Enabling Organizational Resilience Through Communication And Information Systems Design – Analysis
By Joseph Long*
Introduction
The Canadian Armed Forces’ (CAF) operational environment is becoming more ambiguous and subject to rapid change. Leaders and organizations are expected to confront situations of greater complexity than ever before. The contemporary operational landscape involves violent extremist organizations, climate change, cyber threats, humanitarian emergencies, and other new and unique challenges.1 The Department of National Defence and the CAF are doing an excellent job training, educating, and equipping members for expected operational challenges, but the current Communication and Information Systems (CIS) used by those members and organizations are not built to best enable operations.
This article will analyze three adaptive, resilient organizations celebrated for success at the Tactical, Operational, and Strategic levels, paying particular attention to their use of Communications and Information Systems. Extracting lessons learned and best practices will show how adaptive organizations can best be enabled by CIS that creates shared consciousness, has low barriers to entry, and duplicates natural communication patterns. The article will also examine the trade-offs that must be accepted for resilience, and show how applying these lessons will enhance future CAF CIS development and design.
The Contemporary Operational Environment
Environmental Complexity
In the contemporary operational environment, State and non-state actors are becoming increasingly more powerful and interconnected. These actors, unable to mass power to enable a traditional ‘force on force’ confrontation against Western industrial military might, use any and all techniques available to gain an advantage. Global connectedness and the speed of communication exponentially increases the number and variety of actors with their competing interests who are able to participate in any given conflict.
The old ‘top-down’ command model where commanders could read carefully-collected reports from subordinates, concoct elaborate and intricate plans, and execute operations on a deliberate timetable no longer exists. In order to be successful, military forces must integrate a wide variety of knowledge and expertise, rapidly fusing diverse viewpoints to instantaneously react to changing conditions. Decision-making authorities have been pushed lower, as deployed detachments become smaller and required reaction times become shorter.
Resiliency
The new Canada Defence Policy Report – Strong, Secure, Engaged, calls this “…a new approach to Defence: Anticipate. Adapt. Act,” clarifying, “…anticipating emerging threats and challenges is fundamental to Canada’s security. The Defence Team will improve its ability to provide timely information to decision-makers, allowing the Government to identify and understand emerging events and crises, respond appropriately, and minimize the destructive effects of prolonged conflict.”
This ability to rapidly and appropriately react to changing situations can be called “agility” or “resilience.”2 When situations become more complex than any one commander can completely understand and oversee, decision-making powers need to be distributed to lower levels, with the knowledge, intelligence, and context to best enable these subordinate decision-makers. Rapidly changing situations also require rapidly changing teams and structures to address these changes. Specialists, enablers, and operators from various units, governmental and non-governmental organizations (NGOs), and geographical areas must rapidly cohere into an effective force and then just as rapidly disband and reform in other ways for the next mission.
Command vs Network
This changing organizational dynamic by which organizations morph and reform is only possible when members are empowered to make horizontal connections enabled by the trust of their superiors. Members at all levels of the hierarchy need to develop relationships outside of their formal chain of command to facilitate faster and more accurate passing of information to generate context for decisions. Expertise can easily be accessed when and as needed, from the most capable source. This networked organization is illustrated in the following diagrams:3
Figure 1: Command
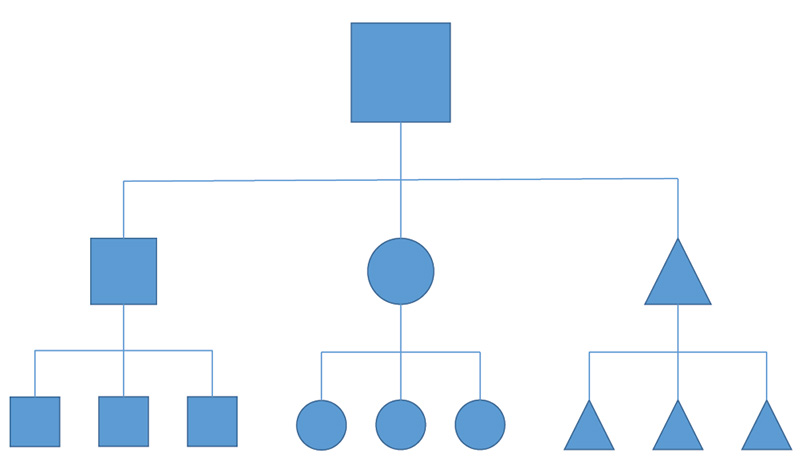
Figure 2: Command of Teams
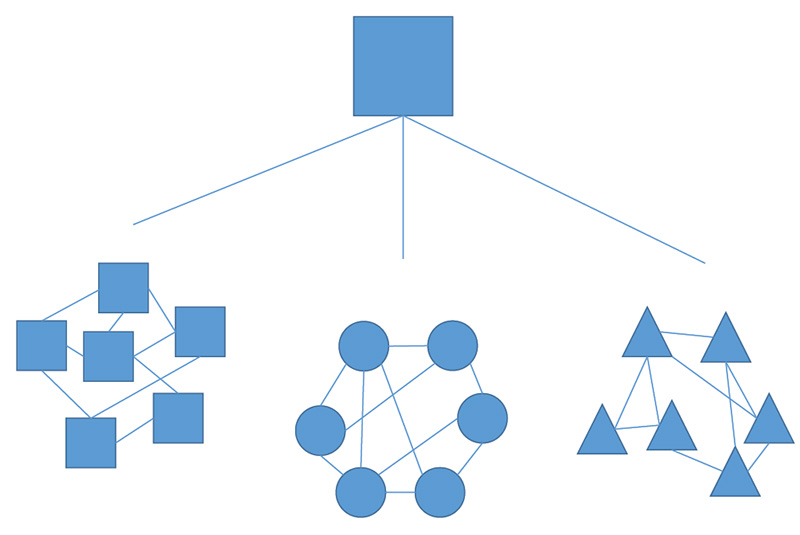
Figure 3: Team of Teams
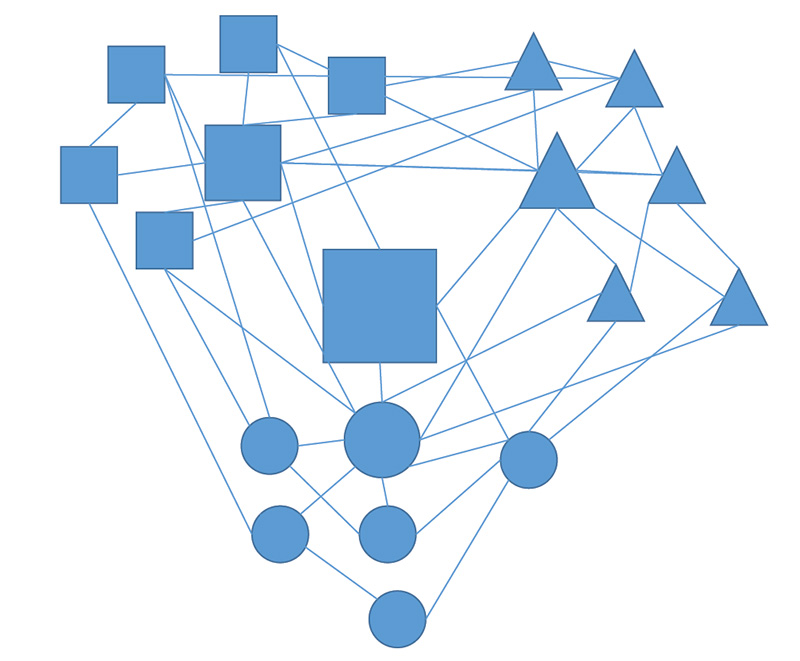
Shared Consciousness
The “team of teams” networked structure, while important for decision making and coordinating action, adds the most value to a networked organization by enabling a “shared consciousness.” Every member of a resilient organization needs to have a shared perception of the situation, mission, and context in which the organization operates. As decision-making is delegated to lower levels, the decision-makers (note that the Defence Policy Review refers to “decision-makers,” not “commanders,”4) need to have the information required to correctly and optimally decide in line with the organization’s requirement.
Shared consciousness also reduces friction internal to organizations. Disputes between sub-units for shared resources can be minimized when each sub-group understands why each other sub-group is requesting the resource, as well as how other groups will use it to accomplish the shared mission.
Case Studies

In order to illustrate important factors in designing and maintaining resilient CIS, this article will examine three successfully resilient organizations. The Cajun Navy and Occupy Sandy will illustrate resiliency in rapid reaction forces achieving tactical success. General Stanley McChrystal’s description of his Joint Special Operations Task Force in Iraq is an excellent example of a military formation achieving operational success. Finally, the open team developing the popular Linux computer operating system ‘kernel’ [the foundational layer of an operating system – Ed.] will show resilience in a large “strategic level” and capability development organization.
Cajun Navy and Occupy Sandy
One of the most striking examples of technology-enabled resiliency and adaptations in recent memory is the emergence of community-based aid groups in the aftermath of natural disasters in the United States.
In late-October 2012, Hurricane Sandy struck the Eastern Seaboard of North America, killing more than 150 people, destroying at least 650,000 houses, and causing more than $71.4 billion (USD) in damage in the US alone.5 As official aid organizations struggled to cope, and within hours after hurricane landfall, members of the Occupy Wall Street [Occupy Sandy] movement on social media began coordinating ad-hoc aid and assistance. Within days, an estimated 60,000 volunteers were providing direct aid (food, water, warmth), medical and psychological care, remediation and rebuilding support, case management and legal assistance, as well as fundraising.6
In a common thread, emergent citizen organizations have been observed following other major disasters, often taking advantage of social media to coordinate efforts. A similar group, the Cajun Navy, a loose grouping of volunteers with private fishing boats, conducted search and rescue missions alongside trained first responders7 in Texas and Louisiana after Hurricane Harvey struck the southern US in the summer of 2017. Coordinating all missions with free smartphone apps, hundreds of volunteers rescued thousands of fellow citizens. The volunteers were eventually officially recognized by the federal government for saving thousands of lives.
General McChrystal’s “Team of Teams”
In 2003, then-Major General, now retired General Stanley McChrystal took command of a Joint Special Operations Task Force in Iraq, transforming it from a reactive, ‘siloed’ organization into an efficient and effective counter-terrorism force, ultimately finding and killing Al-Qaeda-in-Iraq leader Abu Musab al-Zarqawi. In a new book, Team of Teams, General McChrystal describes steps he took to transform his efficient but inflexible and hierarchical organization into the titular “Team of Teams,” able to rapidly adapt and react to new intelligence and operational situations.
While General McChrystal’s book contains many excellent lessons for the manager and leader creating adaptive organizations, clearly explaining the ‘how’ and ‘why’ of procedural, cultural, and organizational changes, relatively little space is spent describing the communications and information technology behind the transformation. What little there is, however, describes a technical architecture very different from most enterprise-level CIS. In describing his daily Operations and Intelligence (O&I) meetings, daily video conferences virtually attended by Task Force members at all levels, partner agencies, and command staff, General McChrystal writes: “In time, people came to appreciate the value of systemic understanding. O&I attendance grew as the quality of the information and interaction grew. Eventually we had seven thousand people attending almost daily for up to two hours (emphasis added).”8 It almost goes without saying that a seven-thousand person two-hour video call requires unique CIS solutions and technological considerations.
Linux
In 1991, 21 year-old Finnish university student, Linus Torvalds, began work on a project to develop an operating system for a new computer he had received. Thinking that other computer users might want to use it as well, he released the code for free public use. Eventually, others began collaborating on-line to introduce improvements, always maintaining the spirit of open collaboration. Today Linux-based operating systems are the most widely used operating systems in the world, used in all Android-based personal devices, most web servers, the International Space Station,9 and all the world’s 500 most powerful supercomputers, as of 2017.10
The adaptability and resiliency of the Linux kernel is due to the on-line collaborative ‘open source’ development process, where the entire code is freely available and modifiable, and the on-line development community can suggest and make changes to the official code, which is reviewed by other trusted community members before implementation. In 2006, it was estimated that over 13,500 developers from more than 1300 companies have contributed to the code since 2005.11
Principles of CIS-Enabled Resilience
While the Cajun Navy, General McChrystal’s Joint Special Operations Task Force, and the Linux kernel development community have wildly different organizational structures, cultures, goals, and methods, there are striking similarities. Each has emerged in response to uniquely-challenging situations, all place a premium on collaboration and communication, and all have demonstrated remarkable resilience and adaptability, leading to success.
On close examination, it becomes evident that each organization uses uniquely-adapted CIS to enable the high levels of communication and collaboration required, and that specific patterns of use and technological adoption emerge. These patterns form the basis of this article. Creating CIS for adaptive and resilient organizations requires different methods and priorities than traditional military communications systems planning and design. Specifically, each of these organizations uses CIS that creates shared consciousness, minimizes barriers to participation, and duplicates natural communication patterns at all levels.
Build the Market Square(s)
Shared consciousness is the most important factor in allowing an organization to effectively analyze information and respond to new challenges. While even the most rigid and inflexible organizations will have some level of shared consciousness (often only in the form of an organization chart and position Terms of Reference), successful agile organizations take this to next levels. When planning CIS to support an agile organization, one of the questions that must be asked is, “Where will the shared consciousness exist?”, or “Where is the ‘market square’ in which diverse teams can share knowledge?”
The ‘Open Source’ software development model championed by the Linux kernel development community is based upon a commitment to shared knowledge. All production code, proposed changes, and most work discussions are open for viewing by anyone interested. The ‘market square’ exists in two places: GitHub, an on-line read-only code management database containing the Linux kernel, as well as proposed and past changes,12 and mailing lists to which interested developers can subscribe. Out of these easily-accessed forums, a large number of specialist sub-communities, tutorials, and working groups have emerged to more effectively concentrate and develop expertise.13
General McChrystal describes the success of his O&I meetings as, “…the most critical element of [the] transformation – the heart muscle of the organism we sought to create and the pulse by which it would live or die.”14 The O&I, physically or virtually attended by thousands of people inside and outside of the Task Force, ensured common information and context throughout the force. At the tactical level, the Cajun Navy after Harvey relied upon two key platforms: Zello, a smartphone ‘walkie-talkie’ app used to create dispatch channels, and Glympse, a shared positional awareness app.15 These modern takes on old-fashioned means (radio voice traffic and location reporting) enabled planning and coordination of thousands of rescues.
At a certain size, the ‘market squares’ can get unwieldy and congested. Any CIS for resilient organizations must pay attention to both the centralized knowledge sharing forums, as well as places for the specialized communities to work in smaller groups. As General McChrystal points out, “…many of the traits that made our teams so good also made it incredibly difficult to scale those traits across an organization… Building a single team the size of our Task Force would be impossible.”16 To solve this problem, the Linux kernel development community maintains smaller specialized code repositories and email distribution lists dedicated to various sub-elements of the kernel, such as graphics processing, network drivers, and security.
Make it Easy to Join

Writing for The Harvard Business Review, data scientist Alex “Sandy” Pentland examined the communication patterns of high performing teams, noting that: “Higher-performing teams seek more outside connections,” calling this objective measurement of a team’s outside connections “exploration,” finding that: “…scoring well on exploration is most important for creative teams, such as those responsible for innovation, which need fresh perspectives.”17 It falls to the designer of CIS to enable these teams to ensure that this exploration can occur by minimizing any barriers (financial cost, policy, or technical challenge are examples) to new nodes joining the network.
Describing his communication systems, General McChrystal says: “We knew that forging the neural network that would facilitate our emergent analysis of complex problems was vital for our long term success,”18 and so he ensured the Task Force took concrete steps to enable access. Occupy Sandy and the Cajun Navy achieved success by coordinating the efforts of volunteers, and the Linux kernel development community allows computer programmers all over the world to easily contribute their expertise, contributions that almost certainly would be less if contributing was inconvenient.
Duplicate Familiar Communications Patterns
On small scales, humans naturally tend to self-organize into resilient organizations, as evidenced by continued survival over the millennia. Therefore, designers of CIS to enable resilient organizations should seek to replicate natural means of communication as much as possible. Alex Pentland, in his research on communication patterns in teams, found that: “…the most valuable form of communication is face-to-face. The next most valuable is by phone or video conference, but with a caveat: Those technologies become less effective as more people participate in the call or conference. The least valuable forms of communication are email and texting.”19
CIS that enables, as much as possible, naturally resilient communications should seek to prioritize voice over text, and direct communication over indirect communication. General McChrystal’s O&I is an excellent example, the daily voice and video contact that Task Force members had with him allowed the passage of more than just operations and intelligence data. It offered him “…a stage on which to demonstrate the culture [he] sought.”20 Although Zello used by the Cajun Navy was not necessarily familiar in and of itself, the ‘walkie-talkie’ interface was familiar. A simple means of communication enabled the human brains to focus upon collaboratively solving problems, and not upon navigating unfamiliar CIS.
Interestingly, the Linux kernel development community almost completely eschews voice communications, relying instead upon email distribution lists. Most community members are experienced computer programmers, and so configure their email to show the email chains in an ‘online forum’ format. In this case, the distributed nature of the community and the technical comfort level allows a different means of communication, although one that is not unfamiliar to the members.
Caveats
Resilient CIS Requires Command Support
Not all CIS planning should or can place organizational resiliency above all other factors. Prioritizing support to resiliency over other factors when designing and maintaining CIS requires deliberate and conscious command support, as the trade-offs required to enable resiliency can be significant.
Resilient Networks Are Less Secure
The National Defence Security Orders and Directives (NDSODs)21 for Information Technology Security specify extremely strict requirements for the security of information. The standards of “least privilege” – everybody is given the absolute fewest rights necessary for their job and role – and “least functionality” – no CIS has more functionality than absolutely necessary for the designed task – are mandatory. These concepts are good for security and compartmentalization of information, but they severely restrict resiliency.
On a more granular level, the commonly applied ‘need to know’ test also restricts resiliency. With this test, every piece of shared information is examined to determine whether the intended recipient has a valid requirement for access. As the point of resiliency-enabling CIS is to better share information and context to build collaborative solutions, a more useful philosophy to enable agility is the ‘need to share’ idea. In this model, information is shared as widely as possible by default, and only restricted on a case-by-case basis when to do otherwise would be an unacceptable risk.
Resilient Networks Are Less ‘Capable’
Every community using a particular CIS will have different preferences and desires for functionality, performance, and user feel. While the desire for ‘agility’ can manifest itself in a desire to constantly add functionality or otherwise modify the CIS, it is important to remember that we are seeking agility to enable organizational resilience, not rapid change to suit individual tastes. CIS designers and managers should resist adding new features and tools – especially information management (IM) repositories – that could functionally be serviced by existing structures. No user should ever have to wonder where a needed piece of information is stored, or how to contact somebody else, even if this means sub-optimal methods are used. It is essential to maximize connectivity, not to optimize any one individual task.
In many cases, this will manifest itself as a lack of capability. If one sub-set of users prefers shared drive-like file structures, another sub-set prefers collaborative programs, such as SharePoint, and another wants a more webpage-like structure, it is better for the ‘cross-pollination’ of information essential for resilient organizations to consolidate information into one unified system, although most communities will perceive the system to be less capable than their ideal.
Resisting the urge to continuously modify and change CIS to suit individual tastes will require strong support from high levels of command, and CIS managers must remain ambassadors of the current system, ensuring that users have the skills and knowledge to use current systems to full benefit. Remember that one of the principles of designing resiliency-enabling CIS is reducing barriers to entry, and training is one of those barriers.
Planning Resilience
These principles of CIS-enabled resilience should form the basis of military CIS planning, but function more as guiding principles than practical planning guidance. In this section, I will make recommendations for IT professionals to plan CIS for resilient organizations.
What Is the CIS For?
The first question that needs to be answered when designing resilience-enabling CIS is, “What is the network designed to do?” The answer is not always obvious, but defining the purpose of networked CIS will allow definition of key factors. Generally speaking, it is designed to support some mix of coordinating operations and managing resources, and the degree to which each function is required will drive design considerations.
In a military context, CIS that coordinates operations should prioritize resiliency, enabling operational partners to join the network and share information. The ‘market square’ will often be an all-informed live chat, such as Mirc, and voice communications are considered essential. Availability is prized over most other security considerations. Designers should focus upon simplicity and common standards. The Cajun Navy use of Zello (voice) and Glympse (positional awareness) is an extreme example of CIS designed to coordinate operations.
In contrast, CIS designed for resource management should focus upon collectively maintaining accurate and auditable databases. Information integrity is prioritized over openness, to ensure confidence in the databases. Information is normally exchanged through more formal and structured means, such as standardized reports, asynchronous messaging (email), and libraries of documents. The Linux kernel development community is built around progressively developing and maintaining a stable code repository, and the primary means of communication are the online GitHub code database, and the internet forum-like distribution lists. Most successful CIS networks will fall somewhere in the middle of the two extremes: General McChrystal’s daily O&I to coordinate operations and integrate intelligence reports was enabled through extensive intelligence sharing databases and an enterprise-level email system.
Communicate Sideways
As mentioned earlier, General McChrystal describes the concept of networked individuals and organizations as a “Team of Teams.”22 In ‘teams’ as opposed to ‘commands,’ horizontal relationships between members grow organically and are as important as the vertical links inherent in the chain of command. He explains, “…we didn’t need every member of the Task Force to know everyone else; we just needed everyone to know someone on every team… We needed to enable a team operating in an interdependent environment to understand the butterfly-effect ramifications of their work and make them aware of the other teams with whom they would have to cooperate.” In the same way, any designer of resilience-enabling CIS must determine how users and nodes will communicate between each other.
Although determining what the ‘market square’ for any given community will be is the biggest design problem to solve, close attention must also be paid to how individual users and communities will communicate between each other. Again, easily-scalable means that closely mimic natural human communication is preferred. Open standards supported by a wide range of products are better than proprietary formats, worth the trade-off to lower functionality or higher cost.
Plan the Access
In the same way that any agile organization will change throughout its lifespan, resilience-enabling CIS must be prepared to enable that change. While planning CIS, the question, “hHw will additional nodes gain access to the system?” must be answered. Further, the cost of adding new users should be reduced as much as possible.
Depending upon the information security requirements, there are two ways to enable access. Using an ‘open’ philosophy, common standards can be used, allowing new users to best select the means to join the network. A Department of Homeland Security analysis found that Occupy Sandy “…used free open-source software platforms because they were familiar and accessible. The small learning curve and minimal training kept the network running efficiently, and made it easier for existing and potential volunteers to maintain situational awareness.”23 The ‘cost’ of joining the network is the time it takes to download the app and any internet package data fees. The Linux kernel development community is even more open; email and web pages do not require users to download any program other than a web browser, which is a standard feature on almost every device.
Another approach, already discussed as having been used by General McChrystal’s Task Force, is to assume the cost on behalf of potential new nodes. He describes how the Task Force “…designed prepackaged communication bundles that [the] teams could take into the field, wherever they were in the world… We invested in bandwidth to enable us to reach every component of our force and our partners… any member of the Task Force, and any of the partners we invited, could eventually dial into the O&I securely from their laptops and listen through their headphones.”24
In either case, the designer must plan how to add nodes and integrate them as functioning members of the community. Procedures and necessary authorities must be determined in advance and well known. Training for new members must be planned, either through ‘landing screens’ and frequently asked questions (FAQs), tutorials, or by using technologies and procedures already familiar to likely new users.
Conclusion
Organizational Agility, or Resilience, is not simply a function of the command environment or culture. In the modern distributed world, resilient organizations require communications and information systems that enable that resilience to develop. Communications and Information Systems must be specifically designed to enable resilient organizations, with the designer and community fully aware of the trade-offs that must be made to functionality, security, and cost. However, the benefits of creating shared consciousness, lowering the cost of participation, and emulating familiar human communication patterns are significant.
*About the author: Captain Joseph Long is a Signals Officer and Certified Information Systems Security Practitioner. He graduated from RMC in 2011 with a BSc in Computer Science.
Source: This article was published by the Canadian Military Journal, Volume 18, Number 2, Page 15.
Notes:
- Strong, Secure, Engaged. Canada’s Defence Policy, (Ottawa: Government of Canada, 2017).
- Michael A. Bell, The Five Principles of Organizational Resilience, (Gartner, 2002) at: <www.gartner.com/doc/351410/principles-organizational-resilience.>.
- General (Ret’d) Stanley McChrystal, Team of Teams, (New York: Penguin, 2015), p. 129.
- Strong, Secure, Engaged. Canada’s Defence Policy, “Anticipating emerging threats and challenges is fundamental to Canada’s security. The Defence team will improve its ability to provide timely information to decision-makers, allowing the Government to identify and understand emerging events and crises, respond appropriately, and minimize the destructive effects of prolonged conflict.”
- US Department of Commerce, Service Assessment: Hurricane/Post-Tropical Cyclone Sandy, October 22–29, 2012, at: <https://www.weather.gov/media/publications/assessments/Sandy13.pdf>.
- US Department of Homeland Security, The Resilient Social Network,
(USA: Homeland Security Studies and Analysis Institute, 2013): “Occupy
Sandy is a grassroots volunteer disaster relieve movement which provided
innovative support to Sandy recovery efforts. Within four months,
Occupy Sandy amassed 60 000 volunteers, collected nearly $1 million in
donations for Sandy Survivors, and distributed food, clothing, medical
supplies, and construction materials. Occupy Sandy impacted thousands of
survivors in New York and New Jersey. Some of Occupy Sandy’s notable
accomplishments included:
- Establishing food distribution centres in Brooklyn and other Hubs, such as Coney Island;
- Setting up online donation and volunteer social media sites;
- Serving nearly 10000 meals a day in the week after Sandy made landfall, through 15000 volunteers recruited via social media sites; and
- Coordinating motor pools to transport construction teams and medical committees to survivors in the field.”
- Emily Wax-Thibodeaux, “‘Cajun Navy’ races from Louisiana to Texas, using boats to pay it forward,” in Chicago Tribune, 28 August 2017, at: <http://www.chicagotribune.com/news/nationworld/ct-cajun-navy-hurricane-harvey-20170828-story.html>.
- McChrystal, p. 168.
- Joel Gunter, “International Space Station to boldly go with Linux over Windows,” in The Telegraph, 10 May 2013, at: <https://www.telegraph.co.uk/technology/news/10049444/International-Space-Station-to-boldly-go-with-Linux-over-Windows.html>. “We migrated key functions from Windows to Linux because we needed an operating system that was stable and reliable – one that would give us in-house control. So if we needed to patch, adjust, or adapt, we could.”
- Top 500 Project “Operating Systems,” accessed 10 January 2018, at: <www.top500.org/statistics/details/osfam/1>.
- Linux Foundation, Linux Kernel Development Report, 2016, accessed 12 January 2018, at: <www2.thelinuxfoundation.org/linux-kernel-development-report-2016>.
- <github.com/Torvalds/Linux>.
- <www.kernel.org/doc/html/v4.13/process/howto.html>.
- McChrystal, p. 164.
- Facebook.com/LaCajunNavy
- McChrystal, p. 132.
- Alex “Sandy” Pentland, “The new Science of Building Great Teams,” in The Harvard Business Review, April 2012.
- McChrystal, p. 164.
- Pentland.
- McChrystal, p. 227.
- Department of National Defence, National Defence Security Orders and Directives, 2015, Ch. 7.
- McChrystal, p. 128.
- US Department of Homeland Security.
- McChrystal, p. 164.