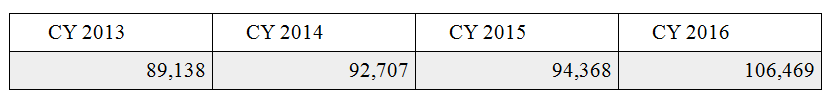The Clock Is Ticking: Why Congress Needs To Renew America’s Most Important Intelligence Collection Program (Part II) – Analysis
By Published by the Foreign Policy Research Institute
By George W. Croner*
The Statutory Process of Section 702 Collection
(FPRI) — The statutory scope of Section 702 can be synopsized as follows: Section 702 of FISA permits the Attorney General and the Director of National Intelligence to jointly authorize the (1) targeting of persons who are not United States persons, (2) who are reasonably believed to be located outside the United States, (3) with the compelled assistance of an electronic communication service provider, (4) in order to acquire foreign intelligence information.
Section 702 opens by providing the Attorney General and the Director of National Intelligence (“DNI”) with the authority to jointly authorize, for a period of up to one year, “the targeting of persons reasonably believed to be located outside the United States to acquire foreign intelligence.”[1] This authorization is immediately followed by a series of “Limitations”: i.e., (1) that no person known at the time of the acquisition to be located within the United States may be intentionally targeted; (2) that no person reasonably believed to be located outside the United States may be targeted if the purpose is to acquire the communications of a particular, known person reasonably believed to be in the United States; (3) that no United States person reasonably believed to be located outside the United States may be intentionally targeted; (4) that no communication may be intentionally acquired where, at the time of the acquisition, the sender and all intended recipients are known to be located in the United States; and (5) that all acquisitions under Section 702 must be conducted in a manner consistent with the Fourth Amendment to the Constitution of the United States.[2]
To ensure compliance with these statutory restrictions, Section 702 requires that the Attorney General, in consultation with the DNI, adopt “targeting procedures” (50 U.S.C. § 1881a(d)),[3] “minimization procedures” (50 U.S.C. §1881a(e)), and “guidelines” (50 U.S.C. § 1881a(f)). The “targeting procedures” and “guidelines” are designed to ensure compliance with the above-described “Limitations” found in 50 U.S.C. § 1881a(b). The minimization procedures, like those required in connection with traditional FISA surveillance, are intended to minimize the acquisition, retention, use, and dissemination of nonpublicly available information concerning unconsenting U.S. persons consistent with the needs of the United States to obtain, produce, and disseminate foreign intelligence information.
Authority for a Section 702 acquisition is obtained in a manner materially different from a traditional FISA surveillance. FISA requires an application to the FISC for an order which can be issued only after an individualized determination that there is probable cause that the target is a foreign power or an agent of a foreign power, and that the target is using or about to use specified facilities. Conversely, a Section 702 acquisition is initiated by a written “certification” of the Attorney General and the DNI attesting that there are procedures (i.e., targeting procedures) that have been submitted to the FISC (or will be submitted with the certification) and guidelines (which are not submitted to the FISC) that are reasonably designed to: (1) ensure that the proposed acquisition is limited to targeting persons reasonably believed to be outside the United States; and (2) prevent the intentional acquisition of any communication as to which the sender and all intended recipients are known at the time of the acquisition to be located in the United States. The certification must also include an attestation that the acquisition will be conducted in accordance with minimization procedures that meet the standards of FISA, and that “a significant purpose” of the acquisition is to obtain foreign intelligence information.[4] However, in a clear departure from the requirements of a traditional FISA surveillance, a certification is not required to identify any particularized target or to disclose the specific facilities, places, premises, or property at which an acquisition will be directed or conducted. 50 U.S.C. § 1881a(g)(4).
Upon receipt of a certification (and, where appropriate, its accompanying targeting and minimization procedures), the FISC has 30 days to conduct a review. The 30-day period may be, and often has been, extended for good cause. The review contemplated by Section 702 is materially different than that performed in connection with a traditional FISA application. Under Section 702, the FISC conducts no probable cause inquiry and does not review the targeting of particular individuals; instead, Section 702 requires that the court determine whether a certification contains all the statutorily required elements and that the targeting and minimization procedures to be used with the acquisition are consistent with Section 702’s statutory requirements and with the Fourth Amendment to the Constitution. 50 U.S.C. § 1881a(i)(3). If these standards are met to the FISC’s satisfaction, the court issues an order approving the certification.[5]
Once the FISC has entered an order approving the certification, the government conducts the acquisition by directing the assistance of an “electronic communication service provider.”[6] Congress clearly contemplated that, notwithstanding the foreign focus of the targets of Section 702 surveillance, the acquisition of communications under Section 702 would occur in the United States, and the statute specifically provides that the Attorney General and the DNI, in conjunction with authorizing an acquisition pursuant to Section 702, may direct an electronic communication service provider to immediately provide the government with all information, facilities, or assistance necessary to accomplish the acquisition in a manner that will protect the secrecy of the acquisition while producing minimum interference with the provider’s service to the target. 50 U.S.C. § 1881a(h)(1)(A).[7]
The Operation of Section 702 in Practice
Acquisition
Once a certification is approved, the government proceeds to target those non-U.S. persons reasonably believed to be located outside the United States who are within the scope of the certification to acquire foreign intelligence information. Section 702 certifications permit non-U.S. persons to be targeted only through the “tasking” of “selectors.” Selectors are neither key words (e.g., “weapon” or “nuclear”) nor individual names of targeted individuals because these terms would not identify specific communications facilities; instead, a selector is a specific communication facility used by a target, such as the target’s email address or telephone number. In the patois of Section 702 collection, people are “targets,” and “selectors” are “tasked.”[8]
The NSA develops a proposed “target” based on “lead” information used by its analysts to determine whether the proposed target is likely to communicate foreign intelligence information as designated in an approved certification. The analyst then proceeds further to conduct a “due diligence” examination of the circumstances relevant to the determination of whether, in fact, the potential target is a non-U.S. person reasonably believed to be located abroad.[9] This “foreignness” test “is not a ‘51% – 49% determination,’” but makes use of multiple information sources and comes to a conclusion regarding the location of the target based on the totality of the circumstances.[10] Analysts are required under the NSA Targeting Procedures to prepare “tasking sheets” citing the specific documents and communications that lead them to the conclusion that the target is outside the United States.[11] As the Privacy and Civil Liberties Oversight Board (PCLOB) reported, the practical effect of these procedures is a requirement that analysts “show their work” with respect to assessing the location of the target.[12]
In its 2014 report on the Section 702 Program, the PCLOB cited to a 2013 review conducted by the Department of Justice (DoJ) designed to assess how often NSA’s “foreignness” conclusions made under its targeting procedures turned out to be incorrect.[13] The review assessed a year of data and showed that only 0.4% of those targeting decisions resulted in the tasking of a selector where, as of the date of that tasking, the user was a U.S. person or was located in the United States.[14] Stated differently, the DoJ review concluded that 99.6% of the selectors that NSA had tasked did not have users who were U.S. persons or were located in the United States. On those very rare occasions where the NSA subsequently determines, as part of its internal post-targeting analysis, that a target has entered the United States or that a target initially believed to be a non-U.S. person is, based upon further review and information, actually a U.S. person, NSA targeting procedures mandate that the selector(s) associated with that target be “detasked” and that the acquisition from that target terminate without delay.[15]
Section 702 surveillance is predicated upon acquiring foreign intelligence information. Thus, in addition to assessing the “foreignness” of the target, the NSA’s targeting procedures also require confirmation, again based on the totality of the circumstances considering all information available to the analyst, that every selector used with a target will likely acquire a type of foreign intelligence information identified in an approved Section 702 certification (the “foreign intelligence purpose” test).[16]
For each selector associated with a target, then, the NSA uses a multi-step process that documents: the foreign intelligence that is expected to be acquired from the selector; the information upon which a reasonable person would conclude that the selector is used by a non-U.S. person; and, the information upon which a reasonable person also would conclude that this non-U.S. person is located outside the United States.[17] Once approved, the selector is provided to an electronic communication service provider, which is directed to provide the communications associated with that selector.
The NSA receives information concerning a tasked selector through two distinct forms of collection. One, the PRISM program,[18] has selectors furnished for tasking to electronic communication service providers (such as internet service providers (“ISPs”) like Google, Microsoft, and Yahoo) by the FBI, with the resultant communications sent to or received from the selector(s) then being provided to the NSA.[19] The NSA receives all data collected through PRISM collection.[20] In terms of volume, as of mid-2011, for example, 91 percent of the internet communications that the NSA acquired in any year were estimated to be obtained through PRISM collection.[21] The PCLOB Report offers the following example of PRISM collection in practice:
NSA learns that John Target, a non-U.S. person located outside the United States, uses the email address “[email protected]” to communicate with associates about his efforts to engage in international terrorism. The NSA applies its targeting procedures (described below) and “tasks” [email protected] to Section 702 acquisition for the purpose of acquiring information about John Target’s involvement in international terrorism. The FBI would then contact USA-ISP Company (a company that has previously been sent a Section 702 directive) and instruct USA-ISP Company to provide the government all communications to or from email address [email protected]. The acquisition continues until the government “detasks” [email protected].[22]
PRISM collection is limited to internet communications, does not include telephone collection, and, in the opinion of the PCLOB as reflected in its 2014 Report, “is clearly authorized by the [FAA] statute.”[23]
The second form of collection conducted in the Section 702 Program is termed “Upstream” collection. Only the NSA conducts Upstream collection,[24] and Upstream and PRISM acquisitions differ in several respects. In Upstream collection, the NSA collects both telephone and internet communications and the acquisition is conducted by directives ordering the assistance of those electronic communication service providers that control the telecommunications “backbone” over which both telephone and internet communications transit. The Upstream yield is substantial: for example, in the first six months of 2011, the NSA acquired more than 13.25 million internet transactions (or roughly 9% of its total Section 702 internet communication collection) through its Upstream collection.[25]
The volume is a reflection of the locus of acquisition. The internet is comprised of interconnected networks that allow computers to communicate. A “gateway” functions as the entrance point from one network to another and possesses the digital dexterity to convert internet protocols with different formats. Thus, gateways, which determine the flow of information, are essential features in most routers that otherwise would be limited to networks using similar protocols. “Cable heads” include the computer systems and databases needed for internet access while including cable modem termination systems that allow for the sending and receiving of signals on a cable network. When tasked selectors are used to acquire communications from these elements of the internet infrastructure, the level of content available for collection increases exponentially over what would be available from a single telephone line or a discrete computer address.[26]
Until recently, Upstream internet acquisition included two other features not present in PRISM collection: the acquisition of both “about” communications[27] and multiple communication transactions (MCTs). However, in April 2017, the NSA announced that it would no longer collect “about” communications.[28] This curtailment has removed a feature of the Section 702 program that was both once a source of concern to the FISC and the focus of considerable fire from critics of the Section 702 Program.[29]
Communications transit the internet as packets of data that together may be assembled and understood by a device on the internet and, where applicable, rendered in an intelligible form to the user of that device.[30] The packets forming a particular internet “transaction” may be reassembled as a single discrete communication or as an MCT containing more than one discrete communication within it.[31] Technologically, the NSA’s Upstream Internet collection devices are generally incapable of distinguishing between the individual communications comprising these MCTs, a task rendered more problematic as evolving technology sees internet service providers constantly changing their protocols and services to afford consumers the ability to customize how they use a particular service.[32] In its Upstream internet collection, the NSA specifically uses an Internet Protocol filter designed to at least “limit such acquisitions to internet transactions that originate and/or terminate outside the United States;”[33] but, if one of the communications within an MCT is to or from a tasked selector, and one end of the transaction is foreign, the NSA will acquire the entire MCT. Based on a statistical sample conducted by NSA in connection with proceedings before the FISC in 2011, NSA acquired between 300,000 and 400,000 MCTS where the “active user” (i.e., the actual human being interacting with a server to engage in an Internet transaction) was the target of the surveillance.[34]
Under NSA’s current minimization procedures, if a communication contained within an MCT is determined to be a domestic communication, the entire MCT will be destroyed unless the NSA’s Director (or Acting Director) specifically determines, on a communication-by-communication basis, that the sender or intended recipient was properly targeted under Section 702 and that certain specific retention criteria are satisfied.[35]
Use, Retention, and Dissemination
Once a communication is properly acquired pursuant to Section 702, it is processed and retained in multiple NSA systems and data repositories subject to multiple requirements designed to sustain protections for U.S. persons throughout the collection to dissemination process.[36] NSA analysts access Section 702 communications via “queries,” which may be date-bound, and may include alphanumeric strings such as telephone numbers, email addresses, or terms that can be used individually or in combination with one another.[37] NSA analysts with access to Section 702-derived data are trained in proper query construction so that the query “is reasonably likely to return valid foreign intelligence information and minimizes the likelihood of returning non-pertinent U.S. person information.”[38] Analysts conduct, at times, complex queries across large data sets, but in every instance, the queries must be constructed in a manner “reasonably likely to return foreign intelligence information.”[39]
Any use of U.S. person identifiers as terms to identify and select communications must first be approved in accordance with NSA minimization procedures that require a stated justification providing facts demonstrating that the use of the identifier is reasonably likely to return foreign intelligence information.[40] The request is then subject to multiple levels of review before approval to use a U.S. person identifier in a query.[41] The NSA retains records of all U.S. person identifiers approved for use as selection terms, and these records are subject to both internal review and external bimonthly audit by the DoJ’s National Security Division (“DoJ/NSD”) and the Office of the DNI (“ODNI”).[42] Compliance issues regarding the use of U.S. person identifiers must be reported to the FISC and to Congress.[43]
The NSA’s Minimization Procedures require that any communication determined to be clearly not relevant to the purpose of the acquisition or clearly not evidence of a crime be destroyed at the earliest practical time, and that under no circumstances will any communication of or concerning a U.S. person be retained for a period of more than five years.[44] As noted above, except in very limited circumstances, domestic communications (i.e., any communication lacking at least one communicant who is outside the United States) are destroyed upon recognition.[45] Even foreign communications of or concerning a U.S. person may be retained, used, and disseminated only for limited purposes specifically detailed in the NSA’s minimization procedures that must be approved by the FISC.[46]
Special retention rules govern MCTs acquired through the Upstream internet collection. No MCT acquired after March 18, 2017 may be retained unless at least one discrete communication within the MCT meets the NSA’s retention standards, and any MCT failing to meet the retention standards and containing communications of or concerning a U.S. person must be destroyed on recognition.[47]
Other than as noted above, unminimized Section 702-acquired data must be aged off NSA systems no later than five years after the expiration of the Section 702 certification under which it was acquired; however, internet transactions acquired through NSA’s Upstream collection techniques may not be retained longer than two years after the expiration of the Section 702 certification under which it was acquired unless at least one discrete communication meets the retention standards (i.e., is a foreign communication containing foreign intelligence information).[48]
The NSA only generates signals intelligence reports when the reported information meets a specific intelligence requirement, regardless of whether the proposed report contains U.S. person information. Dissemination of information about U.S. persons in any NSA foreign intelligence report is expressly prohibited unless that information is necessary to understand foreign intelligence information, assess the importance of that information, contains evidence of a crime, or indicates an imminent threat of serious harm to life or property.[49] Where dissemination is permitted, the identity of the U.S. person is “masked” and a generic term, such as “U.S. person,” is substituted along with suppression of details that could lead to such person being successfully identified by the context.[50] “Unmasking” of the U.S. person is permitted only where specific criteria are satisfied, where additional controls are in place to preclude further dissemination, and additional approval has been provided by one of seven designated positions at NSA.[51]
Oversight
Every feature of the Section 702 Program is subject to a plethora of oversight regimens and reporting requirements. The oversight begins internally at the NSA where the Director of Compliance, the Director of Civil Liberties and Privacy, the Inspector General, the General Counsel, and embedded compliance elements within the NSA’s operational directorates join in an enterprise-wide compliance structure.[52] Any compliance incidents, whether in the form of inappropriate queries, database errors, or typographical mistakes are reported to DoJ/NSD and the ODNI.[53]
Additionally, as required by statute,[54] the NSA completes and delivers to the congressional intelligence and judiciary committees an annual review of the Section 702 Program detailing: (i) an accounting of the number of intelligence reports containing reference to a U.S. person identity; (ii) an accounting of the number of U.S. person identities subsequently disseminated in response to identity requests relating to intelligence reports where the identity was initially masked; (iii) the number of targets that were later determined to be in the United States; and, (iv) a description of any procedure developed by NSA and approved by the DNI to assess, consistent with privacy rights and with national security and operational needs, the extent to which acquisitions authorized under the Section 702 Program acquire the communications of U.S. persons.[55]
As noted earlier, the NSA is required to document on “tasking sheets” every targeting decision made under its targeting procedures, and DoJ/NSD conducts post-tasking review of every tasking sheet furnished by the NSA.[56] Additionally, DoJ/NSD and ODNI conduct bi-monthly reviews of the NSA’s application of its minimization procedures focusing particularly on dissemination and queries using U.S. person identifiers.[57] The results of these targeting and minimization reviews are reported to Congress both in the NSA’s annual review[58] and in the Joint Assessments that also are furnished to the FISC.[59]
All of the foregoing represents an ongoing compliance scheme documented in a recurring series of detailed reporting requirements. Aside from this oversight regimen, after an independent, exhaustive and comprehensive review conducted pursuant to both presidential and bipartisan congressional requests, the PCLOB concluded that “the Board has seen no trace of any such illegitimate activity associated with the [Section 702] program, or any attempt to intentionally circumvent its limits.”[60] Correspondingly, fifteen separate Joint Assessments have concluded there have been no incidents of intentional circumvention of or violation of the procedures or guidelines governing the Section 702 Program.[61]
A Statistical Snapshot of Section 702 Activity
Having examined how Section 702 collection authority is practiced (largely by the NSA), some statistical data helps illustrate the quantitative scope of that application which, in turn, may offer an order of magnitude from which to evaluate the criticism of the Program leveled by its detractors.[62]
Much of the numerical data associated with the Section 702 Program remains classified, but some range of its scope can be gauged from a FISC opinion authored by Judge John Bates in October 2011 and subsequently released in redacted form.[63] In his October 2011 opinion, Judge Bates estimated that NSA acquires more than 250 million communications each year pursuant to Section 702.[64] Roughly 91% of this collection was PRISM collection, while the remaining 9% constituted acquisitions from the NSA’s Upstream collection.[65] In 2011, roughly 60% of this Upstream collection represented MCTs with the remaining 40% constituting discrete (i.e., single) communication transactions (“SCTs”).[66]
Although constituting a statistically smaller part of the overall collection, the Upstream program in 2011 was still acquiring more than 26 million internet transactions per year.[67] These included both SCTs and MCTs. As discussed earlier, MCTs include multiple discrete communications in a single transaction and, in 2011, the NSA was collecting 300,000-400,000 MCTs per year where the active user was the user of the tasked facility. Moreover, according to Judge Bates, the NSA’s Upstream collection resulted in the acquisition of “tens of thousands of wholly domestic communications.”[68]
More recently, in accordance with certain requirements imposed by the USA Freedom Act,[69] the ODNI released its Annual Statistical Transparency Report. While the report does not provide the sort of collection numbers cited by Judge Bates in his October 2011 FISC opinion, it furnished the following data regarding the number of Section 702 targets authorized pursuant to orders issued by the FISC following review of Section 702 certifications:[70]
Moreover, reflecting the continuing expansion in telecommunication connectivity, as of November 2016, Section 702 taskings were reported to have steadily increased in all but two of the fifteen reporting periods covered by the semiannual joint assessments provided to Congress by the Attorney General and the Director of National Intelligence, including a 14% increase in new taskings during the reporting period covered by the November 2016 Joint Assessment.[71] Corresponding with the rise in targeting and tasking, the use of U.S. person identifiers increased with the ODNI Transparency Report showing that, in CY 2016, an estimated 5,288 search terms concerning a known U.S. person were used to retrieve unminimized contents of communications acquired under Section 702, as compared to 4,672 such uses in CY 2015.[72]
While these figures are insufficient to fully portray the scope of the Section 702 Program or assess its impact with any great degree of specificity, they do furnish some quantitative order of magnitude regarding its operation.
Read the first part of the series here. The third part of the series will be published next week.
About the author:
*George W. Croner previously served as principal litigation counsel in the Office of General Counsel at the National Security Agency. He is also a retired director and shareholder of the law firm of Kohn, Swift & Graf, P.C., where he remains Of Counsel, and is a member of the Association of Former Intelligence Officers.
Source:
This article was published by FPRI. This article is the second part of a four part series arguing for the renewal of the FISA Amendments Act originally enacted in 2008, extended in 2012, and now set to expire on December 31, 2017. The first part of the series was published can be accessed here. Part three will be published next week.
Notes:
[1] 50 U.S.C. § 1881a(a).
[2] 50 U.S.C. § 1881a(b)(5).
[3] Because NSA and the FBI are the only agencies authorized to engage in targeting to acquire communications pursuant to Section 702, these are the only agencies with targeting procedures. However, given that NSA is the only agency authorized to initiate Section 702 collection and that FBI targeting procedures are applied only to certain selectors that NSA already has determined as appropriate for targeting under NSA’s targeting procedures, this paper focuses on NSA’s targeting and minimization procedures in its discussion of the Section 702 Program. See PCLOB Report at 42 (“only the NSA may initiate Section 702 collection”).
[4] 50 U.S.C.§ 1881a(g)(2)(A).
[5] See, e.g., Memorandum Opinion and Order, [Caption Redacted], [Docket No. Redacted], (FISC April 26, 2017) (Collyer, J.) at http://icontherecord.tumblr.com (approving certification, targeting procedures and minimization procedures).
[6] “Electronic communication service provider” is defined in the FAA, and includes, by reference to other definitions found in the U.S. Code, a telecommunications carrier, a provider of electronic communication service, a provider of remote computing service, and “any other communication service provider who has access to wire or electronic communications either as such communications are transmitted or as such communications are stored.” 50 U.S.C. § 1881(b)(4).
As noted earlier, one of the hurdles to passage of the FAA had been the issue of immunity for electronic communication service providers that had provided services to the government in connection with the TSP and subsequently had been sued for such participation. Congress granted retroactive immunity to these providers and, prospectively, provided: (1) that electronic communication service providers furnishing information, facilities, or assistance in accordance with [a Section 702 directive] would be compensated at prevailing rates; and (2) that “no cause of action shall lie in any court against any electronic communication service provider for providing any information, facilities, or assistance in accordance with a [Section 702 directive].” 50 U.S.C. § 1881a(h)(1-3).
[7] The FAA permits an electronic communication service provider to petition the FISC to modify or set aside the directive ordering its assistance. 50 U.S.C. § 1881a(h)(4). If the FISC does not provide the requested relief, the electronic communication service provider may appeal to the FISCR and, ultimately, seek certiorari review by the U.S. Supreme Court. See, e.g., In re Directives Pursuant to Section 105B of the Foreign Intelligence Surveillance Act, 551 F.3d 1004 (FISCR 2008) (FISCR rejects provider’s challenge that the directed assistance violated customers’ Fourth Amendment rights).
[8] NSA Director of Civil Liberties and Privacy Office, “NSA’s Implementation of Foreign Intelligence Surveillance Act Section 702” (“DCLPO Report”) (April 16, 2014) at 2-3, 5; PCLOB Report at 21, 32.
[9] See PCLOB Report at 43 (“The government has stated that in making this foreignness determination the NSA targeting procedures inherently impose a requirement that analysts conduct ‘due diligence’ in identifying these relevant circumstances.”).
[10] DCLPO Report at 4. See PCLOB Report at 44 (“The government has stated, and the Board’s review has confirmed, that this is not a’51% to 49%’ test.”). See also Procedures Used by the National Security Agency for Targeting Non-United States Persons Reasonably Believed to be Located Outside the United States to Acquire Foreign Intelligence Information Pursuant to Section 702 of the Foreign Intelligence Surveillance Act of 1978, as Amended (“2016 NSA Targeting Procedures”) at 1-2 (“NSA may use information from any one or a combination of these categories of information in evaluating the totality of the circumstances to determine that the potential target is located outside the United States.”).
[11] PCLOB Report at 45; DCLPO Report at 4-5.
[12] PCLOB Report at 45.
[13] PCLOB Report at 44.
[14] Id.
[15] 2016 NSA Targeting Procedures at 7-9; DCLPO Report at 4.
[16] 2016 NSA Targeting Procedures at 4; DCLPO Report at 4.
[17] DCLPO Report at 4-5.
[18] NSA now refers to PRISM collection as “Downstream” collection. NSA/CSS Press Statement, NSA Stops Certain Section 702 “Upstream” Activities, April 28, 2017. For ease of reference, this paper uses the PRISM descriptor historically applied to this form of Section 702 collection.
[19] DCLPO Report at 5; PCLOB Report at 33-34.
[20] PCLOB Report at 7, 33-34.
[21] Id. citing Bates October 2011 Op., 2011 WL 10945618, at *25 and n. 24.
[22] PCLOB Report at 34.
[23] PCLOB Report at 9.
[24] PCLOB Report at 7.
[25] Bates October 2011 Op., 2011 WL 10945618, at *10, n. 26.
[26] This description of Internet structure draws on that provided in Laura K. Donohue, Section 702 and the Collection of International Telephone and Internet Content, 38 Harv.J.L. & Pub. Pol’y 117, 132 (2015).
[27] In Section 702 parlance, an “about” communication is one that includes the tasked email address in the text or body of an email even though the email is between two persons who are not themselves targets. In the case of “about” communications, acquisition may include communications that are neither to nor from a target but, instead, where a particular selector tasked for collection happens to be included in the communication.
[28] NSA/CSS Press Statement, NSA Stops Certain Section 702 “Upstream” Activities, April 28, 2017.
[29] NSA’s 2016 Minimization Procedures reflect this change in the handling of “about” communications by requiring all such communications acquired prior to March 18, 2017 to be segregated until destroyed and all such communications acquired on or after March 18, 2017 to be “destroyed upon recognition.” Minimization Procedures Used by the National Security Agency in Connection with Acquisitions of Foreign Intelligence Information Pursuant to Section 702 of Foreign Intelligence Surveillance Act of 1978, as Amended (“2016 NSA Minimization Procedures”) at 4.
[30] See Bates October 2011 Op., 2011 WL 10945618, at *9, n. 23 (quoting the government’s characterization of what constitutes an Internet transaction).
[31] 2016 NSA Minimization Procedures at 2.
[32] Bates October 2011 Op., 2011 WL 10945618, at *10; PCLOB Report at 40.
[33] 2016 NSA Targeting Procedures at 2.
[34] PCLOB Report at 40 citing to Bates October 2011 Op., 2011 WL 10945618, at *12.
[35] 2016 NSA Minimization Procedures at 9.
[36] See, e.g., U.S. Signals Intelligence Directive (“USSID”) 18 (titled Legal Compliance and U.S. Persons Minimization Procedures, USSID 18 “prescribes policies and procedures and assigns responsibilities to ensure that the missions and functions of the U.S. SIGINT System are conducted in a manner that safeguards the constitutional rights of U.S. persons.”).
[37] DCLPO Report at 6.
[38] DCLPO Report at 6-7.
[39] 2016 NSA Minimization Procedures at 4.
[40] 2016 NSA Minimization Procedures at 5; DCLPO Report at 7.
[41] Id.
[42] 2016 NSA Minimization Procedures at 5; PCLOB Report at 57.
[43] See FISC Rule of Procedure 13(b) requiring notification of non-compliance (which would include noncompliance with minimization procedures approved by the FISC). See also 50 U.S.C. § 1881a(l)(1) (Attorney General and DNI required to submit semiannual compliance reports to Congress and the FISC).
[44] 2016 NSA Minimization Procedures at 4.
[45] Id. at 9.
[46] 2016 NSA Minimization Procedures at 11-13..
[47] Id. at 5.
[48] 2016 NSA Minimization Procedures at 5.
[49] DCLPO Report at 7; 2016 NSA Minimization Procedures at 10-11.
[50] DCLPO Report at 7; 2016 NSA Minimization Procedures at 12.
[51] DCLPO Report at 7-8; 2016 NSA Minimization Procedures at 12-13.
[52] DCLPO Report at 9.
[53] Id.
[54] 50 U.S.C. § 1881a(l)(3).
[55] 50 U.S.C. § 1881a(l)(3)(A).
[56] PCLOB Report at 70; Semiannual Assessment of Compliance with Procedures and Guidelines Issued Pursuant to Section 702 of the Foreign Intelligence Surveillance Act, Submitted by the Attorney General and the Director of National Intelligence, November 2016 (covering the period June 1, 2015 – November 30, 2015) (“November 2016 Joint Assessment”) at 7.
[57] PCLOB Report at 72; November 2016 Joint Assessment at 8.
[58] 50 U.S.C. § 1881a(l)(3)(A).
[59] 50 U.S.C. § 1881a(l)(1).
[60] PCLOB Report at 11.
[61] Office of the Director of National Intelligence “Fact Sheet” relating to the “Semiannual Assessment of Compliance with Procedures and Guidelines Issued Pursuant to Section 702 of the Foreign Intelligence Surveillance Act (FISA) – 13th, 14th and 15th Joint Assessments” at 1 available at www.dni.gov//Overview_Fact_Sheet.
[62] This statistical picture is, admittedly, incomplete since quantification of significant features of the Section 702 Program remains classified.
[63] Certain provisions in The USA Freedom Act, P.L. 114-23 (2015), now provide for release, in certain circumstances, of redacted decisions of the FISC. A mix of other statutory requirements in the USA Freedom Act also requires the DNI to provide certain statistical data on the use of national security authorities like Section 702.
[64] Bates October 2011 Op., 2011 WL 10945618, at *9.
[65] Id.
[66] Id. at *25.
[67] Id. at *10.
[68] Id. at *16.
[69] See, Note 86, above.
[70] Statistical Transparency Report Regarding Use of National Security Authorities for Calendar Year 2016 (“Transparency Report”), Office of the Director of National Intelligence, April 2017 available at www.dni.gov.
[71] November 2016 Joint Assessment at 16-18.
[72] The search term data is not broken down by agency so it is not possible to determine which agency is utilizing search terms concerning U.S. persons, or how frequently. The PCLOB Report indicates that, in 2013, NSA approved 198 U.S. person identifiers to be used as content query terms while CIA conducted approximately 1,900 content queries using U.S. person identifiers. PCLOB Report at 57-58.