Intermediate Force Capabilities: Nonlethal Weapons And Related Military Capabilities – Analysis
By NDU Press
By Sara McGrath
The U.S. military has a history of fighting wars and winning battles through the overwhelming use of force. In today’s strategic environment, however, the battle is often one of competition below the threshold of armed conflict. Our adversaries are gaining the advantage by exploiting the predictable joint force responses, either showing force through military presence or employing lethal force. Both of these extremes are often ineffective against adversary competition. Yet neither doctrine nor training prepares the joint force to employ force between these extremes. To protect current and future national political and military interests, the U.S. military must modify its mindset and tactics to gain the necessary tools for strategic competition, or the Nation risks losing its competitive advantage.
In the current strategic environment, the application of lethal force is often not suitable against threats below the threshold of armed conflict. A more suitable option, intermediate force capabilities (IFCs), offers a proportional response through nonlethal and nondestructive means. Nonlethal weapons (NLWs) are a primary contributor to the application of intermediate force, but additional existing capabilities also support the concept. These capabilities—including information operations (IOs), electromagnetic warfare (EW), and cyber operations (COs)—together with NLWs, contribute to achieving political goals without the use of lethal force.1 These capabilities are essential to joint operations in today’s security environment, yet commanders hesitate to employ them. This hesitancy is due to a poor understanding of their applicability for threats below armed conflict and, furthermore, because of minimal doctrinal integration and a lack of training on their potential benefits. One way to enable the joint force to gain a better conceptual understanding of how to employ IOs, EW, COs, and NLWs is to integrate them doctrinally as IFCs and to promote them as suitable alternative solutions to lethal force in current and future strategic environments. To explore the applicability of intermediate force and its contributing capabilities to the security environment, the following analysis shows the potential contributions of NLWs, IOs, EW, and COs to the IFC concept and offers suggestions to improve their integration in joint operations.
Traditionally, the United States has viewed national security through distinct categories of peace or war. In the traditional construct, showing military presence is an acceptable method to preserve peace through deterrence without the use of physical force. Conversely, once adversaries cross the threshold of armed conflict, the military responds to the threat with lethal force, both appropriate and proportional in a wartime scenario. But against the current challenge of “long-term strategic competition” and adversary aggression below the threshold of armed conflict, the line between war and peace blurs.2 In this gray zone, the proper determination on the use of force is rarely easily made in the face of an adversary’s coercion or aggression.3 Lethal force is often too aggressive in the gray zone, leaving the joint force without a suitable, proportional response to adversary competition and aggression. As a result, our adversaries can easily gain a strategic advantage by acting below the threshold at which the joint force would normally respond to traditional warfare.4 As an option to compete against the adversary, IFCs provide a flexible response that negates the adversary’s advantage of operating below the threshold of armed conflict.
IFCs are suitable for use across the entire competition continuum. By employing capabilities between “presence and lethal force to enable combat arms and support warfighters with expanded and enhanced options to deter, suppress, and/or respond to adversary action,”5 IFCs offer alternatives below the threshold of armed conflict: a nonlethal response option to adversaries’ coercive tactics, misinformation, and sabotage.6 They also enable U.S. forces to ameliorate allied concerns and collaborate with affected partner nations against strategic competition. However, for IFCs to be effective, the joint force must shift its mindset from the sole employment of lethal force to “the mindset and capabilities necessary to succeed” in the competition continuum.7 This perspective shift will support adopting and employing an array of IFCs and doctrinally integrating the IFC concept into joint operations.
Conditions Achieved by IFCs
To compare the capabilities of NLWs, IOs, EW, and COs and to show their contributions to IFCs, there must first be an understanding of what intermediate force provides to the warfighter. In traditional warfare, using or threatening lethal force is a way to achieve strategic outcomes. In contrast, during gray zone operations, adversaries intentionally avoid lethal force, so as to achieve long-term strategic objectives. The intent of these unconventional methods of coercion is to exhaust opponents, breaking political power or will, without a direct military confrontation.8 The joint force must counter strategic competitors’ actions by managing escalation and fostering peaceful competition while also deterring the threat.9 Current doctrine and training do not sufficiently prepare the joint force to employ methods to counter this sort of competition without force escalation. With a better understanding of their employment, IFCs allow the joint force to achieve deterrence and de-escalation without unnecessary lethal force.
IFCs give warfighters the option to exert influence flexibly, when necessary, and to escalate or de-escalate as appropriate.10 IFCs’ effects may include reducing collateral damage; deterring, defeating, or denying enemy access; and increasing decisionmaking space for the discriminate use of force.11 IFCs provide a toolbox of both nonlethal and nondestructive means to achieve political objectives for competition below the threshold of armed conflict. Additionally, IFCs improve force protection, help maintain legitimacy and credibility, and assert friendly force influence. Still, for their effective employment, the joint force must have the knowledge and means to use all the options of IFCs.
Evaluating Components of IFCs
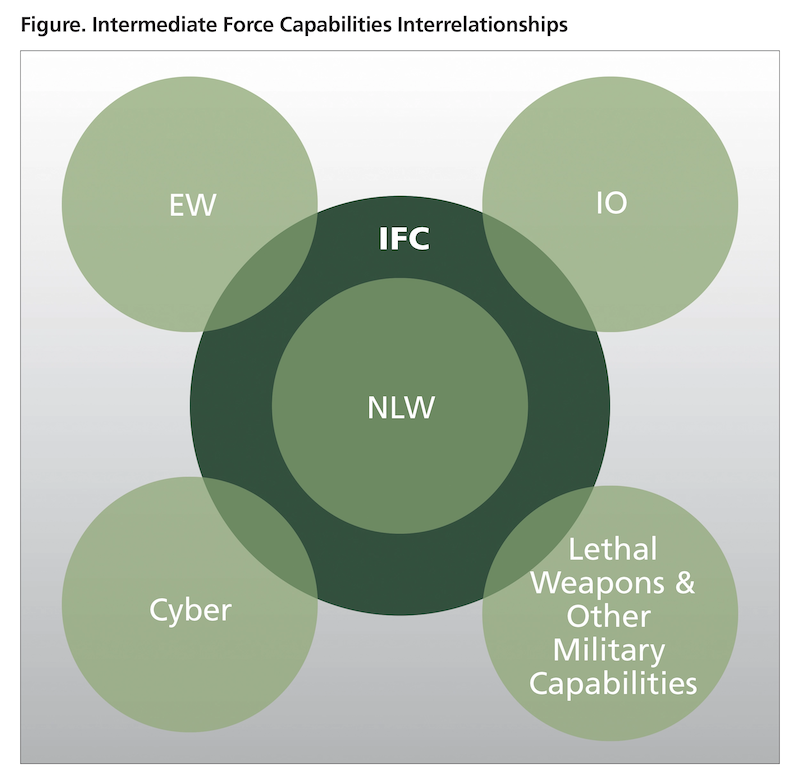
IFCs include an array of military capabilities. Exploring the component activities of NLWs, IOs, EW, and COs enables a comparison of each of these activities to the intended effects of IFCs. A summary of these effects includes four primary advantages: reducing unnecessary damage to personnel and/or infrastructure, increasing the time and distance for effective decisionmaking for maneuver or engagement, deterring or defeating adversary behavior, and preserving credibility and legitimacy for the United States and its partners and allies. NLWs provide all these advantages, but the method of employing IOs, EWs, and cyber and the type of effects they generate determine their ability to support intermediate-force capabilities. Although critical during armed conflict, destructive employment or effects are often not appropriate for intermediate-force application scenarios. For example, physically destroying adversary command and control systems is a method of IOs, antiradiation missiles are a method of EW, and cyber activities can “rise to the level of use of force, with physical damage or destruction.”12 These methods of employment create effects that go beyond the IFC level to lethal force. However, broadcasting messages is a form of IOs that is essential to IFCs; it allows friendly forces to influence the narrative and maintain the initiative in an otherwise ambiguous situation. Similarly, employing EW to deny an adversary’s ability to access command and control through the electromagnetic spectrum is critical to the success of the friendly mission. Finally, employing COs to protect and maintain control of network capabilities reduces unnecessary casualties by enabling situational awareness of friendly forces. The figure shows the interrelationship of NLWs, IOs, EW, and COs as IFCs.13 Each of these capabilities contributes to a set of activities that support optimal IFC employment.
Nonlethal Weapons
NLWs are weapons, devices, or munitions explicitly designed and primarily employed to incapacitate personnel or materiel immediately while minimizing fatalities, permanent injury to personnel, and unnecessary damage to property.14 Despite the known operational benefits of NLWs, their employment has predominantly been by military police or law enforcement. Understanding additional employment options of NLWs against an asymmetric threat allows the joint force to recognize their full value. Specific applications include using long-range nonlethal directed-energy weapons to deter malign activity of adversaries that are using proxies to harass U.S. land or maritime forces. Other examples include various crowd control devices, including multiple projectile munitions and grenades, laser ocular interrupters, auditory hailing devices, and vehicle-stopping devices.15 Additional improvements in technology—providing increased range, precision, and reliability—show promise for developments outside of these commonly known applications.16 Joint doctrine classifies NLWs as “additional capabilities” for nonlethal effects and recommends their integration to minimize both loss of life and property damage that could negatively influence public perception.17 This description of and recommendation for NLWs downplay and underemphasize the strategic role they have for maintaining favorable public perception and avoiding force escalation. The North Atlantic Treaty Organization (NATO) recognizes NLWs as a critical additional capability for meeting the demands of future operations and is currently advancing efforts for integrating IFCs into Alliance doctrine and planning.18 The joint force should follow NATO’s example and make a concerted effort to integrate NLWs and the IFC concept for successful operations below the threshold of armed conflict.
As a component of the IFC concept, NLWs offer a suitable approach when lethal force is unwarranted or undesirable, enhancing the commander’s ability to deter, deny, stop, disable, or de-escalate.19 Against a gray zone threat, NLWs reduce unnecessary damage through the discriminate use of force. Additionally, they increase decision space by offering an initial nonescalatory response for aiding in the determination of intent. Moreover, NLWs deteradversary behavior by providing a warning that adversary aggression is not acceptable. Finally, they preserve credibility and legitimacy by ensuring a level of force proportional to the situation. It is essential to understand that nonlethal fires do not eliminate the ability, nor the need, to use lethal force but instead provide strategic risk mitigation by creating the conditions to determine the necessary level of force.20 In an organization trained for the exceptional employment of lethal force, commanders must also recognize the value of NLWs as IFCs for a proportional military response below the level of armed conflict.
Information Operations
In traditional warfare, IOs are fundamental for facilitating physical maneuver during armed conflict. IOs also enable maneuver at all stages of crisis and below the level of armed conflict to increase the commander’s options.21 Defined as the integrated employment of information-related capabilities to influence, disrupt, corrupt, or usurp the decisionmaking of adversaries, IOs are essential to all military operations.22 NATO expands on this definition with the recognition that successful management of information influences all other elements of national power and is essential to “maintaining Allied freedom of action.”23 Common methods of managing information within the operational environment include military information support operations, military deception, operational security, public affairs, and civil-military operations, among others.24 Including an IO component of IFCs into an operational plan enables successful maneuver in both the physical and information spaces against the adversary threat.
IOs are a critical component of IFCs for friendly forces to advantageously influence and respond to ambiguous or threatening messaging. Enemy propaganda or coercion may prohibit friendly freedom of action in gray zone operations if not countered by friendly information. For example, an adversary may try to limit friendly use of novel technologies, such as directed energy, by using fear tactics to turn public opinion against the employment of this NLW. Additionally, the proliferation of technology makes it easier for an adversary to access and manipulate information against friendly forces.25 Strategic messaging by friendly forces attempts to counter these tactics. Just as NLWs can have a positive influence on public perception through limiting collateral damage, IOs can also have a positive influence if employed effectively.26 Just as gaining the initiative in the physical domain is essential, it is essential that friendly forces control the effects of information to gain and maintain the initiative in the information environment—and thus maintain favorable public perception. Today, commanders must be able to optimize the positive effects of IO during strategic competition to gain the advantage for friendly forces.
IOs are an essential capability against competition below the threshold of armed conflict because of the conditions they achieve using intermediate force levels. Due to the “numerous social, cultural, cognitive, technical, and physical attributes that act upon and impact knowledge, understanding, beliefs, world views, and, ultimately, actions of an individual, group, system, community, or organization,” the information environment is significant for shaping conditions in the gray zone.27 IOs provide an immediate warning for deterring adversary behavior. Additionally, IOs establish the conditions for friendly forces to gain global credibility or to publicly disapprove of adversaries’ illegal or coercive behavior, therefore maintaining their own legitimacy. Other examples of IO components of IFCs include preemptive strategic messaging to reduce collateral damage by facilitating maneuver away from a targeted area. In addition, employing messaging through novel technologies such as long-range auditory warning devices can increase a commander’s decisionmaking space and time to determine adversary intent.28 Just as the joint force employs IOs to support combat operations, it must adapt to a mindset of employing IOs as a component of intermediate force to control the information environment for friendly forces operating in the gray zone.
Electromagnetic Warfare
EW is an additional capability that contributes to IFCs by ensuring friendly use of the electromagnetic spectrum (EMS) in a confrontation below the level of armed conflict. During any engagement today, including those that fall below the threshold of armed conflict, friendly forces must have control of the EMS for effective operations.29 Joint EMS operations facilitate the mission areas of EW and other activities that rely on the EMS, including certain activities that overlap between IO, cyber, and NLWs.30 EW includes any activity in the EMS using radio waves, microwaves, millimeter waves, infrared radiation, visible light, ultraviolet radiation, X-rays, and gamma rays.31 Divided into the subcomponents of electromagnetic attack, electromagnetic support, and electromagnetic protection, EW is defined in doctrine as military actions involving the use of electromagnetic and directed energy to control the EMS or to attack the enemy.32 In a similar definition, NATO also emphasizes that EW operations enhance situational awareness and protect friendly forces.33 During gray zone operations, just as during traditional warfare, commanders may take for granted their ability to maneuver in the EMS. In the competition continuum, where control of the EMS is essential, intermediate force must include EW to facilitate physical maneuver and increase time and decision space for friendly forces.
Maneuver within the EMS is a critical capability for activities below the level of armed conflict. However, EW employment is often suboptimal in joint operations because of fear and a misunderstanding of its effects. Compounding the fear and misunderstanding, innovation and investment in EW capabilities have waned during years of counterinsurgency.34 Together, the minimal investment in modernizing EW and the fear of EW effects have caused their underuse within the joint force, with many commanders lacking knowledge and proficiency in EMS operations. Many simply assume that they will have full use of the EMS when needed. This situation must change so the joint force can become proficient at employing EW IFCs when appropriate. The joint force must understand the essential relationship of EW IFCs to the maneuver of friendly forces and recognize the critical role of the EMS against adversaries so that leaders have the knowledge and proficiency needed to operate in the EMS.
Employing EW as a component of IFCs creates opportunities across the competition continuum. EW that denies, degrades, or delays adversary systems provides viable intermediate force. However, EW tactics that include kinetic fires for the destruction of enemy systems, while potentially effective, are not appropriate for the level of force below armed conflict. More appropriate EW tactics, such as jamming adversary systems, reduce unnecessary casualties by denying enemy observation or targeting systems. EW employed for disruption against adversary weapons systems deters enemy capabilities used to harass, intrude, or assess friendly forces. Degradation of adversary communications or warning systems contributes to increasing the decisionmaking space for friendly force maneuver. Additionally, EW preserves EMS access to the information space for friendly use or denies access to the adversary. Finally, EW creates intermediate force through nonkinetic, nonlethal fires with reversible and nondestructive effects.35 Each of these applications illustrates the critical interdependence of EW components of IFCs as an option against adversary gray zone activities. The joint force must capitalize on these capabilities to operate effectively against the adversary in the EMS in the strategic environment.
Cyber Operations
COs, the final capability considered here, make several contributions to intermediate force with specific applications to the gray zone. Most COs create fires with little or no associated destruction through the interdependent network of information technology infrastructures and data.36 Additionally, cyber targets include numerous critical aspects of the operational environment, such as the Internet, telecommunications networks, and computer systems.37 In the operational environment, commanders conduct COs to retain freedom of maneuver in cyberspace, accomplish the JFC’s objectives, deny freedom of action to enemies and adversaries, and enable other operational activities.38 Similarly, NATO doctrinally recognizes COs for their essential contributions to “collective defence.”39 Each of these advantages of COs can contribute to IFCs, yet to use them effectively commanders must understand the types of cyber employment and the effects that best fulfill the intent of intermediate force.
Compared with traditional kinetic operations, COs have limited historical use in conflict. Given the scant operational case studies in this relatively new domain, their cyber effects and secondary effects are not entirely clear.40 Although destruction of enemy networks is a potentially effective use of COs, this goal is not applicable to the concept of intermediate force. Additionally, studies suggest that certain applications of cyber may cause unintentional force escalation; these methods, too, do not meet the intent of intermediate force.41 The methods of COs best suited for IFCs include defensive operations to preserve friendly networks and offensive ones to degrade or deny adversary networks with nondestructive effects that reduce network capabilities. Cyber capabilities known for nondestructive effects will enable the joint force to gather information or employ targeted actions without lethality and are applicable across the competition continuum.42 In a situation where the strategic and operational goals are to minimize the use of lethal force and the resulting destruction, COs employed at intermediate force levels are most desirable. Employing COs’ nondestructive fires as a component of IFCs enhances joint operations against adversary competition—but only if commanders recognize their suitability and feasibility in the gray zone.
COs support the combined employment of multiple IFCs and contribute to achieving strategic objectives during gray zone operations. In such situations, cyber fires are similar to NLWs in reducing collateral damage and deterring the adversary without lethal or destructive force.43 Offensively conditioning the operational environment with COs enhances the effectiveness of other IFCs. Defensively, employing COs to protect friendly networks creates space for friendly forces to maneuver, increasing time and space for friendly operations in the physical domain. Educating and enabling the joint force to employ cyber fires in the gray zone is essential for countering strategic competition without escalating the level of force.
Scenario Analysis
The following is a theoretical example of IFCs’ use in an operational environment. This scenario describes current capabilities of the joint force in a plausible operating environment to highlight the integrated employment of NLWs, IOs, EW, and COs. A commander must be knowledgeable about the options available within the IFC concept to achieve optimal conditions and delay force escalation.
U.S. and partner-nation naval forces are conducting freedom of navigation (FON) operations in an operational area bordered by multiple states with competing maritime claims. During these operations, friendly forces encounter a mixed contingent of adversary vessels including civilian, maritime militia, and fast-attack craft. The adversaries attempt to interfere with friendly flight operations and disrupt communications systems. The strategic objectives are to de-escalate tensions while conducting deterrence. The specified and implied tasks are to reduce harassing maritime activities, maintain credibility and legitimacy in the operational area, and enable partner and allied nations to defend themselves without escalating to lethal force while preserving FON.
During operations, multiple unmanned aerial systems (UASs) approach a U.S. warship and interfere with friendly operations. To counter the UASs, friendly forces employ IFCs against them that include electronic attack to deny their observation capabilities, resulting in their departing the area. Using IOs as the second component of IFCs, friendly forces video and transmit the UAS swarm, broadcasting the harassing behavior to national news sources to influence public opinion against adversary tactics.
Despite the failed UAS intrusion, the fast-attack craft approaches U.S. ships at a high rate of speed. IFCs provide warning through NLWs by means of directed-energy vessel stopping and acoustic warning devices, delaying the approach of the vessels long enough for the friendly forces to determine adversary intent.44 Additionally, the use of ongoing cyber-component IFCs during these operations protects friendly command and control networks against adversary cyber intrusion, allowing freedom of maneuver in cyberspace for the friendly and allied nations.
The decision to use IFCs in this scenario is in line with the strategic goal—in this case, to de-escalate the threat. The use of IFCs enables multiple proportional and suitable response options. IFCs preserve the credibility and legitimacy of friendly forces and reduce potential collateral damage. Furthermore, they open the decision space and allow time for commanders to determine if lethal force is suitable for the situation. If it is needed, there is nothing to prevent or prohibit the use of lethal force; however, using lethal force before it is warranted can damage the credibility of friendly forces. IFCs give the commander additional options to respond to a threat and de-escalate it.
An alternative playing-out of this scenario without the use of IFCs shows several points at which friendly force actions might result in force escalation. The first is at the onset of the UAS intrusion. The second is at the approach of the fast-attack craft. It is possible that friendly forces could respond by firing warning shots toward the approaching adversary. These shots could be misinterpreted and met with force in response. The escalation continues until one side or the other crosses the threshold of lethal force. Ultimately, it is likely that the global perception of this incident would focus on the fact that friendly forces fired first. Unfortunately, firing a warning shot is a common response by a force not conditioned to think of alternate capabilities and by our partner nations faced with similar scenarios.
In the first example, by integrating the components of IFCs, including concurrent cyber protection to ensure situational awareness, EW to deter the UAS swarm, and NLWs to de-escalate the threat of the fast-attack craft, the joint force achieves the specified and implied tasks. Additionally, IOs in support of the strategic objectives help preserve credibility of friendly forces and maintain FON in the operating area. But because current doctrine leads the joint force to overlook the integration of NLWs, IOs, EW, and COs against an asymmetric threat, the alternate outcome of force levels escalating to lethal levels is a real possibility. To avoid escalating force levels, IFCs must be accessible across the joint force by commanders who understand each of the component capabilities and the applicability of IFCs when lethal force is not desirable.
Risks and Challenges
The above scenario illustrates the benefits of integrating IFCs into joint operations. However, as with any capability, there are associated risks. These include force management risk and future challenges risk.45 The first risk stems from a hesitation to invest in nonlethal technologies and take on the associated challenge of training the joint force in those technologies. Conversely, if the United States does not equip its forces with new technologies and train them in those technologies’ use, there is a risk that adversaries will quickly outpace the United States in equipment, capabilities, and tactics. The second risk is due to the fundamental military perception on the use of lethal force. The perceived characteristic of any military force is that it is a lethal organization with no business in nonlethal capabilities.46 One way to change this narrow mindset is to consider the perspective that war is a continuation of politics by other means.47 The military must support political objectives in the gray zone, and, to do so effectively, the joint force must have suitable options below lethal force.
This same traditional military perception contributes to the idea that investment in nonlethal technologies takes away from investment in lethal ones. This perceived tradeoff comes with the risk that when a threat arises, the commander must choose between escalating the level of force or simply not responding to the threat. Neither of these options is ideal against an adversary that is skilled at warfare below the level of armed conflict. Lethal capabilities alone are not sufficient to equip the joint force for success. The fundamental perceptions that the military is equipped only for peace or war must change, so that the joint force can respond proficiently to adversary aggression with multiple capabilities, including IFCs, across the competition continuum.
Opportunities
The challenge of implementing IFCs also provides opportunities for the joint force. The Department of Defense has an opportunity to change how it views the poles of war and peace. Our adversaries excel in operations between the extremes. If the U.S. military cannot also operate between extremes, it will lose its competitive edge. We must become proficient in operating outside of these well-known and ingrained black-and-white confines, and doing so requires adopting new capabilities suited for the gray zone. Our current operating environment presents the joint force with the opportunity to expand available response options by investing in new technologies. Adopting new concepts and technologies will support the evolution of the institutional mindset and improve operations against current and emerging threats. The evolving mindset will support the simultaneous changes needed in education and training for all leaders on IFCs and the concepts and technologies that support them in the strategic environment.48 Realizing these opportunities will allow the United States to gain and maintain the advantage.
Doctrinal Integration
Capitalizing on the opportunity to integrate IFCs into the joint force requires assimilating the concept through doctrine, organization, training, materiel, leadership and education, personnel, and facilities. This process has begun with the renaming, in March 2020, of the Joint Non-Lethal Weapons Directorate to the Joint Intermediate Force Capabilities Office to emphasize the importance of intermediate force to the current threat environment.49 Additionally, in the tri-Service doctrine Advantage at Sea, published in 2020, Service leadership recognizes and recommends IFCs as an applicable concept.50 Materiel investment continues for new IFC technologies that will provide additional means of influence. However, the momentum of these changes must continue; IFCs must be represented doctrinally more consistently as valid and plausible targeting options for commanders.
One recommendation for doctrinal integration is to introduce the concept of “Intermediate Force” as the first heading under “Joint Fire Support and Force Capabilities” in Joint Publication 3-09, Joint Fire Support. Doctrinally identifying NLWs, IOs, EW, and COs emphasizes their contribution to intermediate force. The current doctrinal references are insufficient to highlight their contributions to combat operations and understate their importance for operations below the threshold of armed conflict. To improve the integration of NLWs, IOs, EW, and COs, doctrine should emphasize their contribution to IFCs. An explanatory paragraph describing intermediate force should define IFCs as “all domain,” suitable across the competition continuum and for employment by multiple platforms across the force. Emphasis should include the relevance of each of the capabilities against a gray zone threat, with an additional reference to the individual joint publication governing their standard employment. In offering intermediate force as an option in addition to lethal force but not in place of lethal force, the IFC concept becomes a suitable, applicable, trained response for future leaders.
Adversaries’ actions across the competition continuum require the joint force to compete through options other than lethal force. Yet strongly held perceptions on the distinction between peace and war have left the U.S. military neither positioned nor prepared for competition below the level of armed conflict. To remain relevant, leaders must “evolve our approach to warfighting,” meaning that we must broaden our perspectives and adopt new technologies and concepts that support such evolution.51 IFCs offer essential options to the joint force to deter and de-escalate adversary behavior when lethal force is not suitable. The U.S. military cannot continue to overlook these critical capabilities as tools of influence against the adversary, when the strategic goals are to de-escalate tension and avoid increasing the level of force. Without the option of intermediate force, U.S. national security goals are at risk. To mitigate this risk, the military establishment must continue to proliferate information and enhance the ability of the joint force to understand how intermediate force can gain the advantage for friendly forces in the strategic environment.
About the author: Colonel Sara McGrath, USMC, is an Analyst in the Joint Intermediate Force Capabilities Office, Quantico, Virginia.
Source: This article was published in Joint Force Quarterly 109, which is published by the National Defense University.
Notes
1 John L. Barry, Michael W. Everett, and Allen G. Peck, Nonlethal Military Means: New Leverage for a New Era (Cambridge, MA: John F. Kennedy School of Government, 1994), 2, available at <https://iiif.lib.harvard.edu/manifests/view/drs:469582318$4i>.
2 Summary of the 2018 National Defense Strategy of the United States of America: Sharpening the American Military’s Competitive Edge (Washington, DC: Department of Defense [DOD], January 2018), 2, available at <https://dod.defense.gov/Portals/1/Documents/pubs/2018-National-Defense-Strategy-Summary.pdf>.
3 Frank G. Hoffman, The Contemporary Spectrum of Conflict: Protracted, Gray Zone, Ambiguous, and Hybrid Modes of War (Washington, DC: The Heritage Foundation, October 15, 2016), 26, available at <https://www.heritage.org/military-strength-topical-essays/2016-essays/the-contemporary-spectrum-conflict-protracted-gray>.
4 Summary of the Irregular Warfare Annex to the National Defense Strategy (Washington, DC: DOD, 2020), 2, available at <https://media.defense.gov/2020/Oct/02/2002510472/-1/-1/0/Irregular-Warfare-Annex-to-the-National-Defense-Strategy-Summary.PDF>.
5 Advantage at Sea: Prevailing With Integrated All-Domain Naval Power (Washington, DC: Headquarters Department of the Navy, December 2020), 25, available at <https://media.defense.gov/2020/dec/16/2002553074/-1/-1/0/triservicestrategy.pdf>.
6 Intermediate Force Capabilities: Bridging the Gap Between Presence and Lethality, Executive Agent’s Planning Guidance 2020 (Quantico, VA: Department of Defense Non-Lethal Weapons Program, March 2020), available at <https://mca-marines.org/wp-content/uploads/DoD-NLW-EA-Planning-Guidance-March-2020.pdf>.
7 Summary of the Irregular Warfare Annex to the National Defense Strategy, 1.
8 Ibid., 4.
9 Joint Doctrine Note 1-19, Competition Continuum (Washington, DC: The Joint Staff, June 3, 2019), 5, available at <https://www.jcs.mil/Portals/36/Documents/Doctrine/jdn_jg/jdn1_19.pdf>.
10 Wendell B. Leimbach, Jr., and Susan D. LeVine, “Winning the Gray Zone: The Importance of Intermediate Force Capabilities in Implementing the National Defense Strategy,” Comparative Strategy 40, no. 3 (2021), 223–234.
11 “Analytical Support to the Development and Experimentation of NLW Concepts of Operation and Employment,” STO-TR-SAS-94, North Atlantic Treaty Organization (NATO) Science and Technology Organization, May 4, 2017.
12 Allied Joint Publication (AJP)-3.10, Allied Joint Doctrine for Information Operations (Brussels: NATO, November 2009), I-10, available at <https://info.publicintelligence.net/NATO-IO.pdf>; Joint Publication (JP) 3-12, Cyberspace Operations (Washington, DC: The Joint Staff, June 8, 2018), II-4, available at <https://www.jcs.mil/Portals/36/Documents/Doctrine/pubs/jp3_12.pdf>.
13 Joint Professional Education Intermediate Force Capabilities Courseware Brief, Joint Intermediate Force Capabilities Office, Quantico, VA.
14 JP 3-09, Joint Fire Support (Washington, DC: The Joint Staff, April 10, 2019), GL-8, available at <https://www.jcs.mil/Portals/36/Documents/Doctrine/pubs/jp3_09.pdf>.
15 Multi-Service Tactics, Techniques, and Procedures for the Employment of Nonlethal Weapons (Hampton, VA: Air Land Sea Application Center, May 2020), 7–11.
16 Leimbach and LeVine, “Winning the Gray Zone,” 3–4.
17 JP 3-09, III-13; JP 3-0, Joint Operations (Washington, DC: The Joint Staff, January 17, 2017, Incorporating Change 1, October 22, 2018), III-37, available at <https://irp.fas.org/doddir/dod/jp3_0.pdf>.
18 Research Task Group SAS-151, “Solutions Enabling Intermediate Force/Non-Lethal Weapon Contributions to Mission Success,” video, 2:37, March 30, 2022, available at <>.
19 Multi-Service Tactics, Techniques, and Procedures for the Employment of Nonlethal Weapons, 2.
20 Wendell B. Leimbach, Jr., “DOD Intermediate Force Capabilities: Bringing the Fight to the Gray Zone,” Joint Intermediate Force Capabilities Office, available at <https://jnlwp.defense.gov/Portals/50/Documents/Resources/Presentations/IFCOverviewBrief_ColL_short>.
21 AJP-3.10, I-2.
22 JP 3-13, Information Operations (Washington, DC: The Joint Staff, November 27, 2012, Incorporating Change 1, November 20, 2014), GL-3, available at <https://irp.fas.org/doddir/dod/jp3_13.pdf>.
23 AJP-3.10, I-10; JP 3-12.
24 JP 3-13, II-6.
25 AJP-3.10, 1-3.
26 JP 3-0, xiii.
27 Ibid., IV-1–IV-2.
28 Susan LeVine, “Beyond Bean Bags and Rubber Bullets: Intermediate Force Capabilities Across the Competition Continuum,” Joint Force Quarterly 100 (1st Quarter 2021), available at <https://ndupress.ndu.edu/Media/News/News-Article-View/Article/2497112/beyond-bean-bags-and-rubber-bullets-intermediate-force-capabilities-across-the/>.
29 JP 3-85, Joint Electromagnetic Spectrum Operations (Washington, DC: The Joint Staff, May 22, 2020), I-1, available at <https://www.jcs.mil/Portals/36/Documents/Doctrine/pubs/jp3_85.pdf>.
30 Ibid., I-13.
31 Ibid., I-2.
32 Ibid., I-5.
33 “NATO MC 64/11 Electronic Warfare Policy,” July 2018, quoted in Malte von Spreckelsen, “Electronic Warfare—The Forgotten Discipline,” The Journal of the Joint Air Power Confidence Centre 27 (Autumn/Winter 2018), available at <https://www.japcc.org/articles/electronic-warfare-the-forgotten-discipline/>.
34 Ibid., 2.
35 JP 3-85, B-1.
36 JP 3-12, I-1, II-11.
37 Ibid., I-1.
38 Ibid., ix.
39 The Warsaw Declaration on Transatlantic Security, NATO, July 9, 2016, available at <https://www.nato.int/cps/en/natohq/official_texts_133168.htm>.
40 Martin C. Libicki and Olesya Tkacheva, “Cyberspace Escalation: Ladders or Lattices?” in Cyber Threats and NATO 2030: Horizon Scanning and Analysis, ed. A. Ertan et al. (Tallinn, Estonia: NATO Cooperative Cyber Defense Centre of Excellence, 2020), 70, available at <https://ccdcoe.org/uploads/2020/12/Cyber-Threats-and-NATO-2030_Horizon-Scanning-and-Analysis.pdf>.
41 George Perkovich and Ariel E. Levite, ed., Understanding Cyber Conflict: Fourteen Analogies (Washington, DC: Georgetown University Press, 2017), 3.
42 Ibid.
43 Robert E Schmidle, Jr., Michael Sulmeyer, and Ben Buchanan, “Nonlethal Weapons and Cyber Capabilities,” in Perkovich and Levite, Understanding Cyber Conflict, 31.
44 David B. Law, “Directed Energy (DE) Intermediate Force Capabilities (IFCs): Relevant Across the Range of Military Operations,” PowerPoint presentation, Joint Intermediate Force Capabilities Office, Quantico, VA, January 27, 2021, available at <https://jnlwp.defense.gov/Portals/50/Documents/Resources/Presentations/DSIAC-Webinar-DE-Intermediate-Force-Capabilities.pdf?ver=nIDCf75TAytk16Je3N5hkg%3d%3d>.
45 Quadrennial Defense Review Report (Washington, DC: DOD, February 2010), 90, available at <https://dod.defense.gov/Portals/1/features/defenseReviews/QDR/QDR_as_of_29JAN10_1600.pdf>.
46 Yasmin Tadjdeh, “Directorate Wants to Change View of Nonlethal Weapons,” National Defense, July 31, 2019, available at <https://www.nationaldefensemagazine.org/articles/2019/7/31/directorate-wants-to-change-view-of-nonlethal-weapons>.
47 Carl von Clausewitz, On War, ed. and trans. Michael Howard and Peter Paret (Princeton: Princeton University Press, 1976), 87.
48 Future of Defense Task Force Report 2020 (Washington, DC: House Armed Services Committee, September 23, 2020), 20.
49 Intermediate Force Capabilities, 1.
50 Advantage at Sea, 18.
51 David H. Berger, “A Message from the Commandant of the Marine Corps,” March 6, 2022, available at <https://mca-marines.org/wp-content/uploads/FMFM1-Warfighting_Anniversary-Letter-from-CMC.pdf>.