanistan during his Presidency, according to the Washington Examiner, his true legacy will be that of the “Drone President.”21 According to the Bureau of Investigative Journalism, over 520 RPA strikes occurred during the Obama Presidency, a near 10-fold increase from the previous administration.22 Additionally, sources claim that the number of American “drones” increased over 14,000 percent from approximately 50 in 2000 to over 7,000 in the arsenal by 2012.23 Unfortunately, like significant portions of reporting on RPA, this claim is not entirely applicable to the discussion of RPA strikes, as only 372 were armed RPA variants as of 2014.24
Regardless of the precision and accuracy of such claims, due to wide proliferation and technical advancements of weapons, sensors, and platforms, the use of armed RPA as a policy tool increased dramatically under President Obama. Concomitantly, under heavy scrutiny regarding collateral damage and civilian casualties, the administration undertook a comprehensive examination of policies, authorizations, oversight, and RPA employment practices. In 2013, this examination culminated in new Presidential Policy Guidance (PPG) that provided the legal framework for target identification, operational authorities, and lethal strike approvals.25 Additionally, President Obama signed a 2016 EO further outlining the criteria for “near certain” avoidance of collateral damage and civilian casualties, while mandating requirements governing employment, congressional oversight, and annual reporting of lethal strikes.26
While the use RPA strikes under President Obama expanded substantially from 2009 to 2016, with a former CIA officer declaring “phenomenal success” at diminishing terrorist organizations worldwide, the administration took active steps to declassify, regulate, limit, oversee, and report on the use of RPA strikes as a tool of foreign policy.27 The move toward transparency, oversight, and limitations on the use of armed RPA under President Obama was a necessary first step in lifting the veil of secrecy and normalizing the legal use of this critical capability. But the constructive momentum to codify the employment, oversight, reporting, and legal attributes of RPA strikes effectively ended with the inauguration of President Donald Trump.
Upon taking office in 2017, President Trump replaced the Obama PPG with his own Principles, Strategies, and Procedures (PSP) that regulate direct action CT operations, including the use of armed RPA strikes in ODTAAC environments. According to the New York Times, the new PSP loosened the requirements for target selection, streamlined strike approval delegation, and removed the requirement for high-level vetting, oversight, and reporting.28 Coincident with a significant increase in RPA strike operations, including the campaign against the so-called Islamic State (IS), the new PSP meant that the threshold for when to conduct strikes was lower and that there was not nearly as much high-level oversight of these strikes.29 Notably, there remain significant levels of planning, operational analysis, legal reviews, and oversight at and above the combatant command level. While the impact of the current administration’s changes is not yet known, the policy reversal away from transparency, high-level oversight, and reporting requirements restricts necessary evaluation and debate of the efficacy of this capability as a tool of foreign policy.
Though there has been a marked decline in strikes against IS in Syria as its territorial caliphate dissolves, the widespread use of lethal RPA strikes against terrorist leaders, facilitators, and fielded forces in other theaters has increased substantially since 2017, with the Bureau of Investigative Journalism reporting over 5,500 strikes in the first 2 years of the Trump Presidency.30 While the reporting of actual numbers of strikes has become more difficult to assess due to President Trump’s PSP, it is clear that this capability has expanded in both frequency and territory, including the establishment of a new RPA base in Agadez, Niger.31 Categorically, the use of armed RPA against terrorist threats has increased substantially since the late autumn of 2001 and will likely continue. While Presidential policy on the strategic use of armed RPA continues to evolve, preventing transparent analysis, debate, and foreign policy formulation, it is critical that lawmakers, military planners, and the public not conflate policy challenges with the tactical prowess of the MQ-1 and MQ-9 enterprise, which has proved extraordinarily effective as a military capability. Furthermore, in order to analyze the efficacy of armed RPA operations at the strategic level, it is necessary to understand the unique characteristics of this capability that often drive policymakers to use it as what Jacqueline Hazelton calls “the new face of US foreign policy.”32
The Unique Value of Armed RPA Operations
The tactical use of RPA and kinetic strikes represents a “means” and a “way,” respectively, to meet strategic ends. Comprehensively, RPA employment is unique from both a resourcing and capability perspective. It is both rational and reasonable to see how this tactical means could be harnessed as a foreign policy tool to meet combatant commanders needs in ODTAAC environments. These characteristics include perceived decreased risk, decreased cost, and decreased deployed signature compared to conventional, manned strike assets.
The primary reason lawmakers tend to support RPA strikes as a principal foreign policy tool to address security challenges is due to the relatively low risk to U.S. forces combined with the tactical effectiveness of the capability and low risk to the military mission itself. RPA operations, by design, mitigate risk to U.S. forces by protecting remote operators from the typical threats to air operations, including antiaircraft artillery and surface to air missiles. Additionally, though current RPA operations require a small footprint of deployed personnel to support taxi, takeoff, landing, and aircraft maintenance requirements, these forces typically remain beyond conflict zones and in lower threat areas and established installations.
In addition to the decreased risk to force, technological advances, precision weaponry, and aircrew expertise decrease the overall risk to successful tactical mission execution. This expertise and decreased risk to mission is evident in the analysis of armed RPA operational effects and their continuous improvements since 9/11. For example, from 2013 to 2019, a single Air Force RPA squadron of less than 100 U.S.-based personnel executed over 1,000 kinetic strikes against enemy forces in seven countries.33 The results of these strikes were 2,592 enemy killed in action with a staggering success rate of 98 percent with zero loss of life to U.S. Servicemembers.34 While the combat results of this squadron are unique and distinctive, this example highlights the low-risk effectiveness of RPA strikes to support U.S. policy objectives. This uneven combat risk between belligerents when using remote strike capabilities is a significant evolution in the character of warfare that leads toward policy preference to meet contemporary security challenges.
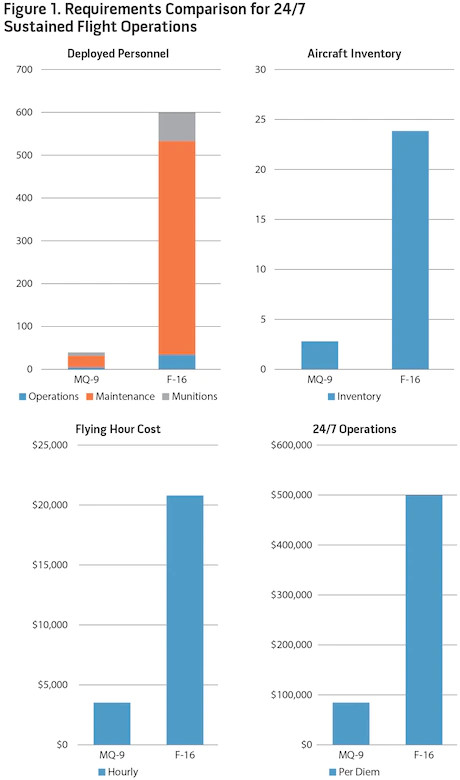
An added factor that drives a preference for RPA strikes as a policy tool is the financial cost of deployment and employment. Additionally, compared to a conventional strike capability, the deployed footprint utilizing RPA is decreased by nearly 94 percent.35 As figure 1 highlights, to fulfill a sustained (beyond 30-days) 24/7 kinetic strike capability, the decreased requirement for aircrew and maintenance “boots on the ground” makes RPA a preferable option to fulfill an operational need.36
These personnel savings manifest themselves in significant financial savings from mobilization costs and deployed financial entitlements as well as aircraft operating costs. To support sustained airstrike capability the hourly difference to operate an MQ-9 versus an F-16 is over $17,000 and nearly 6,000 pounds of fuel.37 Per diem, this results in a savings of nearly $420,000 and 187,000 pounds of fuel with one MQ-9 sortie versus 24 F-16 sorties, according to a RAND study.38
Finally, in addition to the resourcing and financial savings, it is necessary to understand the opportunity cost of RPA employment versus manned aircraft. As the United States shifts security focus to peer/near-peer threats in contested environments, key capabilities such as multirole, manned strike aircraft must be apportioned and allocated appropriately to mitigate contemporary threats beyond the ODTAAC CT fight. Typical operational requirements in the ODTAAC environment to support ISR and tactical airstrike capability,necessitate persistence, flexibility, and limited strike capability. The fact that RPA can meet/exceed this 24-hour requirement with a typical force package of three aircraft, vice 18-24 F-16s according to a RAND study, provides policymakers with greater flexibility for apportionment of high-end, manned capabilities to meet the challenges posed by rogue nations and revisionist powers.39 Necessary to annotate, while RPA provide extraordinarily precise, persistent strike capability, some situations demand strike options that RPA simply cannot provide due to operating limitations (satellite bandwidth/footprint, basing), limited armament payload, and a lack of defensive capability.
While this data drives policymakers often to prefer RPA to manned strike aircraft from a resourcing standpoint, RPA offer unique tactical capabilities as well that further support U.S. security policy. Specifically, modern U.S. RPA employ diverse technologies that represent an evolution in airpower capability, including advanced precision weapons, integrated communications, and multi-intelligence fusion.
The current MQ-9 aircraft employed across the globe maintains the ability to loiter over a single target for over 20 hours, providing capability that historically required multiple types and quantities of various manned aircraft. Highly trained crew employ technological capabilities within the platform that facilitate ISR collection through use of high-definition infrared, short-wave infrared, and visual spectrum (electro-optical) full-motion videos. Additionally, use of synthetic aperture radar and signals intelligence provides combatant commands with a broad array of capabilities to collect and disseminate information regarding enemy personnel and capabilities. The communications suite on the current MQ-9 includes FM, UHF, VHF, satellite communications, voice over Internet protocol, secure Internet (at the secret and top-secret level), and secure telephonic capability. Finally, the MQ-9 retains the ability to carry an extensive variety of precision-guided weapons including 500-pound laser-guided bombs, 1,000-pound GPS-guided munitions, and various laser-guided Hellfire missiles.
The combined capabilities of a single MQ-9 offer military commanders and policymakers an evolutionary cost-effective tool to support the entire joint targeting cycle to find, fix, and finish (kill) enemy forces while concurrently exploiting, analyzing, and disseminating intelligence information. Examples of these synergistic and diverse kinetic capabilities inherent to the MQ-9 include previously infeasible strikes against fast-moving targets in highly populated areas, strikes using extremely low-collateral-damage weapons, and massed employment against fortified positions and enemy formations.
The evolutionary leap in airpower capability that the MQ-9 represents is displayed through a number of recent strike, including the one against General Qasem Soleimani near the Baghdad International Airport, where MQ-9s were able to use multi-intelligence collection, a robust command and control network, and niche weapons capability to execute a strike against a moving vehicle in a dense urban area with no collateral damage. Additionally, as reported from recent strikes in Syria, using modified niche weapons with lower explosive yield, MQ-9s are able to strike individual targets in densely populated areas with no collateral damage.40 Last, in contrast to the precision low-yield strikes, the MQ-9 also retains the capability to conduct massed attack against fortified positions and large troop formations as seen in the 2016 strike against an al Shabab training camp that resulted in 167 enemy killed in action, the deadliest single-salvo airstrike since 9/11.41 Because of the niche tactical competencies of RPA, the staggering disparity in risk and resource requirements, and the opportunity costs associated with manned capability, RPA will continue to be the primary option to meet operational requirements for ISR and air-to-ground strike capability in permissible ODTAAC environments.
While RPA strikes often attain strategic effects, it is important to remember that the tactical use of RPA and kinetic strikes represents merely a means and a way to support policy objectives and must not supplant formulation of effective national strategy. Despite the myriad niche capabilities and the potential strategic effect of RPA strikes, they are often conflated as a strategy or policy in and of themselves. As Jeremy Scahill states, “drones RPA are a tool, not a policy.”42 Moreover, with overdependence on this highly effective capability as an often chosen tool to address security challenges, policymakers and senior leaders must understand those characteristics of RPA strikes that consequently detract from national security objectives in ODTAAC environments.
The Potential Cost of Armed RPA Operations
The term drone carries a generally negative connotation with thoughts of killer flying robots, breaches of personal privacy, and safety risks to aviation. The phrase drone strike may convey even deeper malice, conjuring images of civilian casualties, collateral damage, assassination, extrajudicial killing, and the militarization of American foreign policy.43 While this view may simply be a biased narrative based on current literature and ill-informed reporting, it is critical that the concept be analyzed from a strategic perspective to identify those characteristics of RPA operations that may actually detract from U.S. policy objectives. Specifically, this examination of RPA strikes must identify factors that result in political scrutiny, socioeconomic instability, host-government illegitimacy, and increased strategic risk. The primary factors that often produce the above risks include opaque U.S. policies on the use of RPA, the destructive narrative of drone strikes, an incomplete characterization of the enemy’s operating environment, and what author James Kiras explains as “the appeal of an apparent simple, direct and low-cost solution to a difficult strategic problem.”44 Collectively, lacking an understanding of these factors and an active mitigation plan, reliance on armed RPA operations as the core of a narrow security strategy may further destabilize fragile regions, isolate key partners, and detract from national security objectives.
A primary risk factor in the use of armed RPA, and a consistent criticism from both domestic and international entities, is the opaque nature in which strikes are authorized, executed, and reported. This lack of transparency, from a policy and oversight perspective, restricts necessary debate on the appropriate use, legal framework, and strategic effectiveness of this niche capability as a policy tool. While limited steps toward policy transparency occurred between the Bush and Obama administrations, the Trump administration’s rollback on these initiatives increased opacity, resulting in what Rachel Stohl argues is “a lack of clarity over who represents a legitimate target, and greater secrecy regarding the ways in which operations are conducted, by whom, and the results of such operations.”45 This continued opacity increases policy and strategic risks, wherein transparency is both appropriate and necessary.
Though the assertion is made, and necessarily so, that certain facets of armed RPA operations must remain classified (for example, collection methods, weapons capabilities, operating locations of deployed personnel), there is value in transparent reporting of U.S. targeting efforts, strategic objectives, and the associated successes and challenges. Viewed holistically, armed RPA operations are an evolutionary step in warfare and jus in bello, resulting in greater discrimination in the use of force, increased confidence in effective targeting, and substantially decreased risk to noncombatants. Lacking transparent reporting and accountability, the extraordinary tactical effectiveness of armed RPA operations (in both DTAAC and ODTAAC environments) is relegated to a narrative of excess, illegality, immorality, and destruction. This misinformed narrative, resulting from the opacity of U.S. policy, is further enhanced by an overwhelming quantity of imprecise media reports, individual editorials, books, movies, and an ineffective U.S. informational counternarrative.46
Critics assert that RPA advocates often highlight technological advances as the main factor in assuring proportionality and discrimination. Sarah Kreps highlights this point when quoting State Department legal advisor Harold Koh, who stated that RPA technology “ensures that only legitimate objectives are targeted, and that collateral damage is kept to a minimum.”47 Koh’s argument based on technology fuels critics, who assert that technology intrinsically confuses the “determination of legal or ethical legitimacy.”48 Both Koh and Kreps do not acknowledge the central role of the human interface within the RPA operational framework. This include oversight and review from national-level authorities to the combatant command leadership, legal experts, operational planners, all-source intelligence analysts, targeteers, and individual aircrew members. While it may seem apparent, airplanes do not make decisions; when operated by highly trained crews, RPA represent a means to better inform and facilitate human decisions. In fact, the RPA human network is significantly more robust than more traditional weapons systems, decreasing the ambiguity of distinction and proportionality. As is the case with all aspects of IHL, it is within this human interface that those legal and ethical determinations are attained.
The second risk factor to consider is based on the malign narrative of armed RPA operations. For instance, reviewing results of a simple Internet search of the phrase drone strike illustrates the overwhelmingly aspersive narrative surrounding American use of armed RPA, with nearly 80 percent of search results demonstrating negativity and disapproval. This narrative primarily highlights civilian casualties, collateral damage, the (il)legality of targeted killings, and what Amnesty International terms American “imperial overreach.”49
While transparent and constructive dialogue on topics such as legality, ethicality, unintended consequences, and strategic use of RPA is critical to ensure effective utilization of this capability, it is too often imbalanced, unverified, and/or wholly inaccurate. A simple comparison based on data from various reporting organizations reveals broad statistical disparity, and when compared to a smaller subset based on personal experience, the inaccuracies become even more apparent.
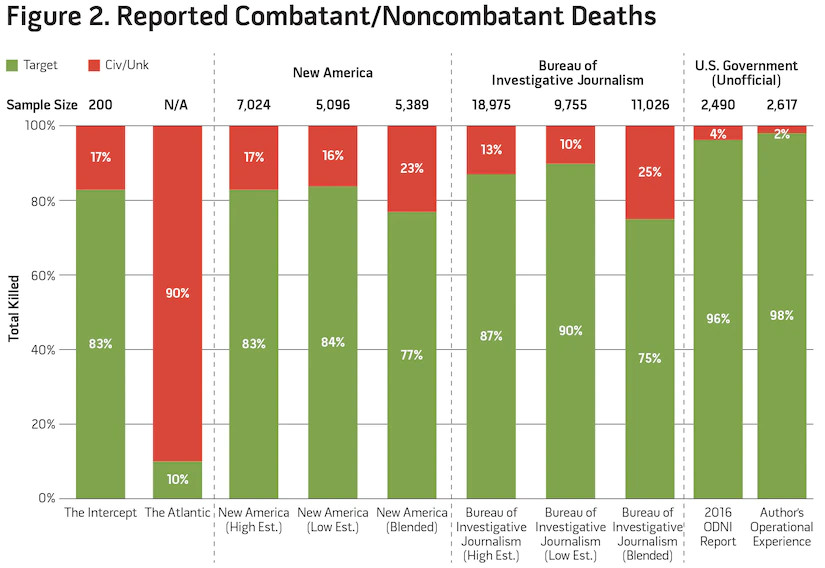
Figure 2 analyzes sample data of RPA strikes (comparing reported enemy deaths to those of assessed noncombatants) from four media outlets, the Office of the Director of National Intelligence (ODNI), and my own personal experience having commanded and directed over 6 years of RPA strikes across seven countries. Of note, because the duration of reporting periods differs among all sources, the reported sample size is included in the figure.
Within these reports, even from within specific organizations, is a wide disparity of data as expressed by author Cora Currier, stating “the estimates are largely compiled by interpreting news reports relying on anonymous officials or accounts of local media, whose credibility may vary.”50 Additionally, because the data range from some individual sources (New America Foundation and the Bureau of Investigative Journalism) is so broad, the figure reflects low estimates, high estimates, and a blended sample that reflects the lowest total number of personnel killed with the highest claim of civilian casualties.51 With media reports of civilian casualties ranging from 10 percent through 90 percent of all strike deaths, compared to ODNI and personal accounts of 4 percent to 2 percent noncombatant deaths, respectively, the disparity of accounting is apparent.52 Additionally within media reports, there is no distinction annotated on how the recorded data was confirmed as RPA strikes, vice any other type of air-to-ground or surface-to-surface engagement. Notably, in searching for accurate data through an Internet search of “drone civilian deaths,” the openly available ODNI report does not even occur within the first 100 search items, further illustrating this narrative bias. Unfortunately, the data from government sources is completely overshadowed by an ill-informed media narrative that results from disparate reports, sensationalism, and a lack of transparency.
This narrative is further refined through the use of popular media, to include television, books, and movies that deal with drone warfare. According to Paul Rich, media and feature films can be “highly influential in framing major political issues.”53 This is certainly the case with the use of armed RPA and has bolstered a malign narrative that, as illustrated by Guardian columnist Henry Barnes, “forgets there’s someone at the controls, emphasizing the alien nature of a remote, robotic death.”54 This narrative has been further bolstered by legal officials declaring that RPA strikes are “kind of antiseptic . . . like a video game . . . like Call of Duty.”55 Mark Bowden goes so far as to state that in war the use of RPA strikes “ignores the spirit of the contest.”56 These cultural implications of “remote death” drive a biased and often false narrative. Without transparent, informative, and accountable engagement by the U.S. Government, the niche capability provided by armed RPA operations is vulnerable among both domestic and international information spheres, increasing the political risk of use when deemed appropriate. Furthermore, in order to counter this malign narrative and maximize the strategic influence of armed RPA, policymakers and senior leaders must transparently assess the proper use of this capability and resist historical tendencies based on incomplete characterizations of the mission, the operating environment, and the policy objectives.
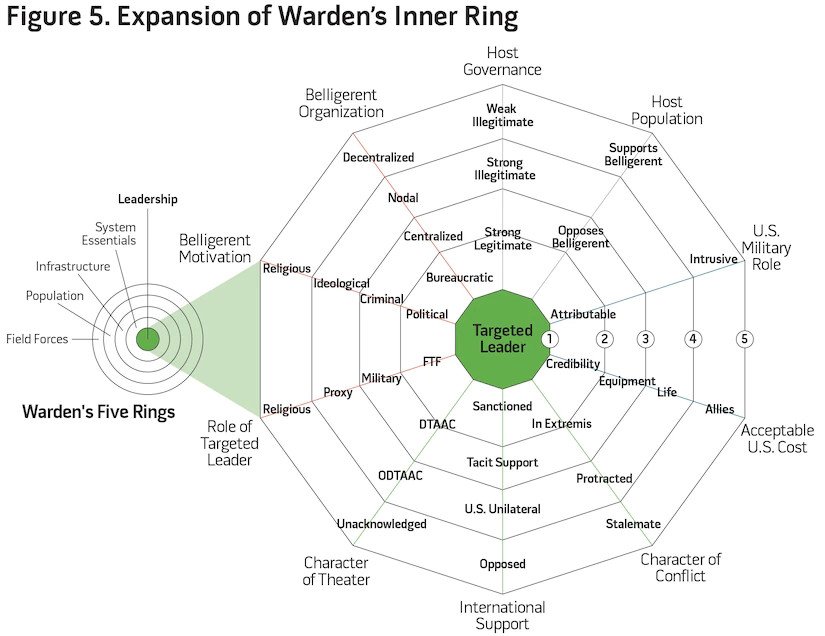
There exists a third risk factor to the use of armed RPA that is even more critical than either the opacity of policy or the malign narrative. This is the mischaracterization of the operating environment that creates an inarticulate strategy, directs improper use of force (to include armed RPA), and detracts from policy objectives. Reflecting on the conventional targeting theory prior to 9/11, we see the concepts of effects-based operations, John Boyd’s OODA Loop, and John Warden’s Five Rings.57 Because of the rapid expansion of RPA operations (and CT strikes) in Afghanistan and Iraq through 2003, planners and senior leaders remained wedded to pre-9/11 concepts. This lag led to a dependence on decapitation strikes to support Warden’s dictum that the enemy leader and his command structure are the only entities capable of “determining a nation’s (or group’s) will to fight.”58 But these assertions did not hold, and they relied on a mischaracterization of the enemy and the operating environment. After 9/11, the United States was no longer fighting a conventional highly centralized, state-managed force. Instead, the United States found itself matched against a disparate, decentralized, religiously based terrorist movement that garnered support from the indigenous population.
From the beginning of the war on terror, the United States became fixated on decapitation strikes and failed to comprehensively assess the role of RPA strikes to achieve strategic objectives in support of policy ends. Moreover, without a coherent policy and war termination criteria, military planners were relegated to decapitation operations (including direct action special operations and conventional operations) that did not address root causes of the conflict. James Kiras captures this sentiment, asserting, “decapitation strikes are appealing precisely because they compress the vertical and horizontal dimension of strategy into a single flat line in which actions, unburdened by friction or imperfect knowledge and unimpeded by political considerations, achieve their effects against an enemy system in a preordained manner.”59 Unfortunately, decapitation targeting theory does not target the foundational principles that foment instability and violence in contemporary CT/counterinsurgency (COIN) campaigns: the malign ideology and its psycho-social influence on the host-nation population. Political scientist Robert Pape captured this sentiment in 1996, stating, “decapitation is not likely to coerce adversaries and can be counterproductive.”60
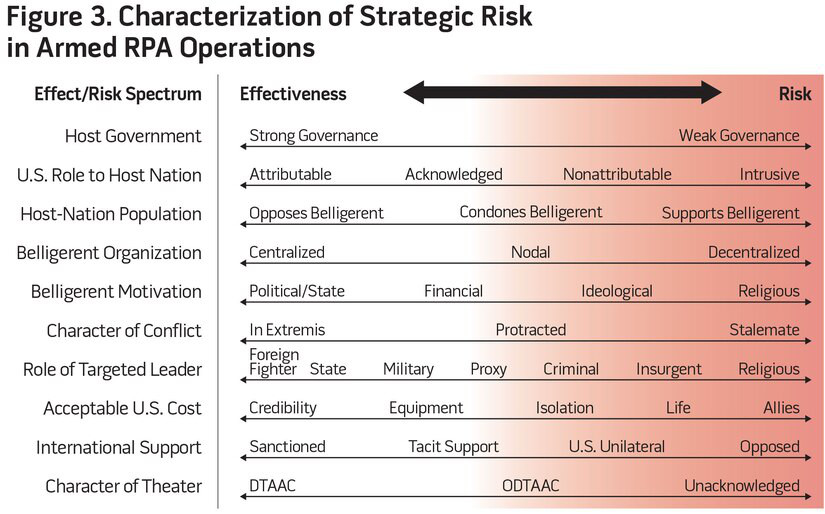
In order to fully assess the appropriate role (or lack thereof) of RPA decapitation strikes as a policy tool at the strategic level, senior leaders must fully consider that additional risk factors, such as social, political, cultural, and economic characteristics, shape military responses.61 As a result of the mischaracterization of these risk factors within the operating environment and false assumptions of the efficacy of decapitation strikes in current conflicts, the U.S. Government has not provided a clear explanation of how RPA strikes will be coordinated with broader foreign policy objectives.62 Moving forward, before the adoption of a national strategy that includes leadership decapitation operations, it is imperative that policymakers understand the complex interaction between effectiveness and the above risk factors. Figure 3 details this interaction using an effect/risk spectrum based on 10 characteristics within the operating environment.
The strategic risk model is not intended to be a checklist-based examination on the efficacy and risk of RPA decapitation strikes, but instead to provide analytical context to policy decisions. The model asserts that an attributable U.S. strike against a leader within a strong bureaucratic state, sanctioned by international support, within a declared theater of conflict is likely the most effective and least risky type of decapitation strike. In contrast, the model asserts that the least effective (and highest risk) decapitation operations are against leaders of decentralized, religiously motivated organizations with weak host-nation governance and strong host-nation popular support. Adding to the challenge, the complex interactive relationship between risk and effectiveness is neither binary nor directly opposed; it is unique to each operational environment, pointing to a greater need for constructive analysis and dialogue prior to commencement of decapitation strikes.
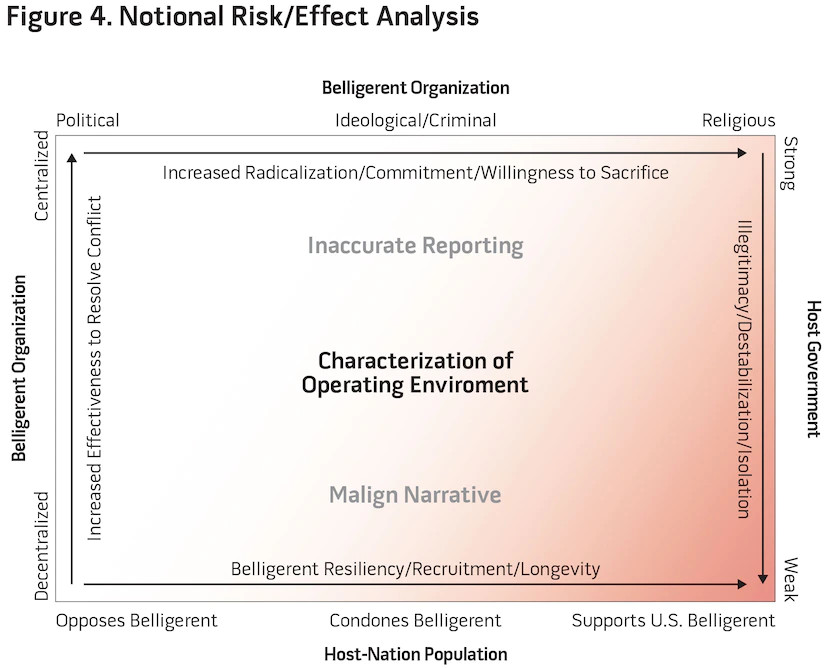
Figure 4 represents this notional risk/effect analysis portraying the complex interactions of the operating environment based on 4 of the 10 principles. In understanding and accounting for inherent risks of RPA strikes (policy opacity, inaccurate reporting, and malign narrative), policymakers must deliberately forecast and anticipate the effects on popular sentiment, the host-nation government, the belligerent organization, and the belligerent’s motivation. In this figure, we highlight those characteristics that increase strategic risk, manifesting in potential unintended consequences and what the CIA refers to as “blowback.”63
Figure 4 also highlights increased radicalization and host-nation illegitimacy as the two greatest strategic risks associated with armed RPA operations. Within contemporary CT/COIN operational environments, these two factors manifest in increased belligerent recruitment, resilience, and commitment, while concomitantly delegitimizing and isolating the host-nation government and security apparatus. Many of today’s CT/COIN environments are defined by weak governance, popular acquiescence, and support to belligerents and the targets represent decentralized, religiously motivated ideologies, creating a destructive cycle that actually detracts from policy goals. Moreover, while the preponderance of scrutiny on RPA operations derives from civilian casualties, in this destructive cycle, even successful RPA strikes (that is, targeted individual killed with no collateral damage) could result in blowback. For example, a successful U.S. RPA strike against a belligerent leader often devolves into a narrative that highlights U.S. overreach, further delegitimizing the host-nation government. This principle is characterized by Mark Bowden, writing, the “political message [of an RPA strike] emphasizes the disparity in power between the parties and reinforces popular support for the terrorists, who are seen as David fighting Goliath.”64 Without an effective US counternarrative, this popular sentiment foments instability and isolation of the host nation.
In order to mitigate the potential for blowback, and concurrent with any proposal to conduct decapitation operations, policymakers must characterize the operational environment to understand the likelihood of success and its complex association with the strategic risk. While Warden’s theories of decapitation strikes continue to drive contemporary airpower theory since 9/11, they do not account for these characteristics within the operational environment. In today’s CT and COIN campaigns, this mischaracterization often creates more instability, host-nation illegitimacy, and strategic risk to U.S. policy goals. An expansion on the theories of Warden and other advocates of decapitation strikes must capture the analysis of the operating environment prior to creation of strategy.
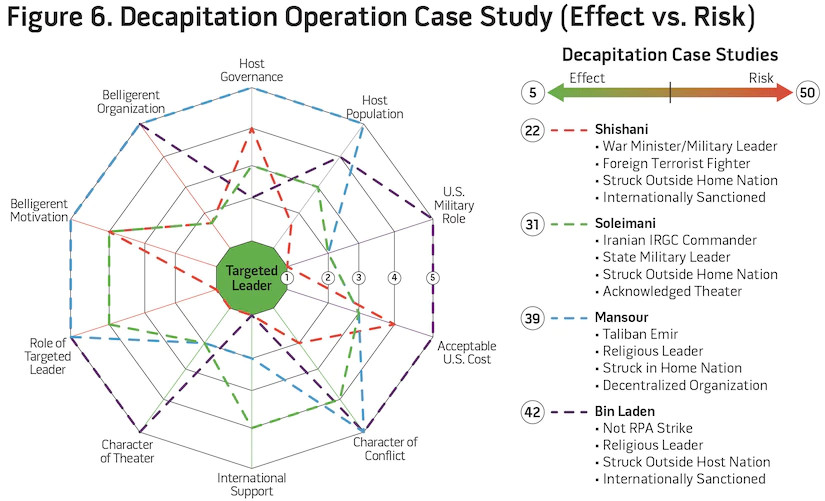
Expanding on the theories of Warden, figure 5 reorganizes the risk characteristics, providing an analytical model to capture the risk characterization of leadership strikes inherent in his Five Rings model. Because neither model is prescriptive, policymakers must understand the complex relationship between the likelihood of effective decapitation strikes and the opposing risk. While the models above are primarily subjective, is flexible enough to represent a more objective analysis by measuring the overall effectiveness/risk spectrum based on the 10 characteristics. By assigning a weighted numerical value to each characteristic (situationally dependent), planners can inform policy decisions based on likelihood of success versus inherent risk. Figure 6 displays examples of four notable decapitation operations. While three of the four were in fact RPA strikes, distinct characteristics (including the highest risk) from the operation to capture and/or kill bin Laden illuminate the need for subjective decisionmaking ability instead of a purely objective analysis.
As the case studies show, using the weighted risk of each characteristic, certain aspects of decapitation operations drive likelihood of success, while others drive risk. Whereas the decision calculus and interplay of these complex relationships is difficult to ascertain, certain assertions can be made about the efficacy of a given strategy. For example, based on the model’s additive score of 22, the airstrike against Abu Omar al-Shishani, the IS minster of war, had a higher chance of success (in influencing IS) compared to a relatively lower risk to operational environment (blowback). According to the U.S. special operations task force commander that directed the operation, the death of Shishani resulted in a significant degradation to IS military capability.65 In contrast, the strike against Taliban Emir Mullah Akhtar Mansour in May 2016, with an assessed score of 39, retained a high risk of blowback (and failure to achieve lasting effects on the Taliban), regardless of whether the strike itself was tactically successful. This objective postmortem of historic strikes using the model is useful to assess proposed roles of military force in current and future conflicts. Because these models are designed for risk analysis at the policy and strategic level, they deliberately avoid discussion of “risk to force” and other tactical risk factors that emerge through joint operational and tactical planning. Understanding the importance of strikes against leadership targets (akin to Warden’s model), these models expand the analysis of the operating environment and highlight those unique characteristics that will likely neuter effective decapitation operations from the strategic level.
Though armed RPA will undoubtedly continue to play a role in U.S. foreign policy, the imperative for success lies not in the hands of the RPA operators, but in the characterization of the environment and the strategy nested therein to support policy goals. Prior to decisions to use force, including armed RPA, policymakers must examine and debate appropriateness to a given situation based on informed analysis of the operating environment. Too often, without a comprehensive whole-of-government effort (based on an understanding of the complexity of effects versus risk), the tendency to employ RPA as the tool of choice alone results in further instability and strategic risk to policy objectives.
Conclusion and Recommendations
While RPA represent an evolution in military capability, they have revolutionized the U.S. ability to project power. In so doing, the use of armed RPA and decapitation strikes as an intrinsic policy, absent a whole-of-government strategy, increases risk to national policy objectives, destabilizes fragile regions, and isolates key partners. With this approach, policymakers risk defaulting to military force as the preferred strategy, instead of analyzing and utilizing other means of national power. With less analysis on other instruments of national power, military force may result in longer term damage to comprehensive national policy goals.
To mitigate this temptation, policymakers must incorporate the unique capabilities of RPA, not to supplant national strategy but as one facet of a broad effort to attain political ends through concerted use of all available instruments of national power. Additionally, greater transparency on the use of armed RPA is necessary to dispel malign narratives and to maximize the effectiveness of this niche strategic capability. In concert with robust analysis and debate on the appropriate use of military force, policymakers and senior leaders must characterize the operational environment to determine the efficacy and risk of military force to address a given security challenge. Complementing historic theories of airpower employment, contemporary theorists must examine the social, political, security, and psychological characteristics of the targeted individual’s environs to determine if decapitation strikes would indeed support or detract from stated policy goals. In future policymaking discussions, instead of debating the role of RPA strikes as a strategic tool, the more appropriate consideration must analyze the efficacy of the overall strategy to meet U.S. policy ends. Lacking transparency and executed without a clearly identified endstate and coordinated whole-of-government strategy, RPA strikes alone could be detrimental. Comparatively, the evolution in character of war displayed through employment of armed RPA, as part of a comprehensive whole-of-government strategy, provides niche, low-risk strategic capability to support policy goals and mitigate immediate threats to our nation, our partners, our interests, and our allies.
*About the author: Lieutenant Colonel Roderic K. Butz, USAF, wrote this essay while a student at the Army War College. It tied for first place in the 2020 Secretary of Defense National Security Essay Competition.
Source: This article was published in Joint Force Quarterly 100, which is published by the National Defense University.
Notes
1 Mark Bowden, “How the Predator Drone Changed the Character of War,” Smithsonian Magazine, November 2013, available at <https://www.smithsonianmag.com/history/how-the-predator-drone-changed-the-character-of-war-3794671/>.
2 Warren Bass, “How One Predator Mission in 2000 Helped Dictate U.S.’s Drone Path,” Wall Street Journal, July 26, 2014, available at <www.marketwatch.com/story/till-911-washington-was-sharply-divided-over-drones-2014-07-26>.
3 Richard Whittle, “Timeline of Key Events,” Predator, available at <http://richardwhittle.net/#timeline2>.
4 “Drone Warfare,” The Bureau of Investigative Journalism, available at <www.thebureauinvestigates.com/projects/drone-war>.
5 Bowden, “How the Predator Drone Changed the Character of War.”
6 Ann Wright, “Killer Drones and the Militarization of U.S. Foreign Policy,” The Foreign Service Journal, June 2017, available at <https://www.afsa.org/killer-drones-and-militarization-us-foreign-policy>.
7 Ibid.
8 Public Law 107-40, September 18, 2001, 115 Stat. 224, 107th Cong., available at <https://www.congress.gov/107/plaws/publ40/PLAW-107publ40.pdf>.
9 Author experience as operations officer and commander of Air Force Special Operations MQ-9 squadron, June 19, 2013–June 5, 2019; Rebecca Gordon, “How the U.S. Military Came to Embrace Extrajudicial Killings,” The Nation, July 18, 2016.
10 Presidential Executive Order 12333, United States Intelligence Activities (Washington, DC: The White House, December 4, 1981), available at <https://www.archives.gov/federal-register/codification/executive-order/12333.html>.
11 Andru E. Wall, “Demystifying the Title 10–Title 50 Debate: Distinguishing Military Operations, Intelligence Activities & Covert Action,” Harvard National Security Journal 3, no. 1 (2011), available at <https://harvardnsj.org/wp-content/uploads/sites/13/2012/01/Vol-3-Wall.pdf>.
12 “What Are Jus ad Bellum and Jus in Bello?” International Committee of the Red Cross, January 22, 2015, available at <https://www.icrc.org/en/document/what-are-jus-ad-bellum-and-jus-bello-0>.
13 Sarah Kreps, “The Use of Unmanned Aerial Vehicles in Contemporary Conflict: A Legal and Ethical Analysis,” Polity 44, no. 2 (April 2012), 261.
14 Bowden, “How the Predator Drone Changed the Character of War.”
15 Whittle, “Timeline of Key Events.”
16 Ibid.
17 National Commission on Terrorist Attacks Upon the United States, The 9/11 Commission Report (Washington, DC: National Commission on Terrorist Attacks Upon the United States, 2004), 212, available at <https://govinfo.library.unt.edu/911/report/911Report_Ch6.htm>.
18 Ibid.
19 Jessica Purkiss, “Obama’s Covert Drone War in Numbers: Ten Times More Strikes Than Bush,” The Bureau of Investigative Journalism, January 17, 2017, available at <www.thebureauinvestigates.com/stories/2017-01-17/obamas-covert-drone-war-in-numbers-ten-times-more-strikes-than-bush>.
20 Simon Frankell Pratt, “Norm Transformation and the Institutionalization of Targeted Killing in the U.S.,” European Journal of International Relations 25, no. 3 (November 2018), 9.
21 Abigail HallBlanco, “The Drone President,” The Washington Examiner, January 2, 2017, available at <www.washingtonexaminer.com/the-drone-president>.
22 Jack Serle, “Obama Drone Casualty Numbers a Fraction of Those Recorded by the Bureau,” The Bureau of Investigative Journalism, July 1, 2016, available at <www.thebureauinvestigates.com/stories/2016-07-01/obama-drone-casualty-numbers-a-fraction-of-those-recorded-by-the-bureau>.
23 HallBlanco, “The Drone President.”
24 “Pentagon Plans for Cuts to Drone Budgets,” Military.com, January 2, 2014, available at <www.military.com/dodbuzz/2014/01/02/pentagon-plans-for-cuts-to-drone-budgets>.
25 Presidential Policy Guidance, Procedures for Approving Direct Action Against Terrorist Targets Located Outside the United States and Areas of Active Hostilities (Washington, DC: The White House, May 22, 2013), available at <https://www.justice.gov/oip/foia-library/procedures_for_approving_direct_action_against_terrorist_targets/download>.
26 Executive Order, United States Policy on Pre- and Post-Strike Measures to Address Civilian Casualties in U.S. Operations Involving the Use of Force (Washington, DC: The White House, July 1, 2016), available at <https://obamawhitehouse.archives.gov/the-press-office/2016/07/01/executive-order-united-states-policy-pre-and-post-strike-measures>.
27 Dan De Luce and Seán D. Naylor, “The Drones Are Back,” Foreign Policy, March 26, 2018, available at <https://foreignpolicy.com/2018/03/26/the-drones-are-back/>.
28 Charlie Savage, “Trump Poised to Drop Some Limits on Drone Strikes and Commando Raids,” New York Times, September 21, 2017, available at <www.nytimes.com/2017/09/21/us/politics/trump-drone-strikes-commando-raids-rules.html>.
29 Stephen Tankel, “Donald Trump’s Shadow War,” Politico, May 9, 2018, available at <www.politico.com/magazine/story/2018/05/09/donald-trumps-shadow-war-218327>.
30 Peter Harris, “Why Trump’s Drone War Shows He Wanted American Global Supremacy,” National Interest, November 28, 2019, available at <https://nationalinterest.org/feature/why-trump’s-drone-war-shows-he-wants-american-global-supremacy-100647>.
31 Diana Stancy Correll, “Armed Drones to Fly Out of Niger Air Base Now Operational After Delayed Completion,” Air Force Times, November 1, 2019, available at <www.airforcetimes.com/flashpoints/2019/11/01/armed-drones-to-fly-out-of-niger-air-base-now-operational-after-delayed-completion/>.
32 Jacqueline Hazelton, “Drones Are the New Face of U.S. Foreign Policy. What Good Are They?” Lawfare, July 23, 2017, available at <www.lawfareblog.com/drones-are-new-face-us-foreign-policy-what-good-are-they>.
33 Author experience, 2013–2019.
34 Meritorious Service Medal, June 5, 2019.
35 Patrick Mills et al., Estimating Air Force Deployment Requirements for Lean Force Packages (Santa Monica, CA: RAND, 2017), 36.
36 Christopher (last name protected), operations officer, Air Force MQ-9 launch and recovery squadron, interview by author, Cannon Air Force Base, NM, March 2020.
37 Winslow Wheeler, “2. The MQ-9’s Cost and Performance,” Time, February 28, 2012, available at <https://nation.time.com/2012/02/28/2-the-mq-9s-cost-and-performance/>.
38 Keith S., “What Is an Afterburner and How Long Can a Jet Fly on Afterburner?” Stack Exchange: Aviation, November 10, 2015, available at <https://aviation.stackexchange.com/questions/17286/what-is-an-afterburner-and-how-long-can-a-jet-fly-on-afterburner>.
39 Mills et al., Estimating Air Force Deployment Requirements for Lean Force Packages, 36.
40 Gordon Lubold and Warren P. Strobel, “Secret U.S. Missile Aims to Kill Only Terrorists, Not Nearby Civilians,” Wall Street Journal, May 9, 2019, available at <www.wsj.com/articles/secret-u-s-missile-aims-to-kill-only-terrorists-not-nearby-civilians-11557403411>.
41 Helene Cooper, “U.S. Strikes in Somalia Kill 150 Shabab Fighter,” New York Times, March 8, 2016, available at <www.nytimes.com/2016/03/08/world/africa/us-airstrikes-somalia.html>.
42 Jeremy Scahill, “The Assassination Complex,” The Intercept, October 15, 2015, available at <https://theintercept.com/drone-papers/the-assassination-complex/>.
43 David Oakley, “The Problem of a Militarized Foreign Policy for America’s Premier Intelligence Agency,” War on the Rocks, May 2, 2019, available at <https://warontherocks.com/2019/05/the-problems-of-a-militarized-foreign-policy-for-americas-premier-intelligence-agency/>.
44 James D. Kiras, Special Operations and Strategy: From World War II to the War on Terrorism (Abingdon, UK: Routledge, 2006), 3.
45 Rachel Stohl, An Action Plan on U.S. Drone Policy: Recommendations for the Trump Administration (Washington, DC: Stimson Center, June 2018), 20.
46 Jordan Mintzer, “‘National Bird’: Berlin Review,” Hollywood Reporter, February 14, 2016, available at <www.hollywoodreporter.com/review/national-bird-berlin-review-865191>; Medea Benjamin, “Good Drone, Bad Drone: How to Fix the Drone PR Problem,” Time, July 9, 2014, available at <https://time.com/2970027/drones-pr-problem/>.
47 Kreps, “The Use of Unmanned Aerial Vehicles in Contemporary Conflict,” 276.
48 Ibid., 275.
49 “Secret U.S. Drone Program Still Getting Away with Killing Children,” Amnesty International, available at <https://www.amnestyusa.org/secret-us-drone-program-still-getting-away-with-killing-children/>.
50 Cora Currier, “Everything We Know So Far About Drone Strikes,” ProPublica, February 15, 2013, available at <https://www.propublica.org/article/everything-we-know-so-far-about-drone-strikes>.
51 Peter Bergen, David Sterman, and Melissa Salyk-Virk, America’s Counterterrorism Wars (Washington, DC: New America Foundation, 2020), “Methodology,” available at <https://www.newamerica.org/in-depth/americas-counterterrorism-wars/methodology/>; “Drone Warfare,” The Bureau of Investigative Journalism, available at <www.thebureauinvestigates.com/projects/drone-war>.
52 Ryan Devereaux, “Obama Administration Finally Releases Its Dubious Drone Death Toll,” The Intercept, July 1, 2016, available at <https://theintercept.com/2016/07/01/obama-administration-finally-releases-its-dubious-drone-death-toll/>; Conor Friedersdorf, “Obama’s Weak Defense of His Record on Drone Killings,” The Atlantic, December 23, 2016, available at <www.theatlantic.com/politics/archive/2016/12/president-obamas-weak-defense-of-his-record-on-drone-strikes/511454/>; Office of the Department of National Intelligence, “Summary of Information Regarding U.S. Counterterrorism Strikes Outside Areas of Active Hostilities,” 2016, available at <https://www.dni.gov/files/documents/Newsroom/Press%20Releases/DNI+Release+on+CT+Strikes+Outside+Areas+of+Active+Hostilities.PDF>.
53 Paul B. Rich, “Cinema, Drone Warfare and the Framing of Counter-Terrorism,” Defense & Security Analysis 34, no. 2 (2018), 144.
54 Henry Barnes, “Kill Shots: Why Cinema Has Drone Warfare in its Sights,” The Guardian, April 14, 2016, available at <www.theguardian.com/film/2016/apr/14/eye-in-the-sky-london-has-fallen-drone-films>.
55 Mark Bowden, “The Killing Machines: How to Think About Drones,” The Atlantic, September 2013, available at <www.theatlantic.com/magazine/archive/2013/09/the-killing-machines-how-to-think-about-drones/309434/>.
56 Ibid.
57 Mike Pietrucha, “The Five-Ring Circus: How Airpower Enthusiasts Forgot About Interdiction,” War on the Rocks, September 29, 2015, available at <https://warontherocks.com/2015/09/the-five-ring-circus-how-airpower-enthusiasts-forgot-about-interdiction/>.
58 Jenna Jordan, Leadership Decapitation: Strategic Targeting of Terrorist Organizations (Stanford: Stanford University Press, 2019), 11.
59 Kiras, “Special Operations and Strategy,” 3.
60 Patrick B. Johnston, “Assessing the Effectiveness of Leadership Decapitation in Counterinsurgency Campaigns,” Belfer Center for Science and International Affairs, 1, available at <https://scholar.harvard.edu/files/johnston/files/decapitation.pdf>.
61 Kiras, Special Operations and Strategy, 4.
62 Micah Zenko, Reforming U.S. Drone Strike Policies, Council Special Report No. 65 (Washington, DC: Council on Foreign Relations, January 2013), 3.
63 Mehdi Hasan and Dina Sayedahmed, “Blowback: How Drones, Coups, and Invasions Just Create More Violence,” The Intercept, available at <https://theintercept.com/2018/01/22/blowback-cia-drones-middle-east/>.
64 Bowden, “The Killing Machines.”
65 Ryan (last name protected), commander, Special Operations Task Force–Operation Inherent Resolve, interview by author, March 2020.